GRIT Ransomware Report: October 2023
Additional contributors to this report: Nic Finn, Justin Timothy
October proved to be much quieter than expected. Compared to the massive month of September 2023, where threat actors posted 495 victims, October represents a significant cooling off with a 32% reduction in victims month over month. Despite the slowdown this month, October’s victim counts still dwarf those from the beginning of 2023. This likely short-term reduction is mostly indicative of just how busy ransomware groups were in Q3. Despite the smaller pool of victims, the number of active ransomware groups has not significantly changed, with many of the larger Established groups showing stability while the smaller Ephemeral and Emerging actors demonstrate staying power.
As conflict explodes across the Middle East, several actors have publicized their allegiance and desires to hack to support their side. Nationalized hacktivism typically manifests as DDoS attacks or website defacements but there remains the possibility of ransomware actors adjusting their victimology towards one side of the conflict. It is likely too early in these operations for these changes to be reflected in the data as the countries most impacted by ransomware remain the United States, Canada, and the UK.
The Manufacturing industry maintained its spot on the top of the list of most impacted industries. Healthcare, Education, Retail, and Consulting round out the top of this list with all three showing significant growth in the past several months. The Healthcare and Education sectors continue to be targeted by threat actors willing to leak sensitive personal data as a part of the extortion process. The Retail and Wholesale industry has had a noticeable increase in posted victims in recent months, a trend we assess as likely to continue as holiday shopping represents a busy and sensitive time of year for retailers.
While October included the return of Clop and the appearance of a handful of Emerging and Ephemeral groups, our threat actor spotlight this month highlights the work of the consistently growing ransomware group “NoEscape.” NoEscape, which GRIT assesses as a Rebrand group, emerged in May of 2023 and has evolved into a formidable threat.
| Total Publicly Posted Ransomware Victims | 337 |
| Number of Active Ransomware Groups | 35 |
| Average Posting Rate (per day) | 10.9 |
Ransomware Trends
As mentioned previously, October was slower than previous months, with 22 of the 35 active groups showing a decline in postings compared to September 2023.
In particular, Ransomed dropped 72% from 44 victims claimed in September to 12 in October. The second largest decrease came from Cactus, dropping 85% from 33 September victim posts to five in October. In total, among the 13 groups with observed declines in October, we observed an average decline of 10.6 posts compared to the previous month.
GRIT observed three days with spikes in activity, two predominantly the result of mass posts from Play, and another mass post on Oct 31st by NoEscape. Play’s activity suggests a process of manually posting victims to their leak site, with 42 victims posted across only nine days.
While this decrease is significant, total observed ransomware posts still far exceed those observed in October 2022, indicating ransomware activity is still trending upward as observed in our previous reports.

Ransomware Victims by Country
Although the US is still the most impacted nation by victim count, posts from the US decreased by 83 from September to October, resulting in 164 total victims, 21 victims less than the monthly average throughout 2023 (184).
Germany saw a massive 76% decline in victim count from September to October, resulting in four total October victims, compared to
15 per month on average throughout 2023.
In contrast, the UK saw 33 total victim posts, 10 more (43%) than their average across 2023, aligning with the trend observed in our Q3 ransomware report, in which we saw a 40% increase from Q2 to Q3.
Iran was a standout this month, with October representing their second-highest monthly total in 2023 at five total victims. In August, they experienced 10 total victim postings. These are primarily the result of posts from Arvinclub, responsible for 70% of all observed Iranian victims and 100% of the Iranian victims posted in October.


Industry Trends

Manufacturing was once again the most targeted industry, with 49 victims. This doubles Retail and Wholesale, who came in second with 23 victims, marking its first appearance in the top five industries since it last appeared at number four in July. Among the most heavily attacked countries, the most impacted industries saw little deviation from the norm. Manufacturing remained in the top spot, but the Legal and Education industries saw a slight fall in victims. After a recovery in September, the Technology industry saw a sharp decline in victims month over month, reporting 17 in October versus 32 in September–a 47% decrease following a downward trend outlined in August’s report. The Manufacturing industry was most heavily impacted by LockBit and Play, which accounted for 35% of the industry’s victims.
