
GRIT Ransomware Report: February 2024
Additional contributors to this report: Nic Finn, Jason Baker, Justin Timothy, Ryan Silver
February 2024 was an utterly chaotic month in the ransomware space. After a relatively quiet January, the diverse set of ransomware actors that we monitor showed that they are on pace to continue exceeding 2023’s operational tempo, adding almost 100 additional victims relative to January.
Without question, the most impactful event in February was the international law enforcement operation aimed at disrupting LockBit and the resulting fallout. Despite several arrests, sanctions, and the release of decryption keys for recent victims, the administrators of LockBit worked quickly to bring their operations back online. In the face of what could have otherwise been an existential threat, LockBit rebuilt its data leak site after just five days and resumed posting victims throughout the end of the month – never deviating from its place as the most prolific ransomware group operating today. The long-term effects of the law enforcement operation on the group’s ability to accrue new victims remain to be seen, but some impacts are readily apparent. In this month’s Ransomware Report, we explore the ways in which LockBit has likely been affected by this month’s events, how they might recover, and whether or not LockBit is likely to remain the “apex predator” of the ransomware ecosystem should affiliate trust erode.
February also proved to be an advantageous month for less prolific groups of varying maturity levels. Hunters International, Play, and 8Base all accrued enough victims to place in the “top five” most impactful groups for the month, with Hunters International, in particular, achieving a record high for a single month. These players may or may not have been inspired by the potential downfall of their largest competitor, but the chance to pounce on vacated market share is likely not lost on these largely opportunistic actors.
Finally, this month continued the unfortunate trend of threat actors impacting sensitive industries in their quest to extract ransom revenue. Groups like Rhysida continue to operate without regard for the human cost of targeting the healthcare industry, posting two such victims this month, including a children’s hospital. Alphv made headlines with its attack on the healthcare technology company Change Healthcare, whose downtime had wide-ranging effects on all aspects of the US healthcare system. At the time of this report’s publication, Alphv seems to have received a ransom as a result of this operation and then vanished with an ill-gotten “nest egg.” Sadly, the potential for this type of payday underscores the reward that entices individuals into ransomware operations, with accompanying risks to the operators and even greater risks to human lives downstream. Thankfully, this norm-busting behavior has not been observed across all ransomware groups. However, a sufficient number has proved willing to turn a blind eye if it increases the “bottom line.” As 2024 develops and threat actors show fewer and fewer restrictions on attacks, healthcare and other sensitive industries, including education, must be vigilant and increase defensive measures to mitigate the ever-increasing threat of ransomware.
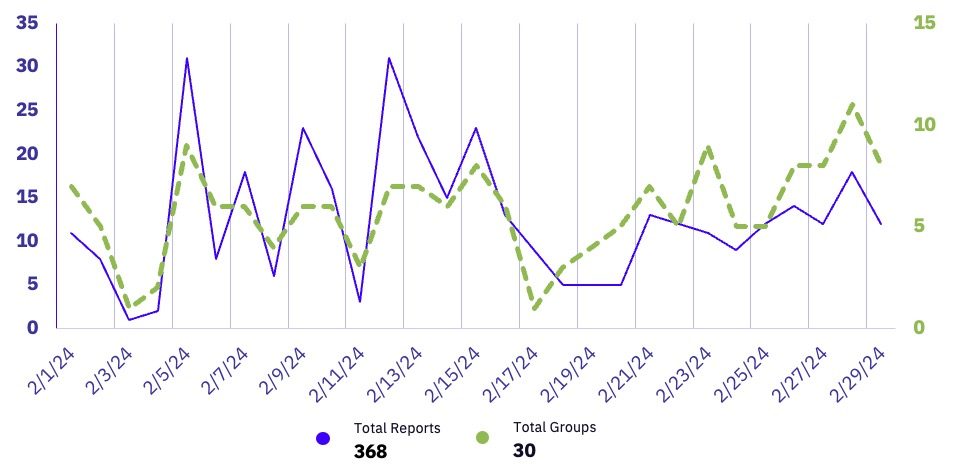
| Total Publicly Posted Ransomware Victims | 368 |
| Number of Active Ransomware Groups | 30 |
| Average Posting Rate (per day) | 12.7 |
Ransomware Trends
February’s ransomware statistics demonstrated a significant increase in activity compared to the same period last year. Observed victim volume surged by 53% year-over-year, up from 241 in February 2023. This growth is mirrored by a 58% year-over-year increase in the number of distinct ransomware groups under observation, climbing from 19 in February 2023.
Temporally, the uptick in observed victim posts for 2024 – from 271 to 368, a 36% increase – echoes the 53% increase observed in the same period of 2023. This similarity suggests holidays, such as New Year’s and Orthodox Christmas, may have delayed or slowed ransomware operations.
If 2024’s victim volume trend continues at a rate similar to 2023’s, we would expect an even higher number of victim posts in March of this year. However, it is important to acknowledge that the recent dissolution of the second-most prolific ransomware group, Alphv, and the disruption of the most prolific ransomware group, LockBit, may introduce uncertainty into these trends, potentially impacting short-term activity levels.
