EMAIL SECURITY CHALLENGES
How Are You Protecting Email From
Being Exploited?
The majority of attacks start with email because it targets the weakest link in your security chain: People.

293 days
to identify & contain a data breach by phishing
Ponemon Institute 2023 Cost of a Data Breach Report
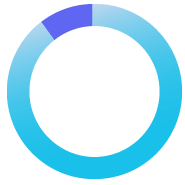
98%
of human-targeted attacks are delivered through email
2023 Verizon Data Breach and Investigations Report
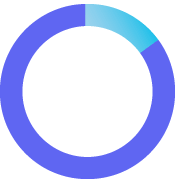
15%
phishing is the most common initial attack vector
Ponemon Institute 2023 Cost of a Data Breach Report
Our Email Security Commitment to You
We will help you improve your Email Security by:
- Ensuring the protection of email content and accounts from unauthorized access.
- Identifying areas of weakness against attacks such as phishing and providing meaningful remediation recommendations.
- Recommending the email security architecture and best-fit solutions to protect your organization—from inbound to outbound protection.
EMAIL SECURITY SERVICES
Results-Oriented Email Security Services
Explore our email security services:
Our experts understand the types of attacks that are carried out through email, as well as the different email security technologies and recommendations for setting up your environment in a secure manner.

Phishing Services
Our social engineers can develop customized phishing campaigns to ensure meaningful results with clear remediation steps.
EMAIL SECURITY OUTCOMES
Protect Your Email From Being Exploited by Phishing and Spear-phishing Campaigns
Our Email Security services are tailored to help you better defend against these types of social engineering attacks, identify the right tools and to set up your email environment in a secure manner.
Secure Your Weakest Link
Train your users to reduce the risk of being socially engineered.
Ensure Email Protection
Minimize the risk of email content and accounts from unauthorized access.
Why GuidePoint Security
Your Elite, Highly-trained Team
More than 50% of our workforce consists of tenured cybersecurity engineers, architects and consultants. We are also highly certified across industry standards as well as hundreds of cybersecurity solutions.
Highly Trained, Highly Certified
Examples Include:



Industry Certifications
Your Trusted Advisor
Our team works side-by-side with you as your cybersecurity partner.
“GuidePoint Security is basically family. They’re always there when I need them. At the end of the day GuidePoint is always there to help and that’s how they add value.”
Mark Gilman
Security Manager


