
GRIT Ransomware Report: January 2023
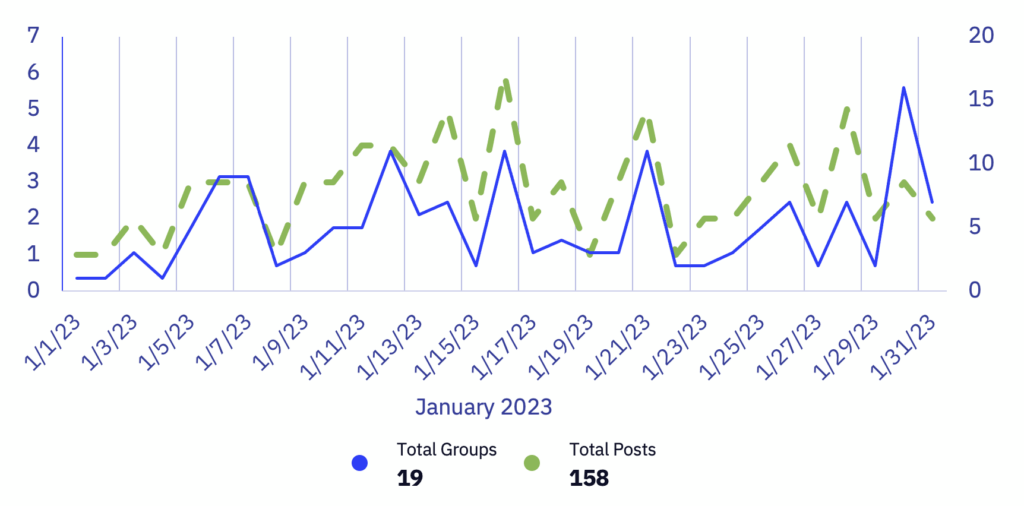
January kicked off 2023 with a slowdown in victim posting rates across ransomware groups. Overall, January saw a 41% decrease compared to December 2022 and a 12.9% decrease in victims compared to January of last year.
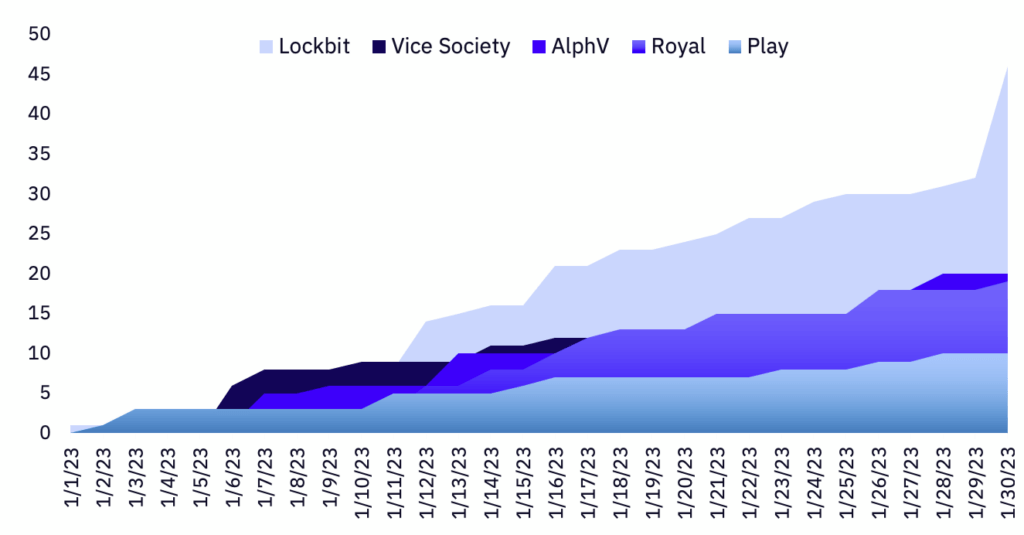
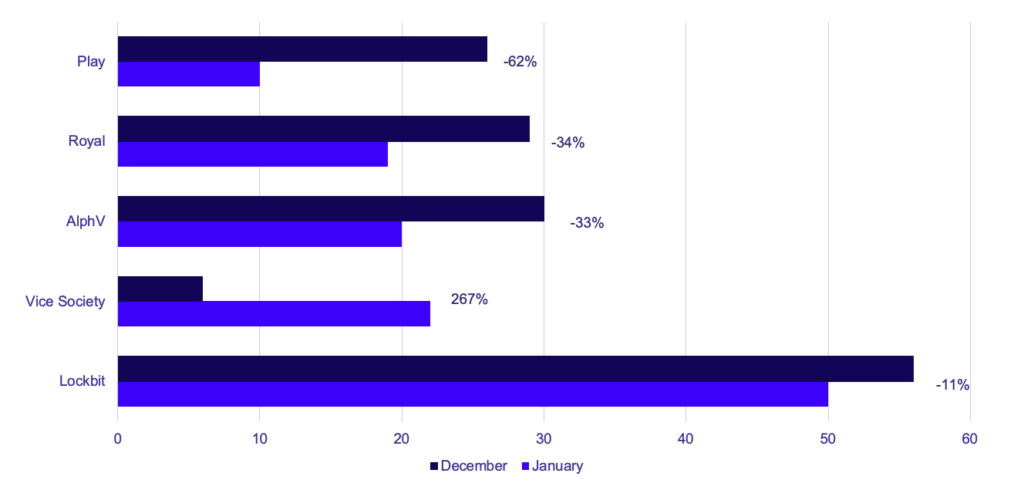
Despite an 11% decrease in victims during January, Lockbit remains the most prolific ransomware group by far, with their victims totaling more than double the other top-five groups: Vice Society, AlphV, Royal, and Play. Vice Society saw a very notable 267% increase in activity, with a significant focus on victims in the Education sector. Out of the top five groups from January, Vice Society was the only group to have an increase in activity compared to December 2022.
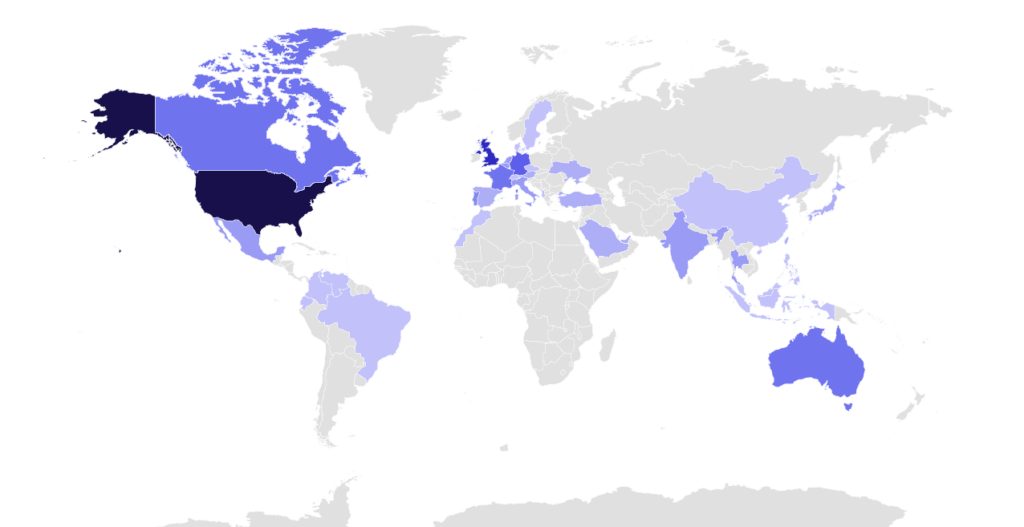
Unsurprisingly, the United States continues to be the most impacted country across all ransomware groups. However, January saw a huge spike in victims from the United Kingdom. At 20 victims for the month of January, the United Kingdom has not seen this many victims since March 2022.
Apart from Construction, Telecommunications, and Aerospace, Defense, & Military, all industries saw a decline in victims during January. This decrease in activity across industries correlates directly to the slowdown observed from December 2022 into January 2023.
Ransomware Trends
Compared to January 2022, there was a 12.9% year-over-year decrease in the rate of publicly posted victims and a 41% decrease following December 2022. Across all groups, there was a consistent posting rate with a large spike at the end of the month.
January’s top ten targeted countries were the United States, United Kingdom, Germany, Australia, Canada, France, Portugal, Belgium, India, and Italy. The United Kingdom had 20 victims this month, the country’s highest number of publicly posted victims since March 2022.