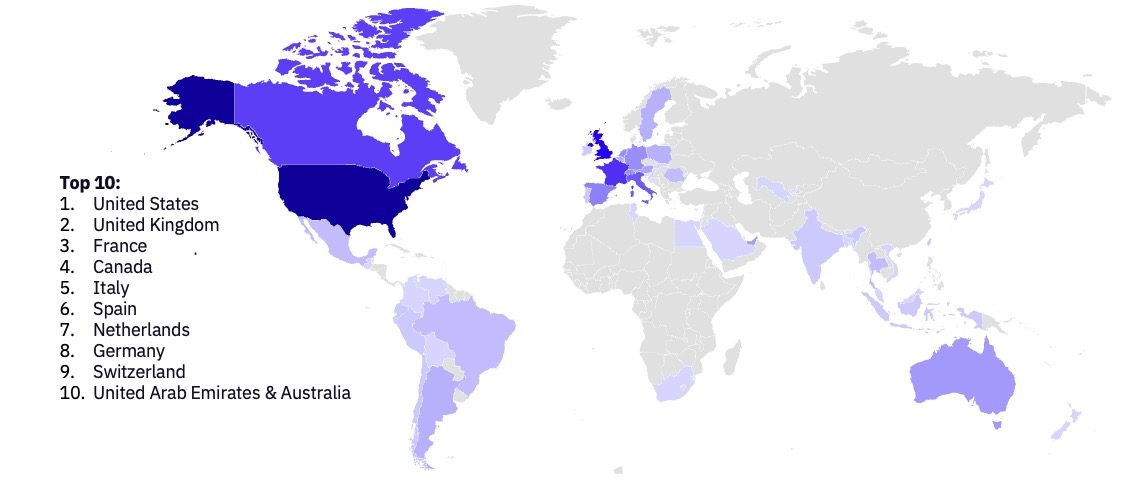
Ransomware Victims by Country
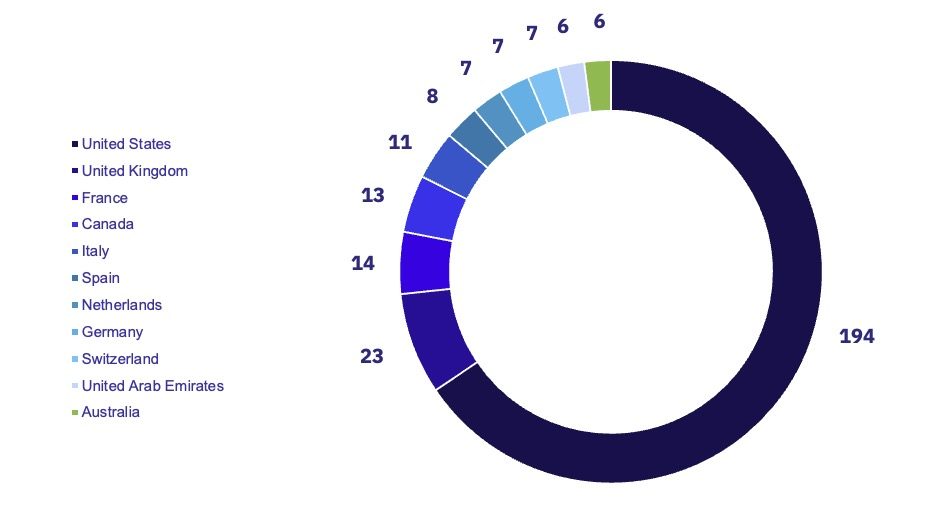
February continues the ongoing trend of US-based organizations disproportionately bearing the brunt of ransomware attacks. In January and February of 2024, US-based organizations accounted for 55% and 52.7% of all observed ransomware victims, respectively. This represents a 4-5% increase compared to 2023 figures (50% and 48.5%), continuing the escalation in the threat to US-based organizations.
While a 4-5% increase may seem modest, the growing total volume of ransomware victims year-over-year amplifies its impact. This trend underscores the outsized risk faced by US businesses and institutions.
Outside of the United States, only five countries suffered ten or more victims in February. Notably, all were located in North America or Western Europe, demonstrating the geographically concentrated nature of current ransomware campaigns.
