GRIT Ransomware Report: May 2023
Additional contributors to this report: Jason Baker, Nic Finn
During the month of May, GRIT observed an increase in the number of ransomware victims compared to April 2023. However, the most prolific ransomware groups, including Lockbit, Alphv, and Royal, exhibited either a reduction or stagnation in their number of victims posted. Despite this trend from established groups, the overall impact of ransomware remained significant. We observed several new branded groups entering the scene, contributing to a cumulative rise in the number of observed ransomware victims. These emerging groups leverage both established and novel tactics in an attempt to blend in and profit amidst an increasingly crowded ransomware economy.
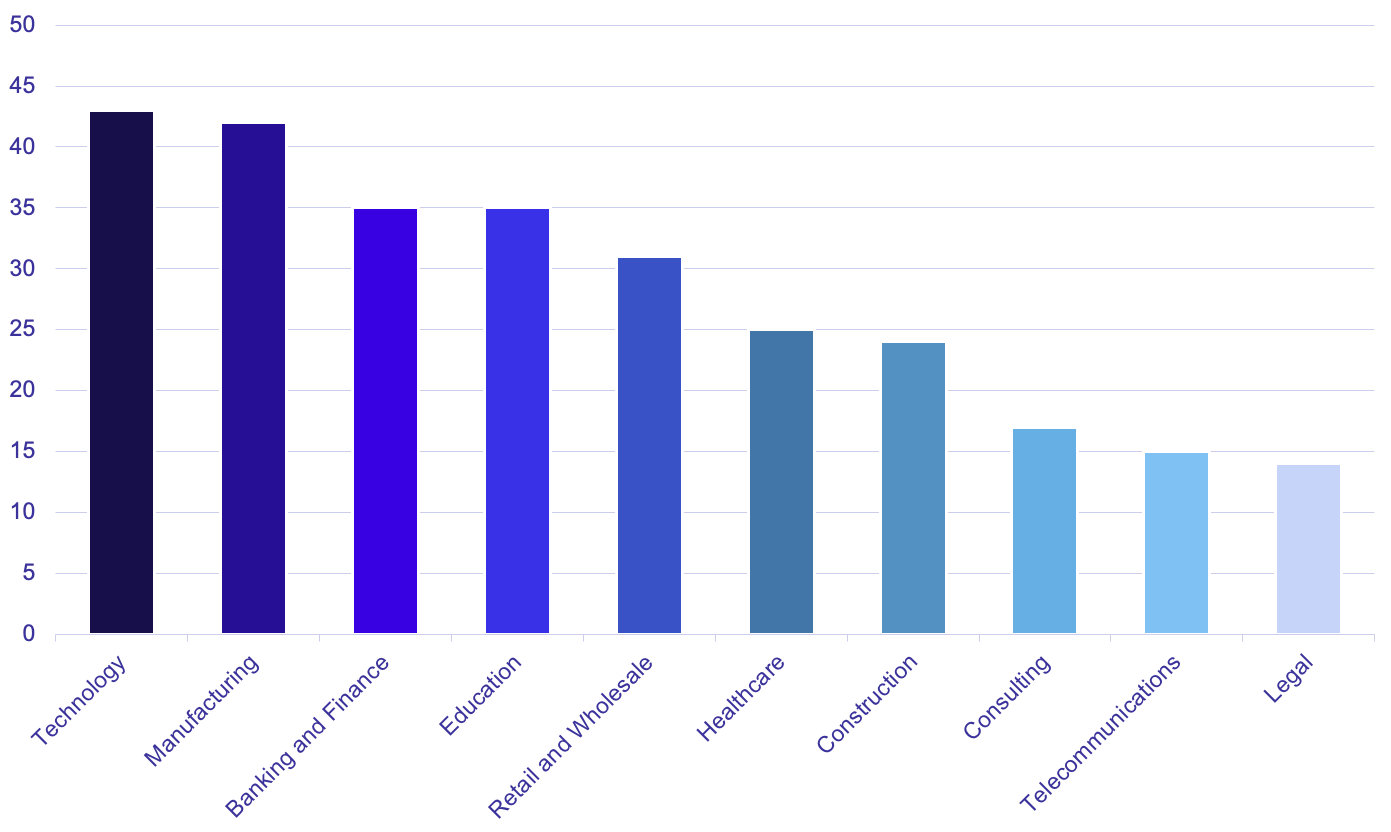
While the most frequently impacted industry verticals remain largely unchanged in May, GRIT continued to observe a previously-noted increase in posted victims belonging to the Education industry. From daycare centers to major universities, ransomware groups posted 35 unique victims in the education industry in May. This activity is driven at least in part by a recent influx in vulnerabilities affecting software commonly used in schools, such as the PaperCut MF/NG vulnerability. While some threat actors publicly pledge not to target organizations in sensitive industries such as Education and Healthcare, other groups seem to purposefully pick up the slack and pursue these targets for monetization.