While Lockbit typically tops the list of every industry in the top 10, Retail and Wholesale is mostly driven by Play and NoEscape. Consulting, at number five on this list, was only impacted by Lockbit twice this quarter.
Ransomware groups continue to regularly target the sensitive Education and Healthcare verticals, accounting for 47 total victims this month. This is slightly down from September, when 55 victims were posted in these two industries. A slight but notable decrease of 14% month over month.
Threat Actor Trends
Despite having the highest number of reported victims, LockBit’s October count (65) was far below (24%) their average monthly count in 2023 (85). Excluding Clop during their mass exploitation of MoveIT, LockBit has maintained the most prolific ransomware group every month since July 2021.
Play’s reported victims in October (42) are nearly twice their next highest from previous months, 27 in June and September, and more than twice their average monthly victim count in 2023 (20)
NoEscape has seen an increase of victims month after month since their emergence in June, with average increases in posts of more than 20% each month. October’s victims (31) saw an almost 50% increase from September (22).


Threat Actor Spotlight: NoEscape (Rebrand)

NoEscape is a ransomware-as-a-service group that began publicly posting victims during June 2023. Although they are relatively new to the ransomware ecosystem, the group has been consistently accruing between 15 to 20 victims each month and is within the top 10 most active groups since June 2023 based on the number of victims posted to their data leak website.
NoEscape is a Rebrand of the terminated group, Avaddon. Avaddon ceased operations in June of 2021 after publicly releasing decryption keys for their victims. NoEscape has been tied to Avaddon due to their encyptors being nearly identical with only minor changes. It is possible that the actors behind NoEscape simply purchased Avaddon’s encryptor, but algorithm changes made within the encryptor suggest that it is more likely that NoEscape is a true Rebrand. If the group continues to progress and becomes a mainstay in the ransomware ecosystem, they will be classified as an Established group.
Although not unique to NoEscape, one aspect that makes the group stand out from its ransomware competitors is that they claim to partake in triple extortion tactics. Along with encrypting and stealing data from victims, the group also conducts Distributed Denial of Service (DDoS) attacks against those victims. This is denoted on their data leak site, where certain victim posts contain a “DDOS” icon in the listing. While some ransomware groups may have an ad hoc policy dependent on the affiliate to conduct DDoS attacks, NoEscape’s DDoS attacks as a service offering can imply that the group is more structured and organized than others.
NoEscape may have taken heavy inspiration from LockBit in terms of their data leak site features and design. Both sites share a similar “Card” based layout, with listings contained within blocks on the site’s homepage and a brief description of the victim. NoEscape’s site showcases countdown timers on victim posts, denoting when the post will be updated with leaked data, and viewer counts to keep track of how many users have viewed a listing, both of which are also evident on LockBit’s site. Both sites also contain a link to “X”(Twitter) which directs users to a search for posts for the respective ransomware group. Lastly, both sites contain a “Contact Us” form that also instructs users to utilize Tox for communication with the threat actors. Throughout 2023, LockBit has been the most successful ransomware group, which may be why smaller and upcoming groups would mimic their data leak site in hopes of achieving the same success. There have not been any other definitive connections made yet between NoEscape and LockBit, but with the success that NoEscape has seen for a relatively new group, there is potential for overlap between the two.
Like most ransomware operations, the group disproportionately affects victims in the United States. Of the group’s 92 victims claimed since the GRIT began tracking the group, 25 have been located in the US. The group’s most impacted industry sector is Retail and Wholesale, with Manufacturing being a close second. The group does not shy away from victimizing organizations within the Healthcare and Education sectors, which are commonly taboo among ransomware groups.
Other Notable Ransomware Events
Alphv’s “AffilliatePlus”
The Established group Alphv has created a new program for their affiliates titled “AffiliatePlus.” Security researchers have reported that the program is only available to those whose total ransom payments exceed $1.5 million. Features of this program include access to a custom Linux-based operating system dubbed “Munchkin.” Munchkin contains tools that allow attackers to easily deploy Alphv’s “Sphynx” encryptor, as well as locking Secure Message Block (SMB) and Common Internet File System (CIFS) shares. It comes prepackaged with the virtualization software VirtualBox so operators can safely run the OS on a compromised device. The feature set of the operating system puts it adjacent to Kali Linux in functionality but attempts to be a lighter-weight, stripped-down alternative to the popular offense-focused distribution. The group claims that the feature list of Munchkin will expand in due time. This program developed by Alphv may be mirrored by other Established groups, whether formally like this program or informally in terms of preferential treatment for the most active affiliates. This plan incentivizes affiliates to remain loyal to one group and rewards them for continued work.
