
Awkward Adolescence: Increased Risks Among Immature Ransomware Operators
Summary. In recent years, cybercrime has become an increasingly familiar issue amongst cybersecurity professionals, with ransomware in particular commanding news coverage, government statements, and new regulations designed to stem its continued increase. Headlines detailing massive ransom demands and attention-seeking performances ensure that “ransomware” is a household term.
The picture of ransomware that is most commonly depicted–including by Defenders–focuses on ransomware groups as an efficient cybercriminal enterprise, with structures similar to legitimate organizations, which behave similarly and demonstrate technical sophistication. This picture is easy to communicate and easy to understand, and provides a plausible answer to the question – How could so many high-profile victims have fallen prey?
This blog will explore the differences between the ransomware groups we “see on TV”–large, established, well-resourced ransomware-as-a-service operations–and ad hoc, opportunistic, or “immature” ransomware groups that operate more quietly and generally impact smaller, less well-defended victims. We will highlight the increased risks and behaviors associated with such groups and provide two case studies of such immature, high-risk groups that we have observed during recent incident response efforts.
Ransomware Rules
To begin with, we need to start with the baseline understanding of ransomware, which is often driven by media reporting that covers high-profile ransomware incidents performed by large, established RaaS groups. Over the past several years, some generally agreed-upon “ransomware rules” have circulated about such groups that serve as talking points when questions of reliability and risk arise. These “rules” most commonly break down or align with the following:
- Ransomware groups care about their brand and don’t want to harm their reputation (there is “honor amongst thieves”).
- Ransomware groups want to get paid, and if you pay, you will more than likely recover, as promised.
- Ransomware groups are technically advanced and are able to help you decrypt or recover, if paid.
There are a significant number of circumstances, the vast majority really, where some or all of these points are correct, in whole or in part. But there is also an abundance of cases where they have proven to be inaccurate. Ransomware groups can generally be expected to benefit from this depiction of their behavior; look no further than most ransom notes left behind to find insistence of these points:
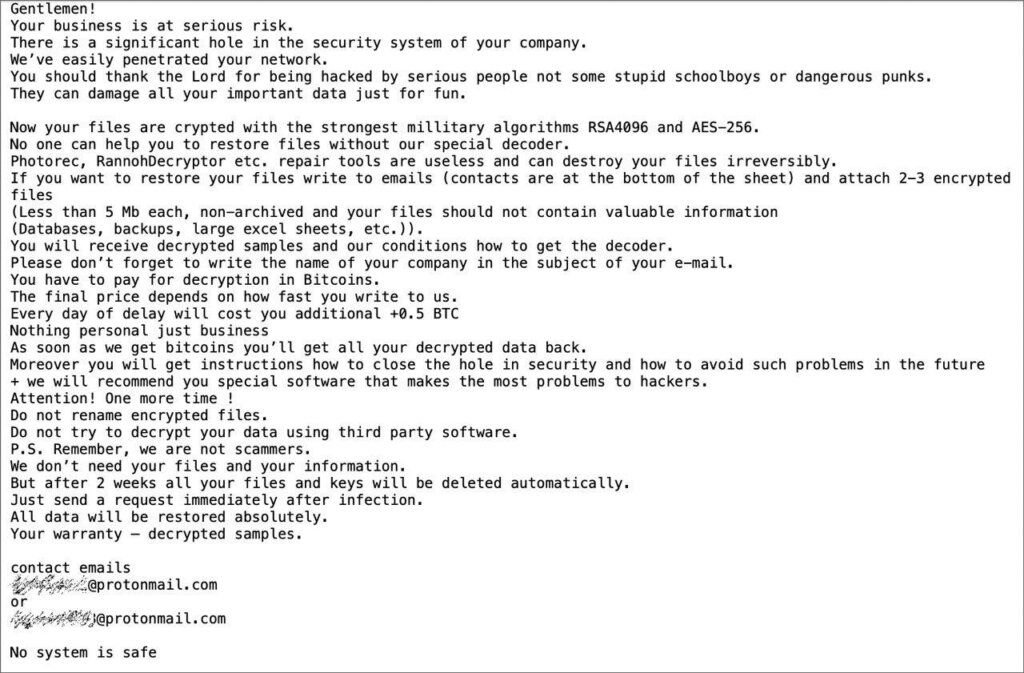
A Ransom Note left by the former Conti ransomware group (source: Bleeping Computer)
Ransomware Reality
As Defenders, Incident Responders, and Threat Intelligence professionals, we have collectively witnessed thousands of ransomware incidents, from triage through response and negotiation to remediation and recovery. Despite most ransomware groups claiming some level of adherence to the above behavior guidelines, a plurality will fail or fall short in at least some aspects. As GuidePoint Security’s DFIR and GRIT teams can attest to, the following outcomes are almost as likely to occur as the “ransomware rules” associated with most “honorable” groups:
- The ransomware group receives payment, does not post stolen data, but does not provide a decryption tool.