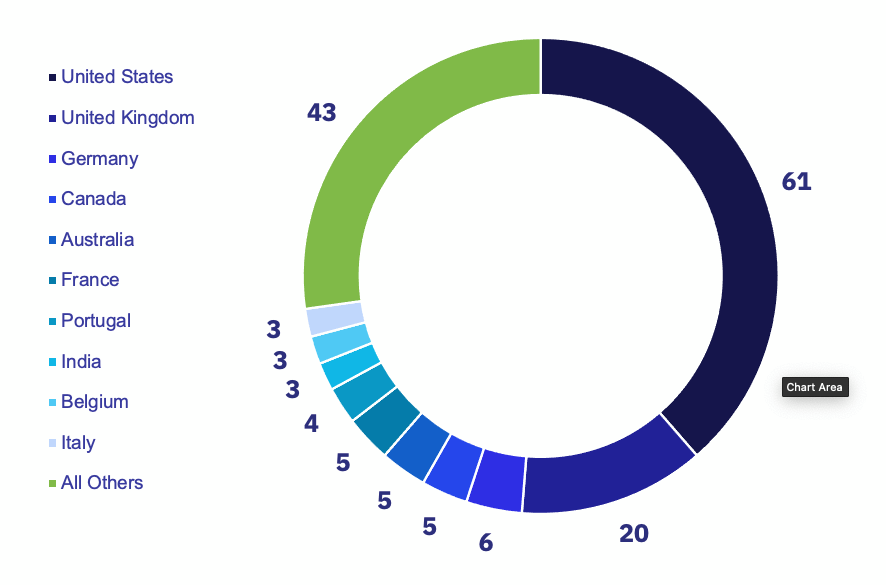
Surprising no one, Lockbit remains the most prolific ransomware group by far, with victims from 23 countries, twice as many countries as any other group. The second highest group was Vice Society, which posted victims from just 10 countries. Specifically regarding the United States, the most active groups were Lockbit, AlphV, and Royal, and the US represented 38.6% of all targeted victims.
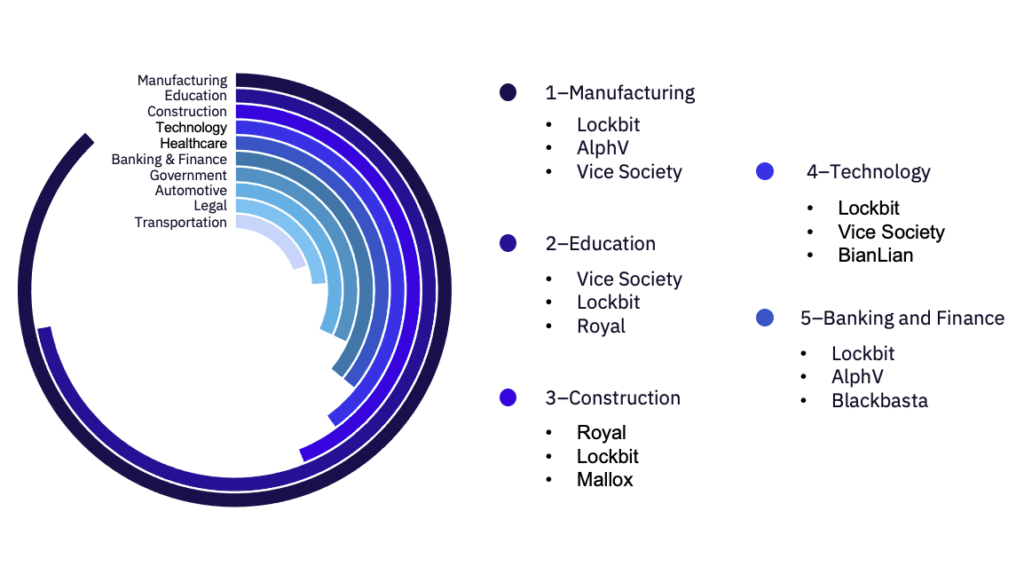
We observed targeting against 37 of the 40 tracked industries in January. Across the top 10 countries targeted, the number of targeted industries within each country are as follows:
Among the top targeted industries, the most active groups were Lockbit, Vice Society, and Royal. The Manufacturing industry had 22 posted victims, while Education saw 18 and Construction had 11. Most industries saw a decline in victims, save for Aerospace, Defense & Military, Construction, and Telecom, which all saw slight increases over last month.
As stated earlier, Lockbit started 2023 off with a firm hold on its position as the most prolific ransomware group, claiming 32% of all victims in January–up from 21% of total victims in December 2022. Lockbit also doubled their victims in the Banking & Finance industry during the month. However, they did see a slight dip in total postings, down to 50 from 56 in December.
Vice Society made an enormous jump this month, increasing their activity by 267% from December, with a total of 22 victims compared to December’s 6. They continued their targeting of sensitive industries and maintained their dominant focus on the Education sector.
In contrast to Vice Society, AlphV saw a 33% drop in postings from December to January. The majority of their victims were in Manufacturing, Agriculture, Banking & Finance, and Healthcare, with a concentration on victims in the United States and India.