Industry Trends
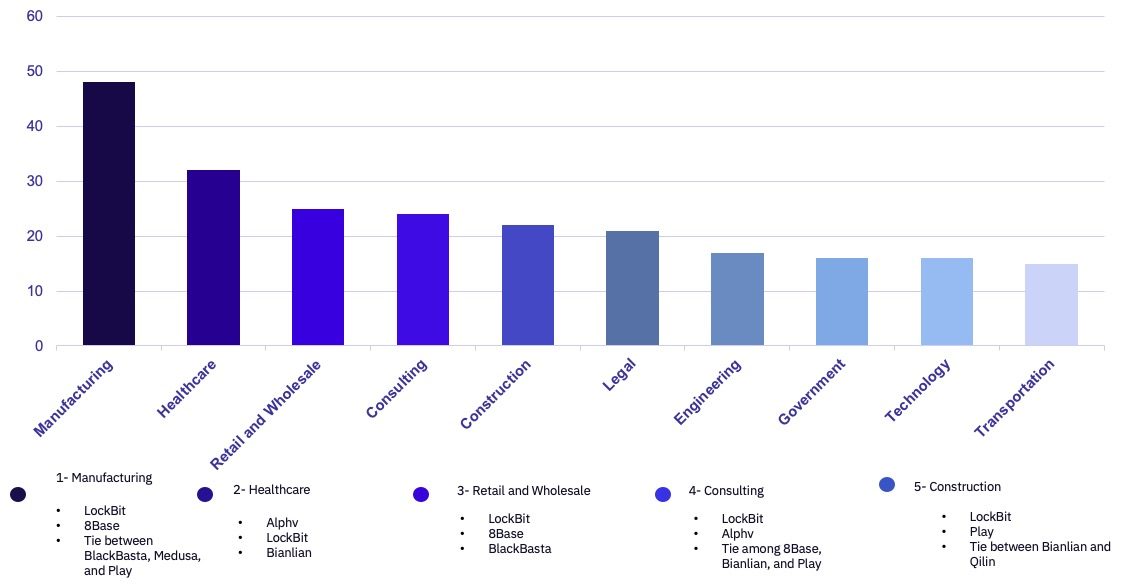
Manufacturing continues to be the industry most heavily impacted by ransomware, with Healthcare and Retail following closely behind. The Healthcare sector experienced a significant surge in attacks during February, with 32 victims compared to only 14 in January. This increase is primarily driven by larger ransomware groups like Alphv and LockBit.
As we predicted, the Retail and Wholesale industries are facing increased impacts in Q1, likely due to seasonal factors. A diverse set of threat actors claimed 43 victims in this sector during the first quarter of 2024, making it the third most impacted industry to date this year.
Interestingly, the Technology industry showed a potential decline in attacks. Only 16 victims were reported in February, a notable decrease compared to 2023, when Technology consistently ranked among the top affected industries alongside Manufacturing and Construction. GRIT will continue to monitor these industry trends closely throughout the year for signs of potential shifts.
After a steep decline in January, Government entities once again made the top-10 list of impacted industries in February. 16 Government-related victims were posted, a significant increase from the two reported in January. Surprisingly, the attacks displayed geographical diversity. While the United States accounted for seven of the sixteen total victims, claims were also made against Government agencies in smaller countries like Bangladesh, Ecuador, and Sweden.
Threat Actor Trends
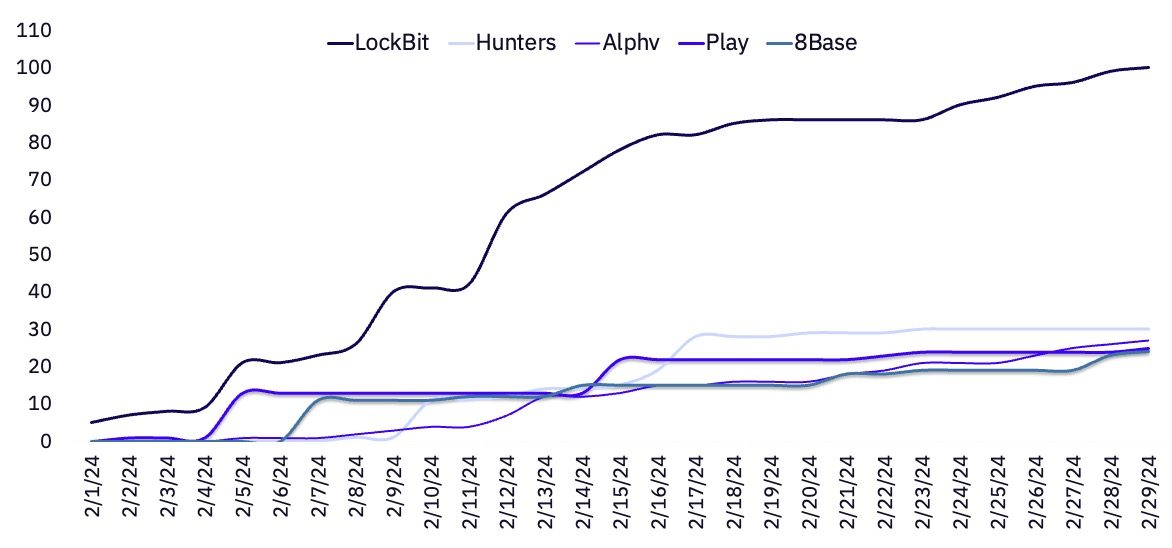
By the second week of the month, LockBit’s February victim volume had already outpaced all other individual ransomware groups before facing an expected and dramatic slowdown in the wake of International Law Enforcement’s disruptive “Operation Cronos.” New posts resumed not long thereafter, though it remains to be seen whether the posts represented new victims or previously breached organizations.