Lockbit tries out a new Coercive Tactic
First posted by the group on October 2nd, Lockbit claims to have victimized the Relocation Services company Sirva Worldwide. After allegedly not paying the ransom, Sirva became the target of a social media campaign by the group, hosted on the social media platform X. On X, several newly created accounts began posting and reposting a message to the company urging them to reconsider paying the group. Taking to social media channels to apply pressure to extortion victims is not a new tactic; however, these messages were notable in that they appear to have been artificially inflated via purchased interactions. X, like many social media platforms, surfaces popular content to users by favoring posts with more interactions from other users. Many of the posts created as a part of this particular extortion campaign have hundreds of replies, likes, and retweets from bot accounts with very few coming from verifiably real users. It is very likely the threat actors purchased these interactions via one of many gray area social media marketing services to signal boost their threats to the victim.
The Return of Clop
After completing one of the largest-scale mass exploitation attacks by a ransomware group in their MoveIT campaign, GRIT and other security researchers predicted Clop would have a period of less activity as the group recovers and regroups. A lengthy 50-day period of inactivity on the threat actor’s torrent-based leak site did occur but was suddenly broken when the group posted a new victim on October 20th and another five days later. At this time, it is unclear whether these new victims were exploited as a part of the MoveIT campaign. However, all indications point to a return to relatively normal operations by the Clop group. Before adopting their mass exploitation strategy, the group’s operations more closely mirrored a traditional ransomware group – a return to form would not be out of the question considering their capabilities.
Middle Eastern Conflict Ignites Hacktivism
With fighting once again erupting in Israel, threat actors on both sides of the conflict have pledged to engage their enemy online. Through DDoS attacks, data theft, and website defacement these actors attempt to influence the battlefield by targeting high-value targets with their operations. The individuals behind hacktivist groups perform attacks using their own knowledge while also recruiting other, less experienced hackers to support their cause. While the biggest names in the ransomware world have not yet pledged their allegiances, GRIT assesses that operators in the Middle East may adjust their targeting methodology in the coming months to advance their, or their country’s, geopolitical interests.
New Ransomware Groups Tracked by GRIT in October 2023:
Hunters International (Rebrand)

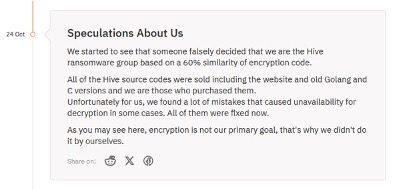
Towards the end of October, GRIT observed infrastructure for a new ransomware group, which included chat and data leak sites set up for extortion of victims. The group, calling themselves Hunters International, posted two victims in October. One of the posts claimed a victim in the Healthcare industry and included sensitive pictures and other personally identifiable information of patients. On review of the group’s ransomware encryptor, many researchers found similarities to the now defunct group, Hive, which was disrupted by law enforcement in January of 2023. This connection was explicitly denied by the threat actor in a post on their leak site, explaining that they had purchased the code for their encryptor and that they are new and unaffiliated with any other groups. Despite their insistence to the contrary, GRIT assesses Hunters International as a Rebrand – one to keep an eye on due to the perceived maturity of their infrastructure.
Final Thoughts
While the month of October has shown a significant reduction in ransomware victims reported month over month, 2023 is still on track to be the most prolific in ransomware history. Even more concerning than the upward trend in victimization is the continued innovation by threat actors in the field of coercive tactics. Threat actors, whether concerned over reduced payments or the degraded effectiveness of encryption operations, continue to try to find new ways to apply pressure to their victims post-breach. In the arms race between ransomware groups and the targets of their extortion, ultimately the biggest losers are the humans whose personal data is the subject of exposure and exploitation. While all groups are guilty of creating negative outcomes for their victims, Established groups have recently shown their willingness to cross many lines to turn up the pressure on their victims in the name of profit. From the publicly available data alone it is difficult to assess whether these individual escalations in tactics are leading to more frequent and larger payments for threat groups. However, groups like Alphv and Lockbit are no strangers to these tactics and consistently find themselves among the top performers.