We also observed four new ransomware groups, including 8Base, which claimed 67 victims in the past year. In total, the four newly observed groups represent nearly 18% of the victim posts we observed in May.
Ransomware Trends
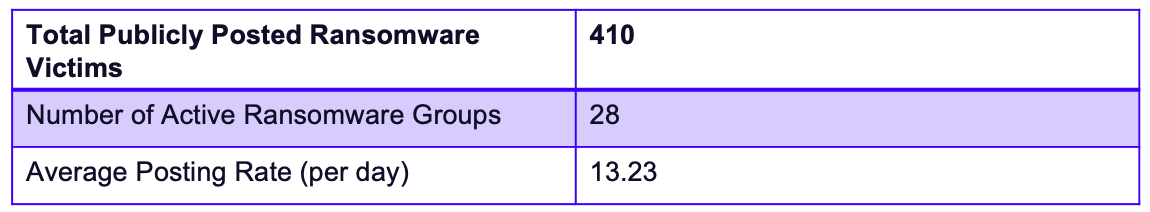
From April to May, GRIT observed a 13.57% increase in total affected organizations. May 22nd and 23 were the busiest days of the month, with the 23rd standing out due to 8Base’s (assessed by GRIT as a Full-Time group) bulk posting of 66 victims. Excluding that single mass publication, May 23rd drops to 28 victims, just below the 29 victims posted on the 22nd.
In total, GRIT observed a diverse slate of active threat groups this month, with 28 observed groups reporting victims.
Ransomware Victims by Country
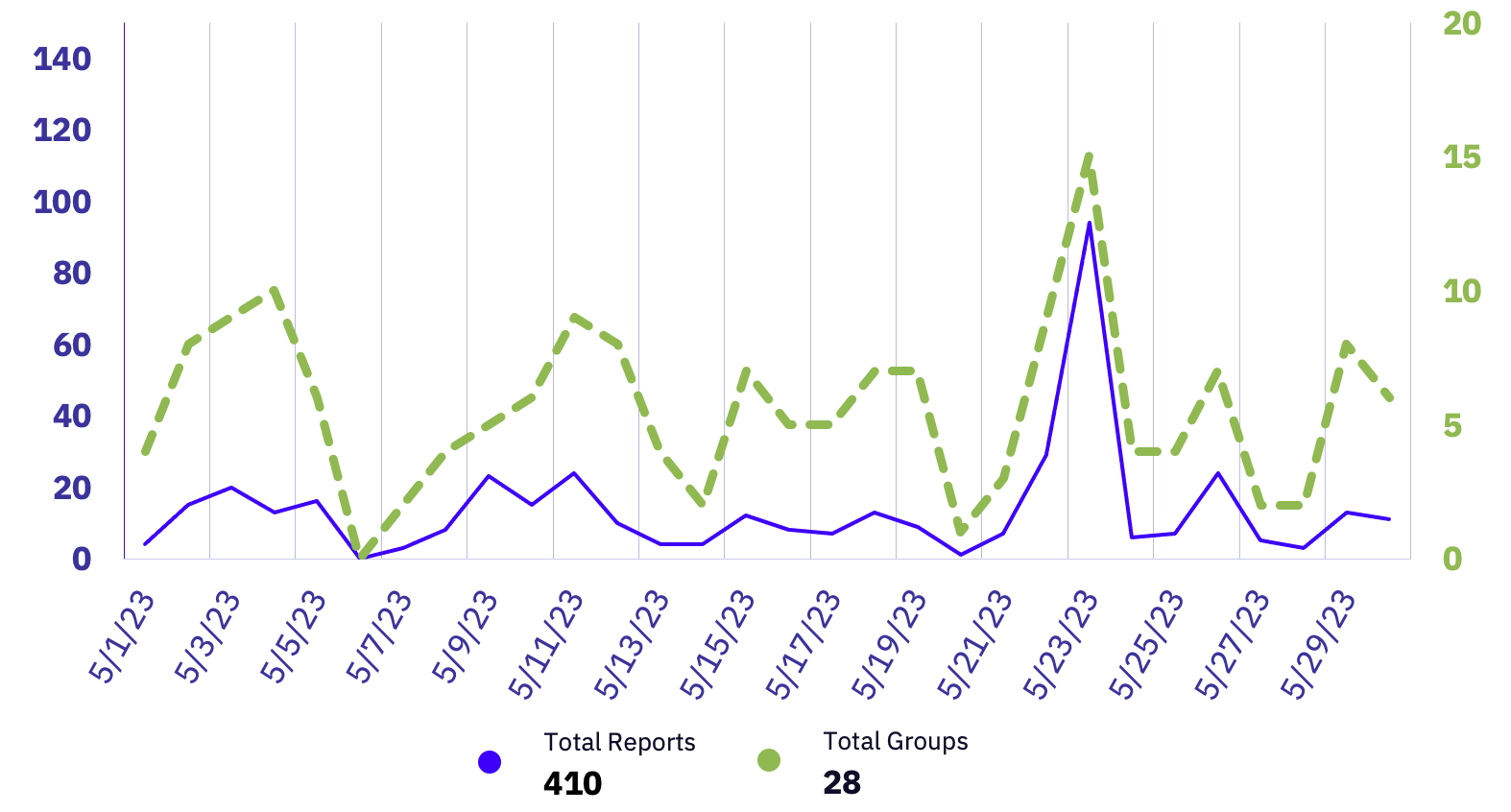
Attacks impacting the US vastly outpaced all other countries in GRIT’s observations, with 214 total claimed US organizations. Canada took a distant second place with 24 claimed victims.