- The ransomware group receives payment, provides a decryption tool, and then disappears once the tool does not work optimally.
- The ransomware group receives payment and does not post stolen data, but then demands an additional ransom before providing a decryption tool.
These outcomes can be devastating for victims who have already lost money through operational downtime and the cost of a ransom payment; to come out the other side without anything to show for the cost, or with only an incomplete ability to restore, is salt in an already aggravated wound. With payment as counter-leverage now out the window, there is little a victim can do but cut their losses or choose (often against advice) to throw the dice again. These are the “worst case scenarios” described by law enforcement and cautioned about by legal counsel and ransomware negotiators, but no matter how thoroughly the possibility is covered, victims are rarely financially or emotionally prepared for these outcomes.
This brings us to the core premise of this blog–identifying high-risk scenarios and when a ransomware group is likely to behave as desired vs. as feared. Drawing from our professional experience, our internal data, and discussions with peers from across the industry, we have concluded smaller, opportunistic, and immature ransomware groups are substantially more likely to engage in deception, to re-extort victims, and to fail in delivering functioning recovery tools.
“Immature” Group Characteristics
What do we mean when we reference immature ransomware groups? Let’s look at a couple of characteristics.
First is the matter of identity. Ransomware groups that establish an identity and consistent “brand” face a double-edged sword. If the group follows through and delivers on its promises, they may increase the likelihood of receiving a ransom payment; conversely, if they welch on a deal, it is easier to sound the alarm and warn off future victims that may have otherwise paid. To mitigate these risks or circumvent them, immature ransomware groups may employ no brand name at all or use a throwaway alias with no established history in their communications to victims. This approach likely makes it easier to conceal past dependability issues while hindering attribution and research.
Second is the matter of sophistication. The most prolific and established ransomware groups often make security headlines for quickly weaponizing and exploiting new vulnerabilities or employing new deception in gaining initial access. Immature ransomware groups are more likely to depend on less sophisticated, yet still effective, techniques – exposed ports, services, or applications; compromised credentials; rudimentary phishing campaigns; or plain brute force. This sophistication carries through to actions on objectives, with advanced ransomware groups covering their tracks and exfiltrating large volumes of data. Immature groups, by comparison, may leave tools behind, and may achieve partial or incomplete encryption and exfiltration, if any at all.
Third is the matter of resources. Longstanding, entrenched ransomware groups have often grown their infrastructure over time, with dedicated leak sites, chat infrastructure, Command and Control (C2), encryptors, and supporting malware. Immature ransomware groups, by comparison, are more likely to depend on rudimentary or “second-hand” infrastructure and tools to get by. Encryptors may be lower quality and inconsistent; Decryptors may experience technical issues or require multiple keys for different directories; Leaked or “cracked” varieties of other ransomware may be used; and Email, Tox, or even Telegram may replace dedicated chat infrastructure.
Finally is the matter of audience. Large, established ransomware groups are experienced and skillful in commanding media and social attention through public statements and social media, with security reporting often building a history of the groups as they continue to operate over time. Established ransomware groups also increasingly employ novel coercive tactics, such as contacting victim customers or selling off victim client information in a piecemeal fashion, a time and resource-intensive approach that nonetheless serves to caution future victims of the consequences of non-compliance. Large ransomware groups combine public and media attention with threats to publish sensitive information on data leak sites as the second form of extortion in “double extortion” ransomware operations, allowing the groups them to command ransom payment even in situations where recovery from encryption is feasible. Immature groups, by comparison, often have no attributable history or branding on which to command public or media attention, and thus fewer viable options for increasing external pressure on victims. Immature groups also often lack dedicated infrastructure, preventing the posting of exfiltrated data in a centralized and easily accessible location; while data can be offered or sold on illicit forums and marketplaces, the data is unlikely to fetch a handsome sum or attract much public attention.