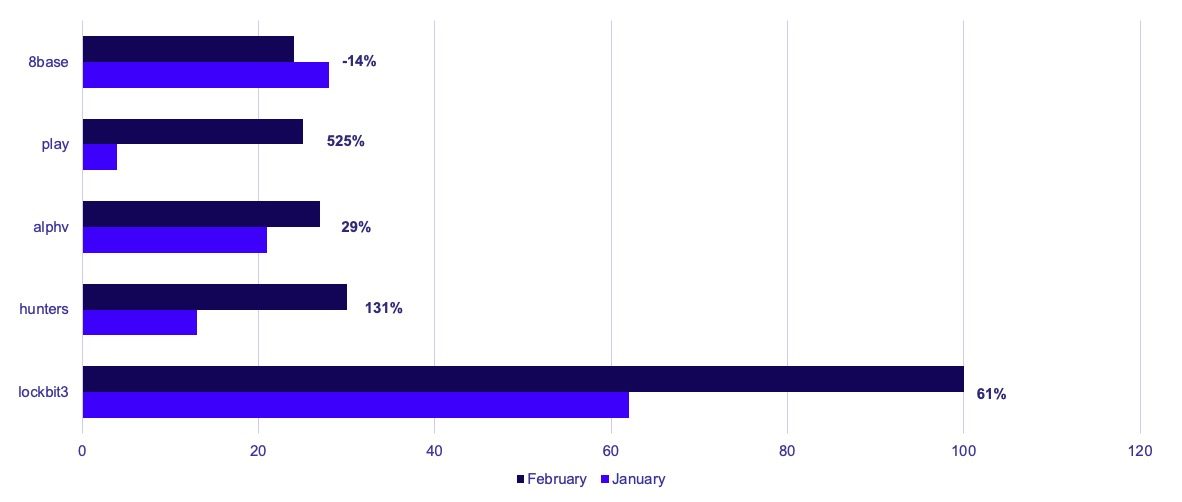
Hunters International appears to be quickly increasing its operational tempo, with a 130% and 36% increase over January and February’s victim volumes, respectively.
Following two consecutive months of slight decreases in claimed victims, Alphv has posted their first monthly increase since November. Alphv increased its number of claimed victims from 21 in January to 27 in February, a 29% increase.
Threat Actor Spotlight: ThreeAM (Developing)
ThreeAM is a Developing ransomware group first tracked by GRIT in September 2023. With 27 total publicly claimed victims they are not the most prolific ransomware group currently operating, but their victim selection and methodology has piqued the interest of several security researchers, including GRIT, questioning their origin and niche in the space.
Symantec’s Threat Hunter Team was the first to identify the ThreeAM ransomware in the wild, discovering the group’s allusion to the ThreeAM moniker in their ransom note and encrypted file extensions. Investigations into ThreeAM incidents uncovered evidence that the threat actor responsible had first attempted to deploy the LockBit ransomware encryptor before falling back to the ThreeAM ransomware after the LockBit encryptor failed.
This occurrence may be the result of a less mature ransomware operator attempting to deploy a leaked copy of the LockBit ransomware, which has been available in the wild since August of 2023. Equally likely is the possibility of an active LockBit affiliate performing operations on behalf of more than one ransomware group, as is reportedly common in the Ransomware-as-a-Service (RaaS) ecosystem as a result of a limited supply of skilled and trustworthy affiliates. While there is no evidence available to suggest that ThreeAM is operating as a RaaS operation, we have observed an increasing operational tempo since the launch of their data leak site, potentially indicating an improvement in the quality and/or quantity of their operations. ThreeAM posted six victim organizations in February, their most active month since the launch of a data leak site that contained presumably legacy victims.
We have paid particular attention to the sharing of LockBit and ThreeAM ransomware by at least one affiliate in the wake of recent law enforcement operations which threaten LockBit’s long-term viability and its attractiveness to affiliates. Although LockBit was only offline for five days, the effects of law enforcement involvement will likely continue to be felt by its current and former affiliates, including those not yet in custody. Ransomware as a whole is a trust-based business, and any breakdown of trust in the RaaS and affiliate relationship should encourage affiliates to seek alternatives for their own safety. With time, ThreeAM may show itself to be one of several viable alternatives to LockBit, in which case we would expect to see continued increases in the group’s victim volume in the coming months. We will similarly monitor other Developing and Established groups with known crossover to LockBit affiliates for noticeable upticks in activity as 2024 progresses.
Other Notable Ransomware Events
LockBit Disrupted by International Law Enforcement
On February 19th, 2024, International Law Enforcement Organizations (LEOs), including the United Kingdom’s National Crime Agency (NCA), The US Federal Bureau of Investigation (FBI), and the European Union Agency for Law Enforcement Cooperation (Europol), announced the disruption and takeover of the LockBit ransomware group’s data leak site and infrastructure, in an operation dubbed “Operation Cronos.” On February 20th, LockBit’s former data leak site was further updated by the controlling LEOs to mimic LockBit’s historical branding and graphic design, but with resources for LockBit victims and announcements from Operation Cronos supplanting former victim listings.
Through Operation Cronos, Law Enforcement was allegedly able to discover and share decryption keys for recent victims impacted by LockBit’s ransomware, and both the FBI and NCA provided contact methods for recent victims that may benefit from receipt of the keys. Separately, Japan’s National Police disclosed the creation of a LockBit recovery tool that may be used by victims of LockBit in circumstances where decryption keys are not available. In addition, Law Enforcement announced the identification and seizure of six LockBit servers used for hosting StealBit, a data exfiltration tool used by LockBit affiliates in support of the group’s double-extortion ransomware operations.