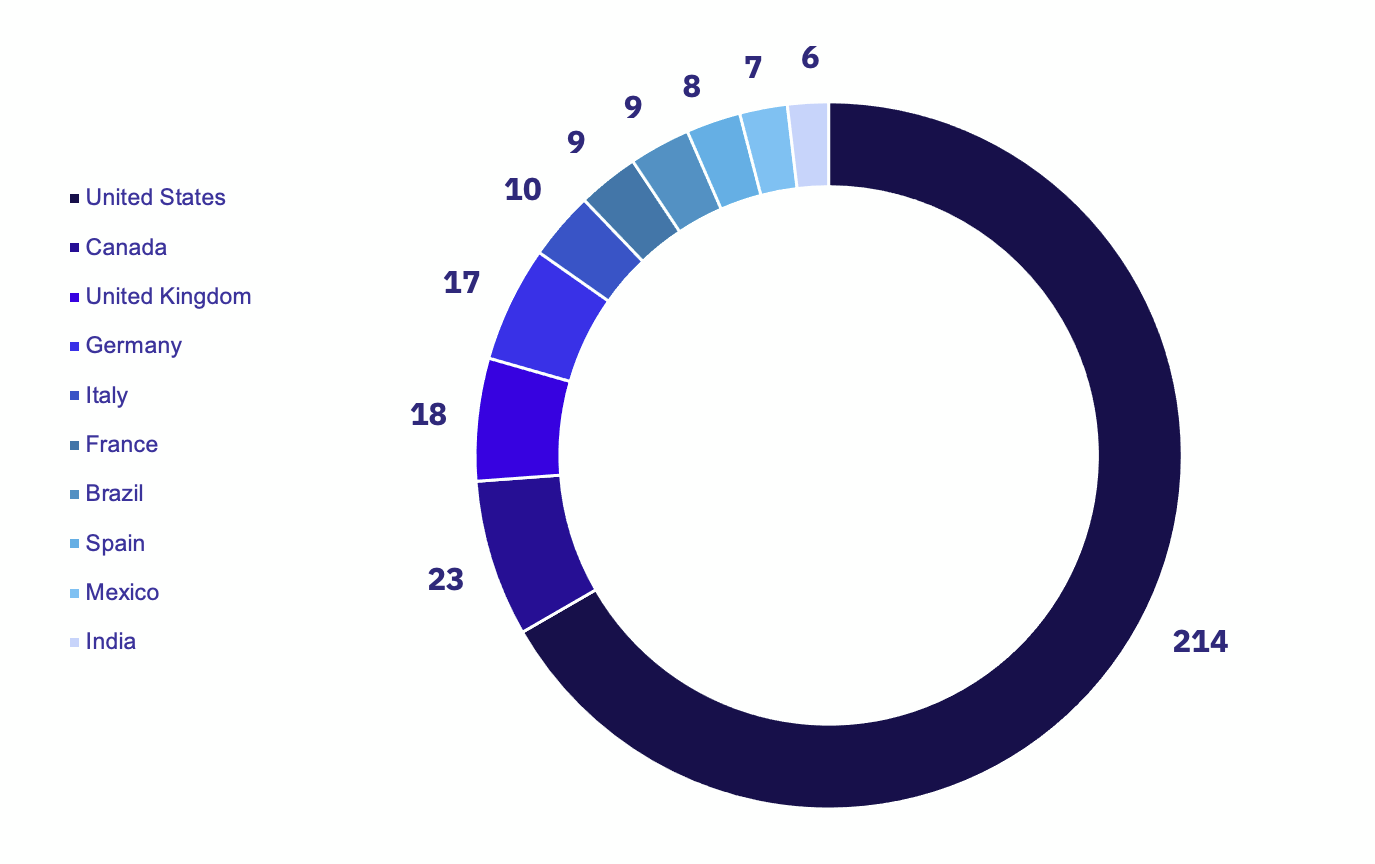
The groups most actively impacting the US were BianLian, Lockbit, and Alphv, all classified as Full-Time groups in the GRIT ransomware taxonomy.