Play and NoEscape were uncharacteristically busy this month, both rounding out October posting at their highest rate ever. The success of these and other groups in the Developing and Rebrand categories proves that the ransomware ecosystem is not overly centralized under the largest Ransomware as a Service operations.
There were many familiar faces among the top industries of the month. Manufacturing once again took the top spot, consistently a favorite target of ransomware groups. Sensitive industries like Healthcare and Education, unfortunately, continue to appear in the top five month-over-month. Shockingly, the Retail and Wholesale industry was heavily victimized in October with 23 reports in total. This can possibly be explained by another more subtle trend in escalating coercive actions – seasonality in targeting. In GRIT’s Q3 ransomware report, we assessed that the Entertainment, Hospitality, and Tourism industry received a bump in victimization during the summer months, likely as a result of threat actors understanding that the best time to strike any given company is when they are the busiest with operations. Perhaps the spike in activity in the Retail and Wholesale vertical this month is a leading indicator of threat actors targeting retailers during the pivotal holiday season.
All eyes are on the ransomware landscape as the last months of 2023 paint the picture for an extremely prolific year for ransomware operators. In previous years, GRIT observed a slight slowdown in posted victims in November and December, however, time will tell whether this trend will continue. As the ransomware economy expands, a newly increased baseline of activity may result in less of a drop-off during the usually quiet end of the year. Regardless of the trends and projections, defenders should be as on guard as ever because the threat of ransomware shows no signs of subsiding.
The GRIT Ransomware Taxonomy
By subdividing ransomware groups, GRIT can obtain more detailed insights into how ransomware groups progress in their level of operational maturity and can classify and identify potential rebranding activity.
We distinguish ransomware groups by placing them into these six categories:
EMERGING
This category is reserved for new ransomware groups within their first three months of operations. These organizations may be short-lived, resulting in an Ephemeral group; may be determined to have Splintered or Rebranded from an Established group; or may move on to further develop their operations and TTPs over time.
EPHEMERAL
These groups are short-lived, with varied but low victim rates. Observed victims are usually posted in a single or short series of large postings rather than a continuous flow over time. Ephemeral groups, by definition, terminate operations, spin-off, or rebrand within three months of formation. These groups may or may not have dedicated infrastructure (i.e., data leak sites and chat support) as part of their operations.
DEVELOPING
These groups have conducted operations for three months or longer, resulting in a recurring flow of victims. Developing groups do not appear to be directly linked to other ransomware groups as a Splinter or Rebrand but may include some experienced ransomware operators. Developing groups generally improve their people, processes, or technology over time by recruiting additional members, refining TTPs, or improving the quality of their associated ransomware and encryption. These groups generally have dedicated infrastructure (i.e., data leak sites and chat support) as part of their operations.
SPLINTER
These groups consist of a plurality of members from previously Developing or Established groups and may have formed either by choice or due to exclusion. These groups may be identified by very similar or overlapping TTPs and tooling or through HUMINT gathered through interactions with personas on the deep and dark web. Splinter groups differ from Rebrands by the continued existence of the original organization as the Splinter group operates.
REBRAND
These groups consist in whole, or in part, of former Developing or Established groups. Rebrands often maintain the same people, processes, and technology as the original group. Rebrands are generally undertaken in order to minimize attention from law enforcement or intelligence officials or to avoid negative publicity.
ESTABLISHED
These groups have operated successfully for at least nine months and have well-defined and consistent tactics, techniques, and procedures. Established groups often possess functional business units that enable sustained ransomware operations, with specialists focused on areas such as personnel, encryption, negotiations, etc. These organizations successfully employ technology and redundant infrastructure to support their operations.
There are multiple routes a group can take through the various classifications, and no one route is standard. While one group may begin as “Ephemeral” and move their way through the ranks to “Full-time,” another group may enter as a “Rebrand” as part of a larger obfuscation strategy to avoid attention from law enforcement.