As part of Operation Cronos, LEOs discovered and announced the discovery of historical LockBit victim data hosted on LockBit’s infrastructure, including data belonging to victims that are thought to have paid a ransom to the group. This discovery supports long-standing assessments in the threat intelligence community that some ransomware groups, including LockBit, have retained possession of some exfiltrated data, even when paid or providing alleged “evidence” of deletion. Relatedly, we note that despite the disruption operation, LockBit’s administrators have claimed to retain copies of at least some victim data, which could support future extortion attempts. LockBit recreated their data leak site and began posting “new” victims on February 24th.
The seizure of LockBit’s data leak site and infrastructure coincided with the US Justice Department’s announcement of indictments against two Russian nationals with suspected LockBit ties, Artur Sungatov and Ivan Kondratyev. Both are charged with deploying the LockBit ransomware against “numerous victims throughout the United States, including businesses nationwide.” Importantly, the Justice Department has confirmed Kondratyev as the true identity of a notorious LockBit affiliate long working under the online moniker of “Bassterlord.” Bassterlord was a known and outspoken LockBit affiliate who garnered additional attention after publishing a “how to” guide for would-be affiliates – first, for sale, and later, freely available in a lightly redacted version. The indictments were announced in parallel with the arrest of two individuals in Ukraine and Poland for similar connections to the LockBit ransomware group.
Before it was taken down, one of the last updates to the LEO-controlled LockBit site pertained to LockBit’s public-facing administrator, LockBitSupp. The update claimed that the LEOs “know who he is” and “where he lives,” along with the notion that LockBitSupp “has engaged with Law Enforcement.” Specifics surrounding the engagement were not shared, but the effect was still the same. We assess that this will likely impact the ransomware group’s overall reputation, including its administrator LockBitSupp. Despite this, LockBit has appeared to recover, at least in part, from this massive setback. Just days after the takeover, the group was able to host a new data leak site, complete with new victims that had not been disclosed prior to the takedown. At the time of this report, it is not clear if these victims were breached before or after the takedown was announced, but LockBit continues to slowly claim victims to their site, albeit at a slightly reduced rate relative to pre-disruption operations. LockBit’s behavior in the coming weeks will likely indicate their ability and willingness to recover from Law Enforcement’s disruptive operations, and to return to a pre-disruption operational cadence.
Mogilevich “Ransomware” Revealed as Scam
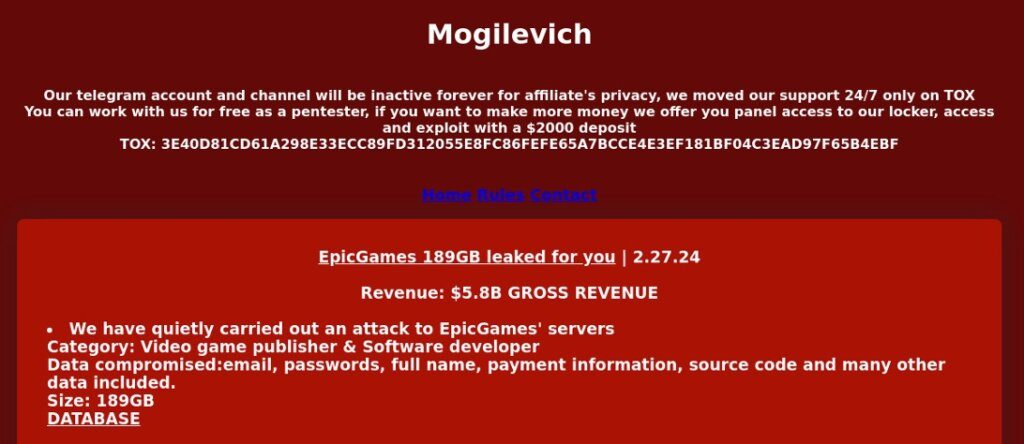
Mogilevich, a self-proclaimed “group dedicated to data extortion,” emerged on February 20th and proceeded to claim high-profile victims, including Infiniti, Epic Games, DJI, and Shein through the beginning of March. The group’s site was updated periodically to reflect the “sale” of associated data, though attempts to solicit proof from security researchers were met with refusal from the group’s ostensible administrator. Meanwhile, listed “victims” refuted the group’s attack and breach claims, citing a lack of evidence of any such breach following internal investigations.
The conflicting reports were reconciled on March 2nd when a persona identifying as “Pongo” posted a statement revealing that “we are not a Ransomware as a Service, but professional fraudsters.” As part of and in summary of the statement, Pongo alleged to have extracted sixteen thousand dollars from individuals paying for panel access to the non-existent Mogilevich ransomware, seven thousand dollars from individuals believing they were buying stolen cryptocurrency accounts, and 85 thousand dollars from an individual believing they were buying sensitive exfiltrated data. Based on the degree of deception disclosed by the actor, there is little reason to believe the amounts claimed reflect the actual level of success of this operation.
In 2023, a persona identifying as ”pongo” belonged to and participated as a member of Breach Forums, an English-language dark web forum. The account is currently permanently banned on the forum, with the provided reason of “Scamming.” Further research uncovered links between this persona and several others used by “Impotent,” the administrator responsible for RansomedVC (briefly known as Raznatovic) and ExposedForum. The persona has become well known as a scammer and fraudster within the dark web forum community and has rotated through a series of usernames and personas while following largely the same playbook of generating attention and attempting to defraud victims.