Ransomware Victims by Industry
Among the most heavily attacked countries, ransomware groups were observed as impacting the following number of industries:
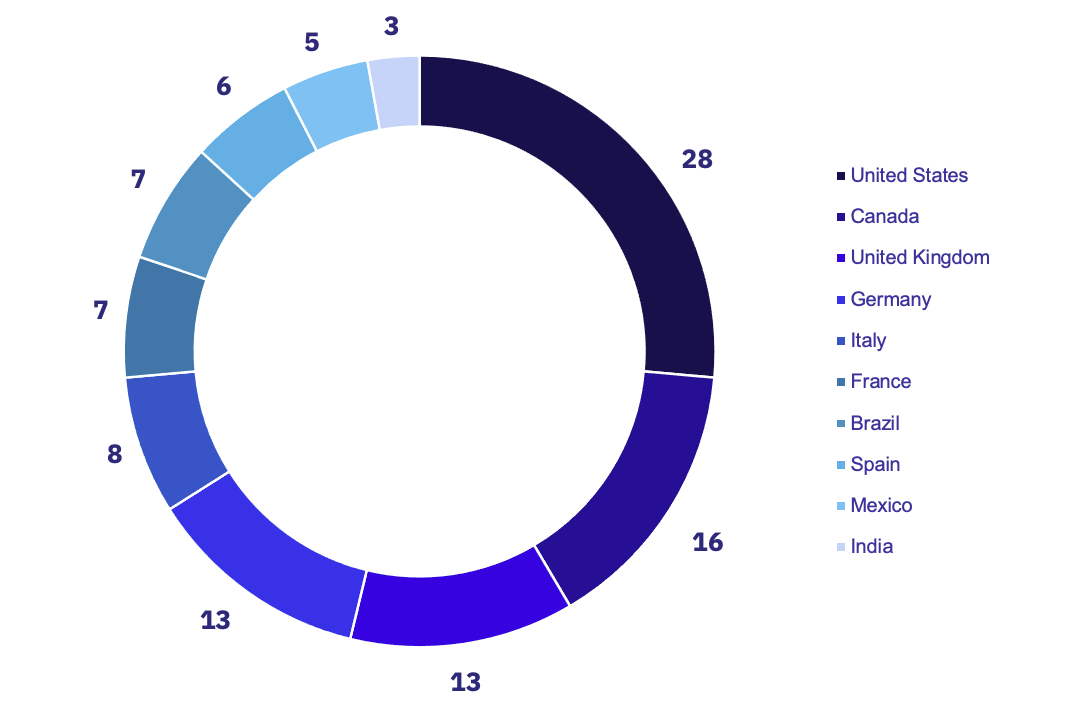
The top ten most impacted industries for May saw some shifts compared to April, with Food & Beverage, Engineering, and Real Estate being supplanted by Legal, Telecommunications, and Consulting. Among the most frequently impacted industries, the most active groups were Lockbit, Alphv, and BianLian. Within the most frequently impacted industries, companies in the US, UK, and Germany were the most frequently attacked.