“Immature” Group Behaviors
These factors combine to place immature ransomware groups in a considerably weaker position than their more sophisticated peers, which at its surface could be a good thing–we certainly don’t want more ransomware actors with more capabilities and resources to leverage. Unfortunately, blogs don’t often get published with good news, so instead, we’ll highlight how this translates to differences in behavior toward victims:
Re-Extortion. We advise all clients experiencing a ransomware event that nothing is guaranteed, and that no matter what a threat actor conveys, there is the possibility of the actor demanding more once they have determined the organization is willing to pay. We are dealing with criminals, after all. In spite of this, we have not observed any instances of ransomware payment resulting in re-extortion attributed to LockBit, Alphv, Black Basta, or similar groups in 2022 or 2023. Conversely, we are aware of multiple re-extortion attempts from affiliates of Phobos, a nominal ransomware-as-a-service group with low costs to entry and a large network of “affiliates” employing different variants and multiple “cracked” offerings available. In at least one instance, the ransomware operator attempted to extort the victim three times–an initial demand followed by two instances of re-extortion–before communication ended. We note that re-extortion may be driven by greed, but also as a means to cover up technical shortcomings, such as an inability to decrypt encrypted files–if the threat actor can continue demanding payment until the victim declines, a plausible explanation exists that avoids “tipping the hand” of a technically inept actor.
- This behavior primarily ties to the issue of identity. Without a brand to build or defend, or with a name that can be changed at a moment’s notice, there is little to no risk for an immature ransomware group to re-extort victims until they refuse to pay any further. Community information sharing on the topic is low and this class of threat actor attracts less security reporting or scrutiny in general.
- Why it matters: When threat modeling or response planning for ransomware incidents, unbranded or immature ransomware groups should be considered as a distinct threat as opposed to larger, more established ransomware groups. The likelihood of re-extortion by immature ransomware groups is higher, and victim leverage in response to such behavior is naught.
Exaggeration and Embellishment. All ransomware groups are criminal, and the word of their operators should be treated as such. While we have observed a fair share of exaggeration and chest-puffing from larger ransomware groups, it most often applies as an issue of scope–how much data had been stolen, how much access the group still has, how many clients they are threatening to call, etc. With immature ransomware groups, we have repeatedly seen a willingness to deceive not just in what is disclosed–fabricating data theft when none has occurred, claiming widespread exfiltration of directories not accessed, or even claiming intrusions that never happened are all behaviors we have observed from such groups.
- This behavior ties into the issues of identity and sophistication. As with re-extortion, an unbranded ransomware group has no incentive to be truthful and no risk of having its deception detected. There is similarly no risk and abundant incentives for the group to portray themselves as more capable than they are, almost certainly with the goal of increasing payment likelihood. While threat actor claims can be confirmed or refuted through digital forensics, an immature ransomware group benefits from these conclusions lagging and circumstances where recovery options are minimal.
- Why it matters: While all cybercriminal claims should be treated with a grain of salt, be particularly wary and scrutinous of claims made by immature ransomware actors, especially if forensic investigation support is available. Consider all aspects of a ransomware event, including downtime, recoverability, and exfiltrated data, in considering whether a settlement with a ransomware actor is the “best” option or just the most convenient.
Technical Issues. Even the most well-oiled ransomware machines experience the occasional hiccup in encryption or decryption, which is why “support” is often cited as a part of stated “terms” during negotiations. Particularly in Ransomware-as-a-Service groups, affiliates benefit from a core team that is experienced with the ransomware and associated troubleshooting, having built, or refined it in-house. This is far less likely to be the case with immature ransomware groups, which may use lower sophistication ransomware purchased without the assumption of support, or which may be using commodity or leaked ransomware with which they are unfamiliar. This increases the likelihood of problematic or incomplete encryption and decryption and reduces the likelihood of the threat actor’s ability to respond effectively. In multiple cases, the threat actor has ended communications or “ghosted” the victim upon encountering technical issues, either immediately or after several failed rounds of troubleshooting.
- This behavior ties into the issues of identity and resources. As I’m sure you have put together, an unbranded, immature ransomware group faces no backlash or consequences for such disappearing acts and only incurs additional resource costs by attempting to remediate issues for a victim who has already paid. From a resource perspective, immature ransomware groups are less likely to benefit from organic technical experts or a robust support apparatus and, when using leaked ransomware, may have no capability at all beyond the GUI.
- Why it matters: The prospect of technical issues and nonrecovery should be considered in any ransomware incident, but the likelihood of such issues should be considered substantially higher when working with immature ransomware groups. Especially in incidents where a leaked ransomware builder, such as LockBit 3.0 or Babuk, confirm decryption capability through “trial decryption” of sample files, and plan for alternative courses of action should decryption fail in whole or in part.