We assess with moderate confidence that Mogilevich and RansomedVC are both enterprises of the same individual threat actor and that the actor will likely continue attempting scam and faux-extortion operations in the future. We continue to encourage security professionals to be mindful and skeptical of unsubstantiated data breach claims, particularly absent a confirmed intrusion or proof of exfiltration.
Emerging and Developing RaaS Groups Actively Recruiting
Following recent disruptive actions impacting LockBit and Alphv, GRIT has identified multiple Ransomware-as-a-Service (RaaS) advertisements for affiliates from other groups on deep and dark web forums during the month of February. These advertisements likely indicate attempts by smaller groups to recruit former affiliates from Alphv and LockBit, with affiliates potentially seeking more secure income or to reduce the likelihood of future arrest. GRIT observed advertisements from the Established group, Medusa; the Developing group, Cloak; and the Emerging group, Ransomhub, indicating recruitment attempts by groups of varying maturity levels as measured by GRIT’s ransomware taxonomy.
In one particular example, RansomHub’s post on the Russian-language dark web forum RAMP explicitly refers to recent law enforcement disruption: “We have noticed that some affiliates have been seized by the police.”
All three observed groups implicitly reference recent affiliate non-payment concerns following a probable “exit scam” by Alphv. They tout a generous ransom split ranging from a 70/30 affiliate/core payout to 90/10, and in some cases, ransom payment is delivered directly to the affiliate rather than the core group.
The advertisements promote attractive features of their respective operations, including robust web panels and ransomware encryption malware, or the availability of negotiators to communicate with victims directly, all of which are likely to render an operation more attractive to current or former affiliates of other groups. The advertisements from Medusa and Ransomhub include stipulations prohibiting the targeting of any organization based within the Commonwealth of Independent States (CIS), with RansomHub also forbidding attacks against Cuban, North Korean, and Chinese targets.
GRIT assesses that additional recruitment advertisements for RaaS affiliate programs are likely to appear in the following months, particularly if and when specific ransomware groups terminate operations or enter a dormant period. We have previously assessed that competition for limited affiliate resources may drive future discord in the ransomware ecosystem, and more protracted or direct poaching attempts may lead to group consolidation, greater attack automation, or model shifts in modern RaaS operations.
Widespread Disruption Highlights Ransomware Risk to Healthcare

In February, two high-profile attacks against healthcare organizations—Lurie Children’s Hospital in Chicago and Change Healthcare—led to widespread disruption of healthcare services nationally and garnered extensive media attention.
The Established double-extortion RaaS group Rhysida attacked Ann & Robert H. Lurie Children’s Hospital of Chicago in late January, forcing the hospital to take their IT network offline and severely disrupting hospital operations for several weeks, according to media reports. Rhysida posted the organization to its data leak site on February 27th, offering an alleged 600GB of data for sale at a price of 60 Bitcoin, around $65,000 at the time.
Before seemingly disbanding in the aftermath, the Established double-extortion RaaS group Alphv, also known as Black Cat, attacked Change Healthcare, a subsidiary of Optum and UnitedHealth Group (UHG), in late February. The attack has had widespread impact on the health networks and systems dependent on UHG’s services, with the president of the American Hospital Association decrying the attack as “the most significant and consequential incident of its kind against the U.S. healthcare system in history.” Multiple media reports have indicated that Alphv received a ransom of approximately $22 Million in Bitcoin, though Change Healthcare and UHG have not confirmed this.
Healthcare organizations had, until recently, been considered more sensitive or “taboo” targets, in some instances drawing apologies from ransomware groups whose affiliates had “gone rogue” and attacked them. We observed a gradual erosion of these ostensible norms in 2023, with an unchecked increase in healthcare attacks from 159 to 292, an 84% increase year-over-year. We assess that this trend of increased attacks impacting the healthcare sector will likely continue as 2024 continues.

This erosion in norms is likely driven in part by financial motivations, as ransomware groups have not necessarily received outsized law enforcement scrutiny or attention in response to healthcare industry attacks. Put more colloquially, they’ve determined they can get away with it and that, at least in some circumstances, victims may be willing to pay.
The healthcare industry often faces challenges in outdated software and security measures, with unpatched systems and medical providers/support staff that may be less familiar with cyber security best practices. These realities can be exploited by ransomware groups to gain initial access to networks through vulnerable devices or phishing.
Healthcare organizations have and will continue to make attractive targets for ransomware groups due in part to the sensitivity and value of Personal Identifiable Information (PII) and Protected Health Information (PHI), which increases both extortive leverage over victims and the value of data for sale to other actors should the victim not pay.
ConnectWise ScreenConnect Mass Exploitation
On February 19th, 2024, the automation company ConnectWise disclosed a pair of vulnerabilities in ScreenConnect, a Remote Monitoring and Maintenance (RMM) tool used primarily for IT staff troubleshooting and remote work. The vulnerabilities, CVE-2024-1708 and CVE-2024-1709, are path traversal and authentication bypass vulnerabilities, respectively, with the former rating as “high” severity and the latter rating as “critical” severity. Proof-of-concept (PoC) exploits were developed within 48 hours, and the ease of exploitation facilitated rapid adoption by threat actors of varying maturity and sophistication levels. Within three days of disclosure, CVE-2024-1709 was added to CISA’s catalog of Known Exploited Vulnerabilities (KEV), indicating widespread exploitation “in the wild.”