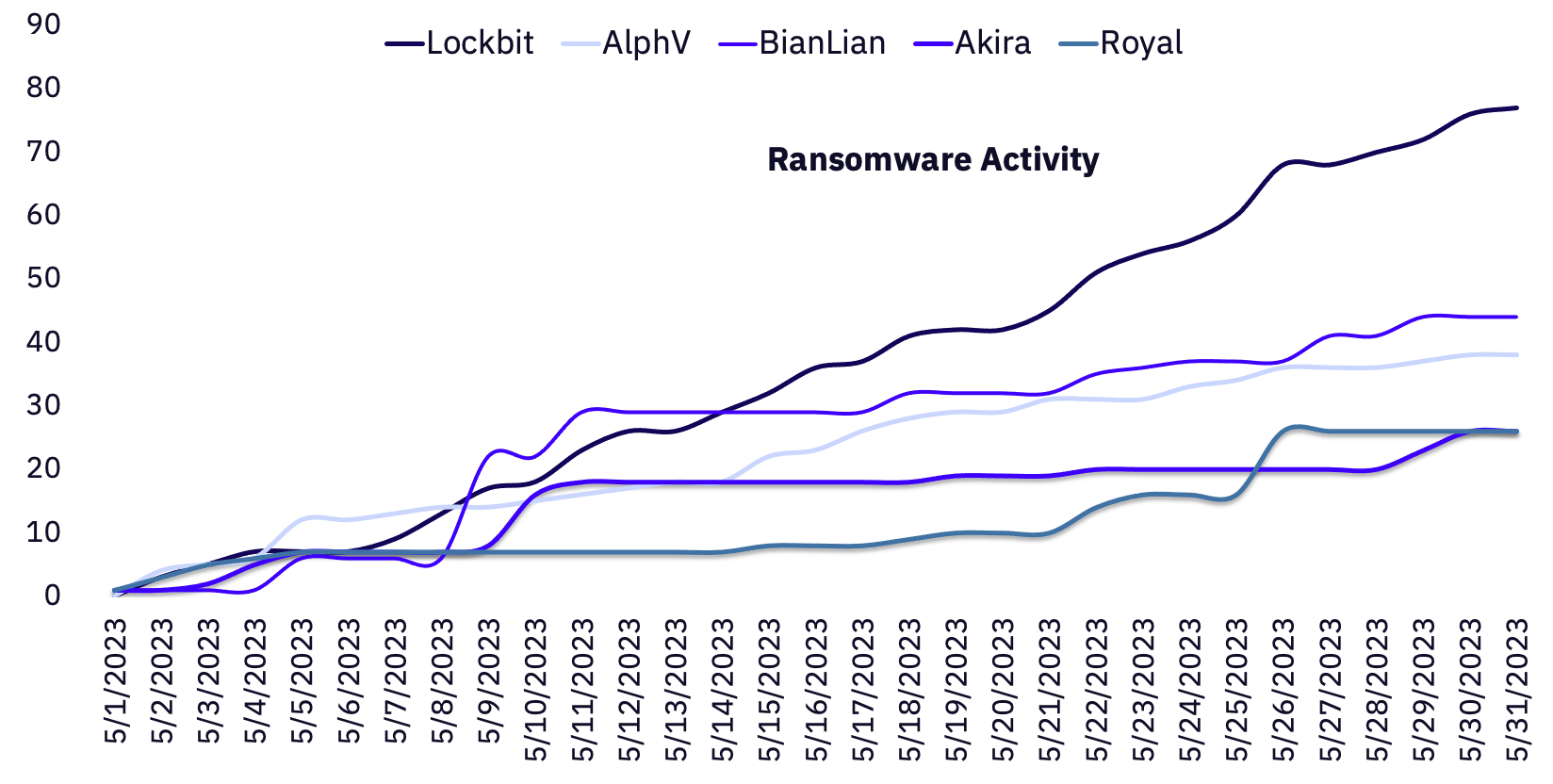
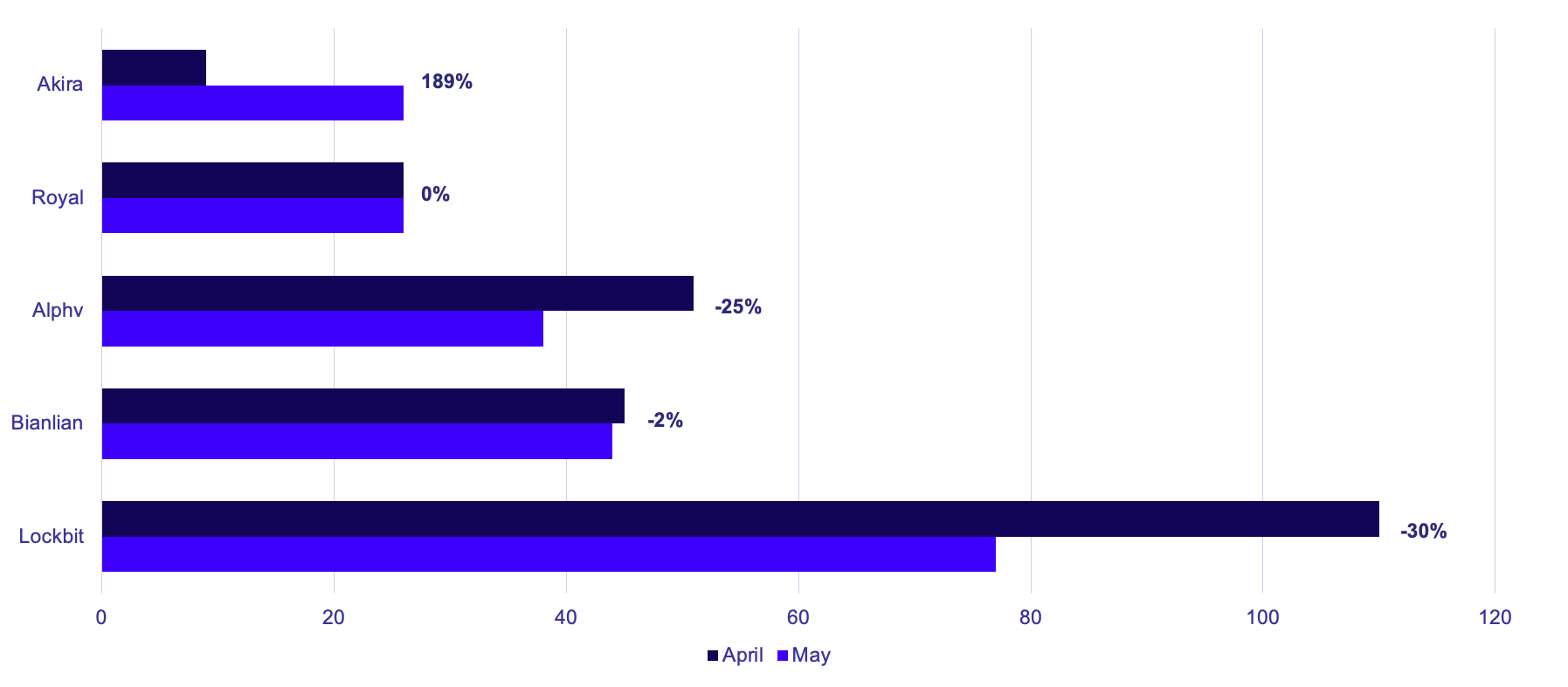
Cumulative Victims by Threat Group
Lockbit remains the most prolific ransomware group, despite a 30% reduction from 110 to 77 observed victims from April to May.
Alphv also showed a reduction in posted victims month-over-month, with 38 observed victims in May compared to 51 in April.
Unlike Lockbit and Alphv, BianLian’s victim posts remained consistent from April to May, posting 45 victims in April and 44 in May.
Threat Actor Spotlight: Akira (Ephemeral)
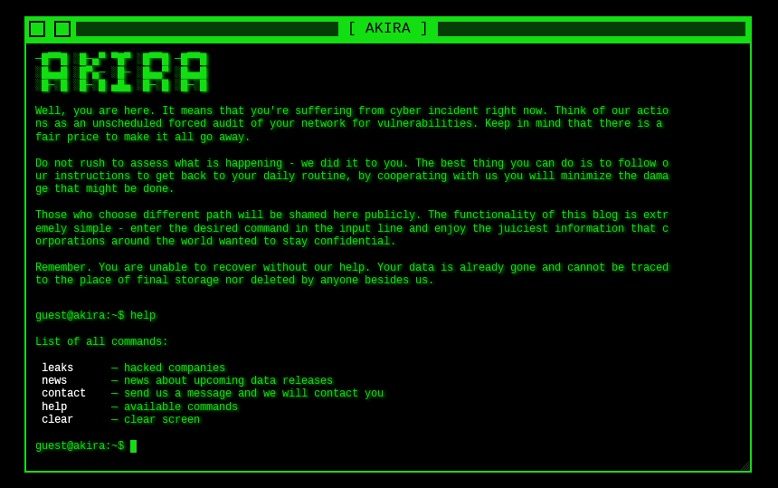
Akira ransomware has been a steady presence in the ransomware scene since their emergence in early April 2023. Their most notable distinguishing feature is the appearance of their data leak site, which was designed in jQuery to appear as an interactive command prompt, allowing users to enter commands to view the list of victims and associated data leaks. The stylized leak site contrasts with the tactics and techniques we have observed in use by Akira, which have led GRIT to attribute an overall low-medium level of sophistication to the group’s operations. Akira participates in the “double extortion” style of ransomware, exfiltrating data from their victims in addition to encryption. They will then threaten to sell or leak the stolen data on their dark-web site if a ransom is not agreed to.
Akira has disproportionately impacted Educational organizations, which represent 8 of their 36 observed victims. Whether intentional or not, Akira seems to be following the ecosystem-wide trend of pursuing this industry, as previously identified by GRIT in the Q1 2023 Ransomware Report.