Affordability and Flexibility. All ransomware groups have a bottom line or minimal price that they are willing to accept as a ransom payment, though the amount that this varies from an initial ransom demand depends on the group. In some cases, such as LockBit, administrator policy prohibits the acceptance of payments beneath 50 percent of the initial demand, though–in other groups–we have seen as much as a 60-80 percent reduction after sustained negotiations. Larger ransomware groups often pursue an approach dubbed “big game hunting,” in which larger, more well-defended organizations are deliberately targeted based on the perceived ability to pay a high ransom amount. This approach is not something we have observed in immature groups, who more frequently target Small to Medium Sized Businesses (SMBs) and similarly sized organizations that are both less well-defended and less capable of paying exorbitant ransom demands. As a result, ransom demands from immature groups are often an order of magnitude lower than those seen from larger groups, often in the tens of thousands of dollars vs. hundreds of thousands of dollars from larger groups. In cases where no payment has been delivered, immature ransomware groups may prove willing to accept substantially lower ransom amounts when facing the prospect of a negotiation falling through, likely in an attempt to extract any possible revenue from victims. While it is hard to imagine how an immature ransomware group could profit from such low ransom amounts, we assess that sufficiently low resource costs (junior or less skilled ransomware operators) coupled with a higher victim volume and/or turnover rate could still render this approach attractive and profitable.
- This behavior ties into the issues of resources and sophistication. Immature ransomware groups are less likely to have scaled and developed specializations relative to larger groups, and the overall experience level of operators may be lower. This may make effective negotiations more difficult, and the combination of smaller organizations and reduced impact may make high ransom demands impractical. As resources have already been expended in order to breach the victim organization, a less sophisticated negotiation strategy focused on quantity over quality may be more achievable.
- Why it matters: If it sounds too good to be true, it probably is. Lower ransom demands, while appealing if affordable, should still be considered as extortion and an extension of the threat actor’s perceived leverage. Consider as well that low ransom demands may combine with a propensity for re-extortion as a means to entice victims into an initial payment, depending on organizations to fall victim to “sunk cost” fallacies in weighing additional payments.
Outsized Threats. Ransomware operators and affiliates love to threaten victims during negotiations, and in most cases, threats represent posturing in order to gain or retain compliance. While larger ransomware groups have time and examples of follow-through on their side to make threats plausible, immature ransomware operators enjoy no such evidence. This does not and has not stopped immature ransomware groups from making grand, sweeping, and improbable threats against victims that often conflict with the version of reality observed in forensics analysis. Immature actors who have not exfiltrated data may claim to have reviewed victim’s financial statements to determine ransom amounts; may threaten to have contact information for major clients or customers; or may threaten time and resource-intensive reattacks against the victim. This behavior likely benefits the immature ransomware operator in at least some cases where the victim lacks appropriate context, though most experienced ransomware negotiators would immediately see through such threats as empty.
- This behavior ties into the issues of audience and sophistication. Immature ransomware operators often possess neither the attentive audience nor the content distribution methods and expertise of larger ransomware groups, lessening their coercive leverage and the threat of reputational damage. Even in circumstances where immature ransomware operators may seek to attract public and media attention, they may find themselves unable to do so.
- Why it matters. Many threats from ransomware operators are empty and amount to posturing, but in specific circumstances or with specific actors they represent imminent and actual risk. When dealing with immature ransomware operators, threats beyond absconding with decryptors are almost always empty, with the threat actor possessing neither the time, resources, nor expertise to make good on their promises. Whether opting to communicate with the threat actor or abstain, victims of immature ransomware operators should consider any associate threats–whether during negotiations or for failure to contact the threat actor–with an even larger grain of salt than those from larger ransomware groups.
Case Study – Phobos
Phobos is nominally a ransomware-as-a-service operation, with a core group (or groups) offering their ransomware for sale at an affordable price point of $100-$150 across a number of illicit forums. Phobos may reference several “splinter” groups and encompasses a number of different “variants” that are classified under the larger Phobos umbrella, including Eight, Elbie, and Faust. Data exfiltration may or may not occur depending on the operating affiliate responsible. (Note: According to Cisco Talos, Phobos variants have also been deployed by 8Base, a considerably more prolific group than most Phobos operators which maintains a data leak site.)
Phobos does not maintain a central data leak site or chat infrastructure, and victim communications most frequently take place over email, with the operating affiliates using “throwaway” accounts with secure email services such as protonmail. Some ransom notes left by affiliates reference the group name or sub-brand, but many do not and remain unnamed. Payment is requested in Bitcoin, and the promised “deliverables” are generally limited to a decryptor unless otherwise specified by the victim and agreed to.
