
Governance, Risk & Compliance Solutions
Ensure Your Infosec Program is Aligned with GRC Best Practices, Frameworks Regulations & Compliance Mandates
GRC CHALLENGES
How Are You Addressing Cyber Risk, Compliance and Business Resilience?
Organizations face persistent threats from advanced attackers, a rapidly expanding technology landscape, as well as complicated and evolving regulatory requirements. And yet many senior-level executives rank risk and compliance among the top two risk categories they feel least prepared to address.
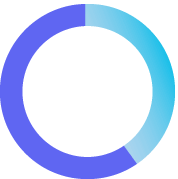
40%
of corporate risk & compliance professionals lack confidence to address compliance risks
2023 Thomson Reuters Risk & Compliance Survey Report
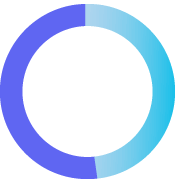
49%
of respondents said standardizing risk & compliance frameworks would reduce complexity & cost
2023 Thomson Reuters Risk & Compliance Survey Report
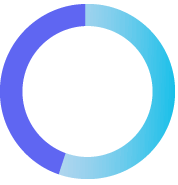
54%
of organizations reported experiencing a data breach caused by one of their third parties in the last 12 months
2022 Data Risk in the Third-Party Ecosystem Study
GOVERNANCE, RISK & COMPLIANCE PRACTICE
GRC Services Designed to Address Your Unique Needs
Our team of GRC practitioners and consultants helps organizations to plan, build and run mature security programs.
Whether it’s aligning with a specific industry framework or a bespoke security strategy, we help you to reduce cyber risk and enable your business.
We offer a robust set of capabilities across strategy, governance, third party and supply chain risk management, business resilience and compliance advisory services.
Our Governance, Risk & Compliance Commitment to You
We will help you raise the GRC bar by:
- Ensuring you have improved decision-making, optimized information security investments, centralized visibility across your environment and alignment with industry best practices, regulations and compliance mandates.
- Defining your organizational information security structure and strategy, creating a prioritized information security program roadmap and establishing, reviewing and updating security policies and procedures. Additionally, we can provide security leadership and direction through a virtual CISO advisory.
- Establishing a strategic risk management program built on a security framework to effectively manage and grow the program and ultimately allowing you to make faster, more risk-informed business decisions.
- Providing you with a clear understanding of your level of compliance, any gaps and how to shore them up, including an environment review and scope validation, conducting readiness assessments to determine areas of deficiency, reviewing and assessing your IT controls and providing formal compliance assessments and advisory services.
GRC SERVICES
The Guidance You Need to Develop or Enhance Your Information Security Program
Explore our GRC services:
With our help, you can be assured of improved decision-making, optimized information security investments, centralized visibility across your environment and alignment with industry best practices, regulations and compliance mandates.

Security Program
Review
Evaluate & measure your organization’s security program maturity, which can be based on a multitude of frameworks.

Data Security Governance
Aligning your data protection strategies with business objectives through expert assessments, program development, advisory and sensitive data scans.

Data
Privacy
Enhancing compliance and privacy maturity with tailored assessments, advisory, program development and strategic solutions.

ICS Security Program
Review
Designed to align your OT/ICS security strategy with your organization’s business goals – while managing security risk.

M&A
Security
Go beyond documentation review to evaluate your target company’s vulnerabilities & risk of being compromised by a cyber-attack.

Ransomware Readiness
Gain a broad, risk-based analysis of your organization’s ability to protect against ransomware & respond if victimized.

Third Party Risk Management
Understand & manage risk as it relates to the vendors in your supply chain.

Compliance Advisory
Services
Designed to keep you on top of the dynamic landscape for relevant regulatory & industry standards.

CMMC
Compliance
Ensure you’re prepared to address the new age of information security for the defense industrial base.

HIPAA
Compliance
Protect patient health information & compliance with HIPAA & other healthcare security regulations.

PCI DSS
Compliance
Ensure PCI DSS compliance obligations via advisory & assessment services, as well as formal audit & attestation.

FedRAMP
Advisory Services
Design and build your Cloud Service Offering to adhere to FedRAMP & StateRAMP compliance requirements.

Compliance Management as a Service
We manage your compliance program to ensure your organization stays on top of required activities & maintains the necessary data to support future compliance assessments.
GOVERNANCE, RISK & COMPLIANCE OUTCOMES
Align Information Security to Your Business Goals, Manage Risk & Ensure Compliance
Our GRC services help ensure your information security program is optimized to meet today’s complex cyber risks while aligning with industry best practices, regulations and compliance mandates.
Gain an Accurate View of Risk
Ensure visibility of risk & controls to make faster, more risk-informed decisions
Ensure Consistent Measurement
Gain robust risk & compliance measurements & insights into your environment
Enable Effective Compliance Programs
Address evolving regulations, technology advances & business needs
Reduce Your Assurance Cost
Proactively address third party risk, business resilience issues & security gaps
Why GuidePoint Security
Your Elite, Highly-trained Team
More than 50% of our workforce consists of tenured cybersecurity engineers, architects and consultants. We are also highly certified across industry standards as well as hundreds of cybersecurity solutions.
Highly Trained, Highly Certified
Examples Include:



SANS & ISC2



Offensive Security



Global Information Assurance & Frameworks
Your Trusted Advisor
Our team works side-by-side with you as your cybersecurity partner.
“GuidePoint took it on themselves to bring in their company experts to walk us through, put together a proposal and partner with us to improve our cyber maturity to improve our compliance. And so by listening and understanding and having the resources on staff with the expertise to bear, working in partnership to provide solutions that will benefit and help mature GPC’s security long term.”
Damian Apone
Global Security Program Director
Genuine Parts