Akira typically achieves initial access to their victim’s environment via compromised remote access credentials. It is unclear if the group purchases these credentials through marketplaces or public leaks, or if they directly acquire them through phishing or other methods.
We do not know whether Akira represents a new threat actor or a Splinter group, consisting of previous members from other groups. While we have observed similarities in the tools, tactics, and procedures used by Akira and other established threat actors, there is insufficient information to confidently establish any relationship. As of this report, GRIT classifies Akira as an Ephemeral group; however, their post rate indicates that they have enough victims and capabilities to rival many of the medium-sized, Full-Time groups.
Other Notable Ransomware Events
Previously Posted Victims Revisited by New Groups
Across its corpus of research, GRIT has occasionally observed a ransomware victim as claimed by multiple threat actors. In some instances, this occurs because an organization has truly been attacked by successful ransomware operations from multiple threat actors. For example, a Financial Services company from the United States has been claimed by three different tracked groups so far in 2023 – First posted by Clop as a part of their campaign of GoAnywhere exploitation in March, the same company was posted to both the RansomHouse and Abyss data leak sites in May. While collaboration between multiple threat actors cannot be ruled out, the simplest explanation for a victim appearing on multiple leak sites is that multiple threat actors have found themselves with access to the same victim networks at roughly the same time. In other cases, there may be reason to believe that different threat actors are either coordinating or factions of the same group (more on that in a minute).
We have considered the possibility that this near-simultaneous access to victim networks could be the result of less than scrupulous initial access brokers, but found this explanation less likely due to the importance of reputation and probable impact on future business in the ransomware ecosystem. We assess that the most likely cause of multiple threat actors impacting victim networks is the rapid weaponization and exploitation of emerging vulnerabilities. New, impactful vulnerabilities are discovered almost daily, and GRIT has observed a decreased operational delay from vulnerability identification to mass exploitation, particularly by more mature and competent ransomware operations. Once one adversary achieves access to an organization through an exploited vulnerability, there is often little standing in the way of another threat actor entering through the same access vector afterward. The resurgence of “extortion-only” tactics–where ransomware groups eschew encryption of victim data and instead pursue strictly exfiltration and extortion–actually serves to enable this trend by leaving the same unencrypted data vulnerable to repeat theft or subsequent encryption. Historically, if an organization was compromised by a single or double-extortion ransomware group, the threat actor would encrypt the victim’s data at rest in an attempt to coerce the victim into paying for decryption. If another threat actor happened to have access to this environment, they would be dissuaded from launching their own attack, as only already-encrypted data would be available to steal or hold hostage until backups were restored or other ransoms were paid. As more threat actors move to simplify their extortion efforts, temporarily vulnerable organizations may see more of these multi-pronged attacks.
Victim Overlap Between Snatch and Nokoyawa
On the same topic of victims posted to multiple leak sites, GRIT observed an unusual link between two groups that were previously considered unrelated. Going back as far as February 2023, Snatch and Nokoyawa have claimed at least 8 common victims, including the City of Modesto, California and Chattanooga State Community College. Without direct insight into these incidents or intimate knowledge of the relationship between the two groups, GRIT cannot accurately determine if these groups are working together to further extortion efforts or if they have separately targeted the same victims on multiple occasions. Cooperation between extortion groups is common, and posting victims to multiple leak sites may serve as a coercive tactic seeking to increase the chance of payment.
New Ransomware Groups Tracked by GRIT in May 2023:
8Base (Full-Time)
8Base entered the scene on May 14th with a post on Twitter stating “A lot of leaked data for the past year will be published soon. Enjoy.” They quickly followed through on this promise, posting 67 unique victims on their newly established data leak site in just two days (66 on May 23, and 1 more on the 26th). While many of the posted victims are backdated as far back as last year, it is unclear how long this group has been operating under this particular moniker. 8Base has primarily impacted the Banking and Finance industry, representing 18 of the 67 total victims posted to date. 8Base, like other groups, mainly impacts organizations in the United States, accounting for 32 of their 67 total victims. Unusually, 8Base’s second most impacted country is Brazil, with a total of 7 victims. Over the past year, Brazil was the 10th most impacted country by all ransomware groups; this outsized impact could indicate 8Base’s purposeful targeting of organizations in the South American country.
Malas (Ephemeral)
GRIT observed a new extortion group, referring to itself as “Malas“, performing mass exploitation of Zimbra, a business email and collaboration software. Malas differs from traditional ransomware groups in that they claim they are not asking for money themselves. Instead, Malas claims in their ransom note and on their data leak site that affected organizations may donate the ransom amount to “a non-profit that we approve of”. Despite this highly unusual extortion method, Malas has posted a list of companies they call “defaulters” which have not given in to their demands. It is unclear whether Malas will continue to operate in this manner or if this was the result of a one-time, opportunistic mass-exploitation.
