
Security Operations Center (SOC) Services
Unlock the Power of Your SOC to Gain Greater Visibility, Reduce the Time to Remediate Incidents & Improve Your Security Posture
SOC CHALLENGES
How are You Maximizing the Value from Your Existing SOC Investment?
Your SOC is the hub of your capability to detect and respond to incidents targeting your organization, but if not implemented, optimized and managed properly, your security operations center may create a lot of noise—impacting your analysts’ efficiency and ability to detect and respond to real threats.

277 days
is the average time it takes to detect and contain a breach.
Ponemon Institute 2023 Cost of a Data Breach

32%
is the average time SOC teams spend investigating incidents that are not a real threat.
Morning Consult 2023 Global Security Center Operations Study
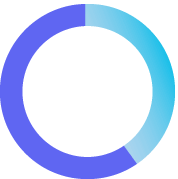
40%
of Security Operations teams are relying solely on manual inputs.
Ponemon Institute 2023 Cost of a Data Breach
Our Security Operations Commitment to You
We will help you create more signal and less noise from your SOC
Our team of security operations experts and engineers will help you optimize your SOC to effectively respond to the latest and most relevant threats to your organization while driving efficiencies in automated and human response, processes and technologies. We do this by:
- Evaluating and addressing your organization’s current network and infrastructure security needs and helping you plan for the future.
- Providing an in-depth look at your SOC processes and capabilities, as well as the overall maturity of your SOC to identify areas of growth and/or improvement.
- Building an Enterprise Framework for Defense to advance cyber protection and threat detection capabilities.
- Building a SOC Maturity Roadmap by determining your SOC’s current maturity and identifying risks and areas of needed growth.
- dentifying ”real world” threats targeting your organization based on cyber threat intelli research.
- Increasing your SOC’s visibility by identifying new detection and response capabilities to protect against the latest threats and intrusions.
- Determining the efficacy of existing detection capabilities and identifying detection gaps based on the latest threats.
- Assessing the fidelity of existing log and data sources and identifying those missing from detection capabilities.
- Consolidating and improving existing response workflows and/or runbooks.
- Providing expert SOC and Cyber Advisory Staffing Services to provide organizations with the right level of expertise to keep your security operations center operational and assist with special projects.
- Ensuring your SOC will scale as your organization and its needs evolve.
SECURITY OPERATIONS CENTER SOLUTIONS
Results-Oriented Security Operations
Center Services
Explore our SOC services:
Our team of SOC experts has experience architecting, deploying and operationalizing security operations for some of the world’s largest organizations. Whether it’s developing a robust data aggregation platform or designing workflows and playbooks to meet a wide range of use cases, our SOC services enable you to respond faster with meaningful insights that improve your overall security.

Security Analytics
Services
Improve visibility into security events, reduce remediation & improve your security posture.

SOAR
Services
Operationalize your SOAR through automated playbooks that enable you to respond faster to alerts.

Insider Threat
Solutions
Build an insider threat program that identifies compromised credentials & malicious individuals.

Splunk Services
Maximize the value of your Splunk instance, improve visibility of security events & reduce remediation time.

Security Analytics as a Service
Experts tailor your security analytics platform to fit your environment & use cases.
SECURITY OPERATIONS OUTCOMES
Ensure your SOC is Fully Optimized to Quickly Detect & Respond to Threats
Our team of security operations experts can help you unlock your full capability to effectively hunt for threats, speed investigations and assess your SOC’s health and compliance.
Decrease time to incident resolution
With greater visibility into security events, you can reduce the time to remediate incidents & improve your security posture.
Gain Efficiencies through Automation
By optimizing SOAR and machine-learning capabilities, you can maximize the value of your investment as well as your security operations team.
Improve Your SOC Maturity Level
Identify gaps within your SOC, validate and improve existing processes, curate threat intelligence & improve collaboration between teams.
Why GuidePoint Security
Your Elite, Highly-trained Team
More than 50% of our workforce consists of tenured cybersecurity engineers, architects and consultants. We are also highly certified across industry standards as well as hundreds of cybersecurity solutions.
Highly Trained, Highly Certified
Examples Include:







Industry Certifications





MITRE ATT&CK Certifications






Product Certifications
Your Trusted Advisor
Our team works side-by-side with you as your cybersecurity partner.
“GuidePoint Security is a trusted partner. Cybersecurity is a program not a project, so it’s always evolving. And GuidePoint does a great job of staying in step with the times. The GuidePoint Security team has an answer for every question and challenge we have around cybersecurity.”
James Lowry
Director of Information Security
Aviation Customer