Observed Phobos encryptors often depend on unique encryption keys for each impacted device or directory, complicating decryption efforts. We have observed limited troubleshooting and instructions provided by affiliates.
In a recent incident response case impacting a Small to Medium Sized Business, Phobos encrypted the majority of the victim’s endpoints and virtual machines and demanded a ransom of $70,000 in Bitcoin. The initial ransom note advertised a willingness to provide “tools” upon receipt of 50 percent of the ransom, an offering that makes little sense at face value–after all, who would pay the second 50 percent if they had already recovered?
The impacted victim opted to pursue settlement in this case and was able to negotiate the ransom down first to $35,000 and then to $17,500. After issuing the $17,500 payment in Bitcoin, the threat actor provided an executable file designed to retrieve the encryption key from impacted systems. After checking the executable and retrieving the key, the Phobos operator responded that a decryptor would be provisioned following the confirmation of a second $17,500 payment. When pressed about the agreed-upon price, the communicating threat actor repeatedly insisted that the victim had “misunderstood,” that the agreement was “always $35,000,” and that the “tool” provided upon 50 percent payment had been the executable rather than a decryptor. Of note, the threat actor had previously agreed explicitly to a singular payment of $17,500 before any payment was sent. When confronted with their agreement in plain text, the threat actor abandoned their nominal justification, stating only “the final price is what it is.”
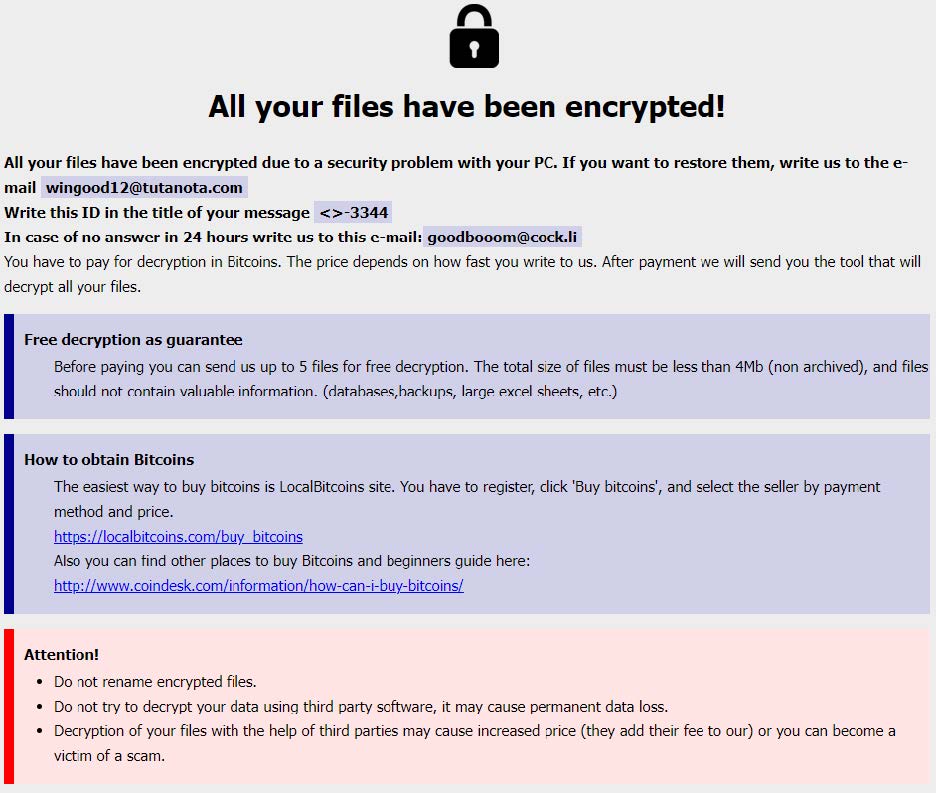
Phobos Ransom Note (source: Cisco Talos)
Takeaways
We have observed and received reporting of re-extortion by Phobos affiliates more than any other immature ransomware group, which could reflect a “nothing to lose” approach as an unnamed or relatively unknown actor, a willingness to rapidly “rebrand” once the group’s reputation for deceit becomes common knowledge, or an attempt to conceal technical issues. Regardless of root cause, we have observed this behavior with sufficient frequency in 2024 as to wholly recommend against any ransom payments to known Phobos affiliates or in cases where the ransomware is determined to be a Phobos variant.