Rancoz (Ephemeral)
Having only posted two victims so far, not much is known about how one of our newest tracked groups operates. One of the two observed victims is in the Technology industry, and the other is in Manufacturing. Researchers at Cyble with access to the group’s custom encryptor note similarities to that of Vice Society.
Blacksuit (Splinter)
With only one observed public victim in May, a Manufacturing company from the United States, Blacksuit may not seem like a grave new threat in the ransomware landscape. However, the maturity of their operations have not gone unnoticed. Multiple researchers have noted similarities in the code and tactics used by Blacksuit and the Full-Time group Royal, particularly in the structure and function of their VMWare ESXi encryptor; however, at this time we lack sufficient evidence to declare a definitive relationship between the two groups. Royal, a double-extortion group regularly among the top 5 most active, is known to have itself originated as a Splinter group of the notorious Conti ransomware gang.
Final Thoughts
At a macro level, the ransomware landscape has shown no signs of slowing down in May 2023. The total number of victims posted continues to climb month over month, closely following the quarterly trends identified by GRIT in previous reporting. An interesting trend to pay attention to as it develops is the increasing emergence of much smaller ransomware groups which exist ephemerally but seem to have access to a significant victim base. These small groups exist publicly for a short amount of time but are nonetheless very productive during their lifespan. Explanations for why certain threat actors are operating in this manner vary, but tracking these groups helps provide some insight into an already complicated ecosystem.
Throughout 2023 and continuing in May, GRIT has observed an increase in the number of extortion attempts against victims compromised by automated vulnerability exploitation. The exploitation of Remote Services (Mitre T1210) is nothing new to threat actors, who have been scanning for and exploiting vulnerable internet-facing servers for years as a method of initial access. Groups like Clop have recently taken this a step further by discovering that, with a zero-day vulnerability on the right software and some automation, they can exfiltrate data from a large range of victims and proceed to extort them at scale. While the number of groups with the capability to both find and exploit a zero-days at scale is limited, vulnerabilities available for purchase on the dark web could enable any group with enough resources to perform attacks in this manner. To address this attack pattern, defenders must be diligent in the patching and monitoring of internet-facing software. While Clop has shown a preference toward targeting secure file transfer software (like Accellion FTA, GoAnywhere MFT, and, as recently as 5/31, MOVEit), any piece of software designed around making sensitive data available via the internet is a strong potential target. With their observed success in these operations to date, more groups are likely to follow in Clop’s footsteps if the opportunity presents itself and barriers remain low.
Finally, looking ahead at the rest of the year, GRIT cautiously predicts a short period of reduced activity from many of the larger ransomware groups. Based on data from 2021 and 2022, GRIT observed lower numbers of victims and active groups compared to the baseline during the summer months of June, July, and August. With so many people involved, the causation behind this trend is difficult to identify, but the trend could indicate that some ransomware operators vacation or are otherwise indisposed once the weather gets warm in the northern hemisphere. Continuation of this trend is anything but guaranteed, especially as smaller and harder-to-track groups flood into the ecosystem.
The GRIT Ransomware Taxonomy
By subdividing ransomware groups, GRIT can obtain more detailed insights into how ransomware groups progress in their level of operational maturity and can classify and identify potential rebranding activity.
We distinguish ransomware groups by placing them into these four categories:
FULL-TIME
These groups have been active for nine or more months and often have months where they publicly claim 10 or more victims. Their standardized infrastructure and defined affiliate structure (if acting as Ransomware as a Service) lead to consistent TTPs and behaviors with only slight variations based on the ransomware operator.
REBRAND
These groups have typically been active for less than nine months, but their public posting rates regularly rival Full-time groups. TTPs for this type of group are more varied than a Full-time group, yet still project an organized and determined operational capability. If the rebrand wasn’t announced publicly, these groups’ TTPs will help identify their previous identity.
SPLINTER
These groups are established and have been active for 2-5 months with varied public posting rates. Their TTPs are varied, sometimes borrowed, and indicative of less experienced operators that are developing their brand and identity. If their split from another group wasn’t public information, their TTP overlap with known groups can give them away.
EPHEMERAL
These groups have been active for less than two months, with varied, but low, victim rates. These groups are often a “flash in the pan” and do not progress to more developed and mature group types.
There are multiple routes a group can take through the various classifications, and no one route is standard. While one group may begin as “Ephemeral” and move their way through the ranks to “Full-time,” another group may enter as a “Rebrand” as part of a larger obfuscation strategy to avoid attention from law enforcement.