Threat Actor Spotlight – Play Ransomware Group
Play Ransomware Group was the fifth most active ransomware group this month and has had a swift rise to prominence since their leak site first became active to claim 36 victims in December of last year. However, it should be noted that multiple intelligence sources have reported references to Play as far back as June 2022.
Play has predominantly targeted the Transportation sector. Government and Manufacturing tied for their second-most favored industries, and Automotive and Chemical round out their top five most impacted industries. The United States and the UK are tied for their most impacted countries, but they tend to favor European victims as the Czech Republic, France, and Sweden complete their top five.
The group utilizes tools that are relatively common to many eCrime groups, including classics like Cobalt Strike, ADFind, SystemB, and GMER. Additionally, they are known to quickly leverage vulnerabilities, most notably utilizing CVE-2022-41080 (Microsoft Exchange Escalation of Privilege), to gain initial access into their victims’ environments. Other notable intrusion vectors include abusing externally-facing RDP and exploiting FortiOS vulnerabilities.
Intelligence suggests that Play shares some behavioral attributes and TTPs with the Hive and Nokayawa ransomware groups, but they employ a unique technique to avoid detection during the encryption process, wherein they only encrypt chunks of data at specific, set intervals.
Other New and Notable Ransomware Events
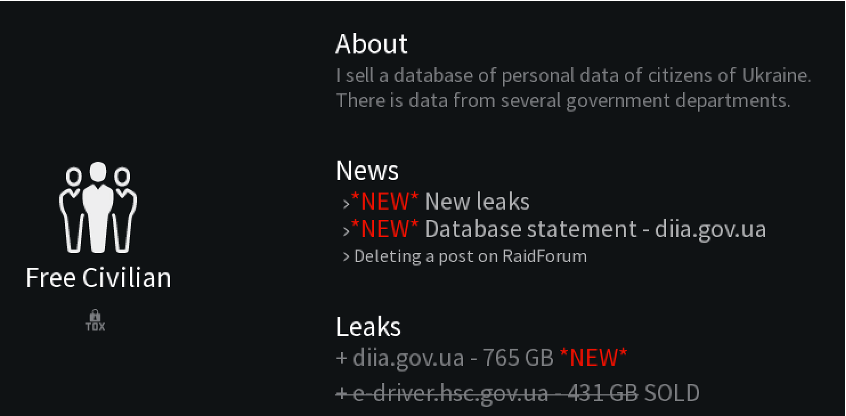
New Leak sites: GRIT first began tracking Free Civilian, a leak site dedicated to releasing data of Ukrainian citizens, in January 2023.
New group: We also came across a new group called ProjectRelic. We are currently developing intelligence and creating a threat profile for this group; however, we do know that their encryptor is written in Go, and they talk to their victims through a custom Tor chat app.
Notable:
On January 26, 2023, the Hive ransomware infrastructure was taken down. Based on recent trends in rebranding, Hive will likely pursue a rebrand to reduce law enforcement attention.
On January 16th, 2023, Avast released a BianLian decryptor, allowing victims to decrypt their files without paying a ransom.
Final Thoughts
Much like the beginning of 2022, January 2023 started off with a lower volume of victims than previous months. The slowdown in overall activity is demonstrated by four of the five most active threat groups in January seeing a significant decrease in their overall number of victims. Similarly, most industries saw a decrease in victims aligned with the overall slowdown in activity during January.
Despite the slowdown in activity, groups like Vice Society had a huge spike in activity with a focus on victims in the education sector. As Play ransomware group arrived on the scene in January, they quickly rose to the top five ransomware groups and are making a name for themselves by swiftly taking advantage of critical vulnerabilities.
On a more positive note, the FBI and coordinating agencies delivered a huge blow to the Hive ransomware group by taking over much of their infrastructure and obtaining many keys associated with victims. Avast’s creation of a decryptor for BianLian ransomware shows how impactful reverse engineering and threat intelligence can be for making threat actor operations much more difficult. Based on recent trends in ransomware rebranding, both of these events are likely to produce one, if not two, rebrand scenarios.
Although 2023 started off slow, if trends from 2022 are any indication, we are primed to see a sharp rise in ransomware activity as Q1 of 2023 progresses. Groups like Play are demonstrating just how impactful ransomware continues to be in 2023, while the cybersecurity industry and law enforcement respond in kind. As 2023 continues, GRIT will continue to monitor active ransomware groups to establish ransomware trends and disseminate threat intelligence accordingly.




