Case Study – DATAF LOCKER
The self-titled DATAF LOCKER threat actor has not been tracked over time as a continuously operating group, and while they are known to have used a leaked version of the Babuk ransomware builder, little else is available in open source security reporting regarding the group or its origins and composition. The group has leveraged a rudimentary chat site over TOR which appeared generic and functioned only intermittently.
In a recent incident response case, the group encrypted the endpoints and virtual machines of a mid-sized business and claimed to have exfiltrated a sizeable amount of data from the victim. Beginning with an initial ransom demand of $300,000, negotiation reduced the final agreed amount to $150,000. After issuing the payment, the threat actor provided a decryptor for impacted Windows virtual machines, requesting that the victim confirm its efficacy before providing an applicable decryptor for endpoints.
After confirming that the first decryptor worked as intended, the threat actor refused to provide any remaining decryptors until “the rest” of the ransom was received; the threat actor later confirmed this to reference an additional payment of $150,000. When pressed that their behavior had violated the terms of the agreement, the threat actor continued to insist that the agreed-upon amount had been for a single “set of keys” and that additional decryptor generation was always outside the scope of any agreement.
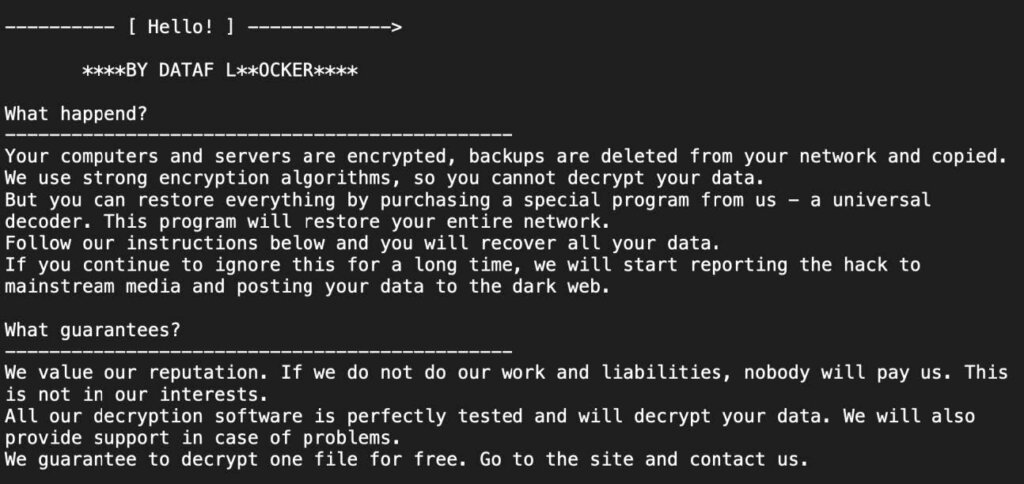
Takeaways
As is the case in the previously mentioned Phobos re-extortion efforts, the threat actor depends upon claims of ambiguity in settlement terms to provide a veneer of justification for re-extortion. We note that this is not the result of a poorly worded or vague settlement agreement, having seen the same behavior even in cases where the alleged ambiguity was explicitly addressed in terms that were agreed to multiple times (i.e., the threat actor had agreed not to request additional payment and to provide all applicable decryptors). The group also almost certainly expected minimal blowback for its decision based on its relatively unknown status, with background research at the communications’ outset yielding only AI-generated references to the group.
Conclusion
Popular images, depictions, and understanding of modern ransomware groups often focus on the largest and most established groups, which maintain media attention through high-profile attacks and sensationalist extortion tactics. While this segment of the ransomware ecosystem exists and remains relevant, immature ransomware groups operating on the fringe continue to harm smaller and less well-defended organizations, often without a recognizable brand or name to aid in attributing and ascribing deceitful behavior. Examples include Phobos and DATAF LOCKER, both of which are known to have accepted a negotiated ransom amount only to re-extort victims for a secondary payment before completing or delivering decryptors. In considering ransomware incidents as part of enterprise incident response planning efforts, we strongly encourage organizations to consider the known history, credibility, and plausibility of ransomware groups and the claims of their operators in order to reach an informed decision regarding ransom payment or non-payment. At a minimum, payments made towards unknown or poorly understood immature ransomware groups should be undertaken with an understanding and acceptance of the increased risk of re-extortion, embellishment or exaggeration, and technical issues in decryption.




