Over the duration of February, CVE-2024-1709 has been exploited by malware campaigns, initial access brokers, and ransomware operators to facilitate initial access, command execution, and command and control (C2). Ransomware groups known to have exploited the vulnerability include Black Basta and Bl00dy, the latter of which has employed the leaked LockBit ransomware encryptor in attacks; other groups known to have exploited the vulnerability include the North Korean Advanced Persistent Threat group, APT43, also known as Kimsuky.
These vulnerabilities come on the heels of similar mass exploitation of vulnerabilities impacting Ivanti Connect Secure, a remote access VPN solution, which was similarly leveraged by a wide range of threat actors. The rapid adoption and exploitation of these vulnerabilities by ransomware groups may indicate an increased willingness and ability of ransomware groups to adopt publicly disclosed vulnerabilities and their associated exploits as part of their attack chains rather than pursuing or purchasing undisclosed “zero-day” vulnerabilities. Particularly as organizations increasingly implement defensive technology and laypersons become more familiar with common social engineering techniques, vulnerability exploitation may provide a more attractive, stealthy, and dependable access method.
In our annual report, we assessed that vulnerability exploitation would become more common among ransomware groups, particularly with regard to public-facing infrastructure and enterprise software. Widespread ransomware group exploitation of CVE-2024-1709 and the preceding Ivanti Connect Secure vulnerabilities supports this assessment and indicates likely future recurrence in severe vulnerabilities impacting other enterprise software.
We strongly advise organizations to maintain situational awareness of easily exploitable or widely exploited vulnerabilities, and to prioritize them for patching or mitigation ahead of existing backlogs. We note that while threat actors may operate most successfully and stealthily in the lead time between vulnerability identification and patch provision, the majority of attacks generally occur in the weeks and months following vulnerability disclosure, impacting unpatched targets of opportunity.
Akira Encryptor Update
In June 2023, researchers at Avast Threat Labs released a public decryptor that enabled previous victims of the Akira ransomware group to decrypt their files for free. At the time, GRIT assessed that this would be a damaging blow to the bottom line of the group, which would have to either change tactics or make considerable updates to their encryption technology to prevent future unintended decryption.
Almost immediately after the publication of Avast’s decryptor, we observed a shift in tactics by the group to focus primarily on data theft and extortion, in some cases opting not to encrypt victim networks at all. These updated tactics were almost certainly born out of necessity but ultimately proved effective as Akira’s victim volume steadily increased over the following months, placing them among the most prolific ransomware groups.
This month, Unit 42 identified significant changes to the codebase of Akira’s encryptor, which likely represents an attempt to dissuade researchers from attempting to reverse engineer the malware. The previous version of Akira’s encryptor was written in C++ and compiled for Windows and Linux and used the Windows CryptoAPI protocol to generate an RSA-4096 encrypted key on run. This version then used an implementation of the ChaCha20 cipher to encrypt sections of targeted files. The weakness of the original Akira encryptor lay in its handling of small files, with the malware encrypting only the first half of files under two million bytes, thereby allowing reverse engineers to potentially unravel the encryption key.

The latest version of the Akira ransomware uses implementations of KCipher2 and ChaCha20 to perform symmetric file encryption. The group has seemingly learned from their mistakes, and now ensures that small files are fully locked by encrypting them in their entirety, leveraging a new auto-save feature which enables systematic piecemeal encryption.
These updates show how hard ransomware groups are willing to work to preserve the viability of current double extortion tactics as part of the larger Ransomware as a Service model. By comparison, smaller groups may be unwilling or unable to invest the time and resources required to harden their encryption tools, leaving them open to decryption by those knowledgeable enough and sufficiently skilled to do so. GRIT assesses that the “cat and mouse” game of decryptor development and release will continue in the future but may be less visible should decryptor release enable ransomware groups to adjust and continue operations. Private and public sector development and provision of decryptors to victims, without notifying ransomware groups of specific codebase weaknesses, may serve more victims and degrade ransomware profitability in the long term.
Ransomware Groups First Tracked by GRIT in February:
Blackout

Blackout posted its first two victims to a dedicated data leak site on February 27th. Though little public information is available about the group, its operations, or its structure, references to ”blackout ransomware” have been observed in illicit forums and marketplaces on the deep and dark web dating back as far as February 2022. References to an ”editable” ransomware “for beginners” named Blackout, offered for the price of $6 USD, can be found in early 2022 posts on Nulled Forum and Kingdom Market. Later, allegedly improved versions were posted to Breach Forums, MGM Grand Market, Kingdom Market, and Dark Forums in late 2022 – late 2023. We do not know if the Blackout ransomware associated with the observed data leak site and the Blackout ransomware posted for sale from 2022-2023 are the same variant and malware family or merely share a name.
Alphalocker
Alphalocker began posting victims to a dedicated data leak site on January 24th, and as of the time of this report has posted eight victims between January 24th and February 14th, 2024. We note that several of the victims’ pages on the data leak site appear limited to database information and database backups, including SQL database contents, though others may contain more widely-scoped exfiltrated data. We have no indication that this data leak site is connected in any way to an “affordable” ransomware strain using the name of Alphalocker in 2016.
