
Vulnerability Management & Penetration Testing Solutions
Identify and Prioritize Your Vulnerabilities for Effective Remediation — Before Attackers Can Leverage Them
VULNERABILITY MANAGEMENT & PENETRATION TESTING CHALLENGES
How are You Mitigating Risk and Ensuring Your Security Controls are Working Effectively?
Zero-day and known, unpatched vulnerabilities are among the top most common initial attack vectors. Having an efficient, repeatable vulnerability management program along with offensive security services such as penetration testing, that identify gaps and test your controls is an effective way to help prevent cyber attacks.

50%
of organizations experienced more than 39 Web application attacks this year
Verizon 2023 Data Breach Investigations Report
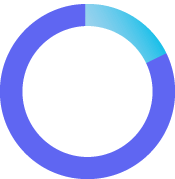
18%
Reduction in the cost of a data breach for organizations that deploy more intensive, risk-based analysis
Ponemon Institute 2023 Cost of a Data Breach
THREAT & ATTACK SIMULATION PRACTICE
Improve Your Defenses Against Any Adversary
Our Threat & Attack Simulation practice allows you to emulate an advanced adversary attacking your organization.
From traditional vulnerability assessments and penetration tests to advanced services such as red teaming, social engineering, continuous penetration testing and breach and attack simulation, we enable you to test your defenses against any type of adversary.
Our Vulnerability Management & Penetration Testing Commitment to You
We will help you identify security weaknesses and test your controls by:
- Tailoring our vulnerability management and penetration testing offerings to your specific organizational goals, ensuring that we provide the most value based on your budget, objectives, time constraints and/or security program maturity levels.
- Helping you navigate your political landscape, overcome technical hurdles and best position you to achieve your objectives.
- Inventorying, demonstrating and prioritizing risks.
- Identifying and addressing gaps in policies and procedures.
- Helping you understand real-world business impacts.
- Strengthening your security posture with realistic, actionable recommendations.
Additionally, our vulnerability management and penetration testing project teams have been in your shoes, enabling us to provide realistic recommendations and further guidance after the engagement is complete. The same team that helps you scope and tailor the project to your needs will help deliver the engagement and provide on-going support. After an engagement is complete, we don’t hand you a report and walk away; our job is not finished until you’ve reached your desired outcomes.
VULNERABILity MANAGEMENT & PENETRATION TESTING SOLUTIONS
Understand Your Security Gaps, Prioritize Risks and Improve Your Defenses
Identify & prioritize vulnerabilities & assess your organization’s readiness to withstand an attack from the most advanced adversaries.
Explore our Vulnerability Management & Penetration Testing solutions:
Our team of highly-certified and vetted threat and attack simulation experts provides a wide range of vulnerability management and penetration testing services to help you prioritize risks and improve your defenses.

Penetration
Testing
Gain real-world results to understand vulnerabilities, threats & gaps, & prioritize security investments.

Cloud Penetration
Testing
Identify current & emerging cloud-specific threats to your environment.

ICS Penetration
Testing
Bridge the IT & OT gap and gain a holistic view of your ICS security posture.

Social
Engineering
Use in-depth reconnaissance & hand-crafted campaigns to reveal realistic responses.

Red Team
Assessments
Sophisticated, multi-pronged attack simulation to identify threats before an adversary does.

Purple Team
Assessments
Prepare your security team for real-world attacks without the risk of an actual incident.

Active Directory
Security Review
Gain a baseline security audit of your AD environment & its key services.

Application
Vulnerability Scan
Evaluate your attack surface & gain insight into vulnerabilities inherent to your applications.

IoT Vulnerability Assessments
Gain an in-depth architectural review of your IoT ecosystem.

Vulnerability Management Services
Optimize your vulnerability management program and toolset through a risk-based approach.

Breach & Attack Simulation
as a Service
Fully managed threat intelligence program from conception to execution.

Penetration Testing
as a Service
Combine the power of manual & automated penetration testing.

Vulnerability Management
as a Service
Our experts identify critical assets, threats & vulnerabilities to close gaps.
VULNERABILITY MANAGEMENT & PENETRATION TESTING OUTCOMES
A Fundamental Component of Your Security Program
The combination of an efficient, repeatable vulnerability management program and threat and attack simulation services can help identify and prevent cyber attacks.
Understand Security Gaps
Identify security gaps & emulate adversary tactics to strengthen security policies & procedures
Prioritize Security Risks
Know where your greatest risks are at all times & implement the right controls
Strengthen Your Security Posture
Gain realistic, actionable recommendations to shore up vulnerabilities and weak security controls
Why GuidePoint Security
Your Elite, Highly-trained Team
More than 50% of our workforce consists of tenured cybersecurity engineers, architects and consultants. We are also highly certified across industry standards as well as hundreds of cybersecurity solutions.
Highly Trained, Highly Certified
Examples Include:




Industry Certifications





GIAC Certifications


Offensive Security Certifications
Your Trusted Advisor
Our team works side-by-side with you as your cybersecurity partner.
“I have a lot of personal trust in GuidePoint Security, which is a partner that really knows you, knows what’s important to you, knows how you want to move your organization, knows where your maturity point is and works with you to solve your most pressing challenges.”
Joey Johnson
CISO
Premise Health