Ransomhub
Ransomhub is a self-described Ransomware-as-a-Service operation first disclosed in announcements on the Russian-language dark web forum RAMP in February 2024. The encryptor has versions written in C++ and the Go programming language and claims to support encryption of Windows, Linux, and ESXi devices. Initial posts announcing the group explicitly forbid attacks on the Commonwealth of Independent States, Cuba, North Korea, and China, as well as encryption of non-profit hospitals. At the time of this report, Ransomhub has publicly claimed five distinct organizations across nine posts from February 10th to March 4th on its data leak site.

Final Thoughts
Overall, February demonstrated the continuing resilience of Ransomware’s most prolific and entrenched threat groups, home to operators that have often honed their abilities over years. In the face of increasingly countervailing forces, including law enforcement disruption and breaking of encryption, financially motivated threat groups such as LockBit, Alphv, and Akira show that they are willing to make large investments in blood and treasure to return to their status quo.
By continuing or resuming operations after disruption and setbacks, ransomware actors are almost certainly attempting to project strength and signal to their victims and other actors that they are unstoppable, despite the observable impacts of recent operations in aggregate. Each time law enforcement seizes ransomware infrastructure or a security researcher finds a vulnerability in an encryptor, the threat actor on the receiving end of the disruption must take steps to adjust and recover. These steps cost the actors time, money, and other resources that would otherwise be spent acquiring and impacting new victims and may shift the risk vs. reward calculus of participants in the ransomware economy. Much speculation can and has been made about the herculean task of wiping a sufficiently motivated and sophisticated actor from the internet entirely; however, by imposing incremental cost through disruptive actions, Defenders can chip away at the capability and viability of ransomware operations.
In light of the recent widespread and high-visibility impacts of ransomware on sensitive industries such as critical infrastructure and Healthcare, discussion amongst decision-makers on combating ransomware will likely come to the forefront in the near term. The concept of ransom payment bans has circulated extensively in the United States following the implementation of a limited number of state bans over the past year and often highlights the downstream impacts we have observed this month. The concept of payment bans is not without its fair share of detractors, who often highlight the needed lifeline in the event that a successful ransomware operation deals what would otherwise be a mortal blow to the organization’s information systems. Regardless of where individuals and defenders may fall along the spectrum of this argument, the fact remains that no solution will be quick, and any legislation or regulation will likely be slow-moving. For the time being, imposing cumulative costs through disruptive actions is our best available tool and most desirable outcome as defenders. These actions are best observed in aggregate and over time, and we encourage a cautiously optimistic view of their success while encouraging their continued increase in the future.
While ransomware shows no signs of slowing down, February provided much-needed perspective into how defender actions can and do meaningfully degrade ransomware operations over time.
The GRIT Ransomware Taxonomy
By subdividing ransomware groups, GRIT can obtain more detailed insights into how ransomware groups progress in their level of operational maturity and can classify and identify potential rebranding activity.
We distinguish ransomware groups by placing them into these six categories:
EMERGING
This category is reserved for new ransomware groups within their first three months of operations. These organizations may be short-lived, resulting in an Ephemeral group; may be determined to have Splintered or Rebranded from an Established group; or may move on to further develop their operations and TTPs over time.
EPHEMERAL
These groups are short-lived, with varied but low victim rates. Observed victims are usually posted in a single or short series of large postings rather than a continuous flow over time. Ephemeral groups, by definition, terminate operations, spin-off, or rebrand within three months of formation. These groups may or may not have dedicated infrastructure (i.e., data leak sites and chat support) as part of their operations.
DEVELOPING
These groups have conducted operations for three months or longer, resulting in a recurring flow of victims. Developing groups do not appear to be directly linked to other ransomware groups as a Splinter or Rebrand but may include some experienced ransomware operators. Developing groups generally improve their people, processes, or technology over time by recruiting additional members, refining TTPs, or improving the quality of their associated ransomware and encryption. These groups generally have dedicated infrastructure (i.e., data leak sites and chat support) as part of their operations.
SPLINTER
These groups consist of a plurality of members from previously Developing or Established groups and may have formed either by choice or due to exclusion. These groups may be identified by very similar or overlapping TTPs and tooling or through HUMINT gathered through interactions with personas on the deep and dark web. Splinter groups differ from Rebrands by the continued existence of the original organization as the Splinter group operates.
REBRAND
These groups consist in whole, or in part, of former Developing or Established groups. Rebrands often maintain the same people, processes, and technology as the original group. Rebrands are generally undertaken in order to minimize attention from law enforcement or intelligence officials or to avoid negative publicity.
ESTABLISHED
These groups have operated successfully for at least nine months and have well-defined and consistent tactics, techniques, and procedures. Established groups often possess functional business units that enable sustained ransomware operations, with specialists focused on areas such as personnel, encryption, negotiations, etc. These organizations successfully employ technology and redundant infrastructure to support their operations.
There are multiple routes a group can take through the various classifications, and no one route is standard. While one group may begin as “Ephemeral” and move their way through the ranks to “Full-time,” another group may enter as a “Rebrand” as part of a larger obfuscation strategy to avoid attention from law enforcement.