
GRIT Ransomware Report: April 2024
Additional contributors to this report: Nic Finn, Grayson North, Justin Timothy
April 2024 presented as an outlier amidst the preceding two years of reporting, with notable impacts on ransomware’s most prolific actors. Following their March “exit scam,” Alphv, also known as Black Cat, is nowhere to be found. LockBit, the most prolific ransomware group for 30 of the past 33 months, has moved to the fourth-most active ransomware group by victim volume. Since July of 2021, LockBit’s impact has only been bested by Cl0p’s mass-exploitation campaigns in March, June, and July of 2023. It is hard to overstate the significance of the decrease in LockBit’s operational tempo this month, which is equal to less than 25% of the group’s victim volume during the same period of 2023.
The result of the decreasing operational tempo amongst the landscape’s largest groups has been observed downstream, where newer Developing groups have increased their pace and “climbed the charts.” Play, an Established group less prone to the theatrics associated with Alphv and LockBit in recent years, has moved from a quieter but consistent position in the “top 5” to become April’s most prolific group. The Developing group Hunters International continued its three-month-long streak of increased operations, and Established group 8Base continues to follow a similar playbook to Play. Newer groups, including RansomHub, Ra Group, Dark Vault, and Inc Ransom now rank surprisingly high by victim volume, potentially reflecting an influx of new affiliates as well as the decreased influence of outlier numbers from Alphv and LockBit.
In this month’s Ransomware Report, we explore the operations of newer Emerging and Developing groups, including increased use of lower-quality malware, exploitation of historical vulnerabilities for “smash and grab” data extortion, and an outlier group, Muliaka, claiming to attack Russian organizations. For our threat actor spotlight, we look to RansomHub, a relatively new entrant to the ecosystem that has attracted attention for its alleged re-extortion of Change Healthcare, ostensibly the result of a scorned Alphv affiliate.
April has resulted in decreased total victim volume relative to preceding years, even though year-over-year monthly decreases are increasingly rare. We typically observe gradually increasing victim volume in Q1 and decreasing volume in portions of Q2. Based on historical precedent and the surprising impactfulness of law enforcement disruption in the mid-term, we now expect that total ransomware victim volume may remain steady or decrease in the coming months, though this may change depending on the efficiency with which former LockBit and Alphv affiliates find new homes and resume operations apace.
| Total Publicly Posted Ransomware Victims | 333 |
| Number of Active Ransomware Groups | 33 |
| Average Posting Rate (per day) | 11.1 |
Ransomware Trends
The first trimester of 2024’s trends have remained consistent with trends from 2022 and 2023, with an increase in victim volume in Q1, and a steady or decreasing volume in early Q2. However, the months of April to May resulted in decreased volume in 2022 and increased volume in 2023, complicating predictions for the same period this year.
This month’s victim volume showed a 15% decrease relative to March and a 7% decrease relative to April 2023, a rare outlier among our reporting.
By comparison, the number of active distinct ransomware groups tracked in April 2024 has remained constant at 33 relative to the preceding month of March (as covered in the GRIT Ransomware Report for Q1 2024). Year over year, the number of distinct groups operating in April 2024 has increased by 18% relative to April 2023.
The objective decrease in victim volume observed in April is almost certainly driven by the dissolution of Alphv and a decrease in victims claimed by LockBit, which typically “leads the pack” with the most observed victims each month. For example, in March 2024, LockBit claimed 57 victims, accounting for 15% of the month’s total. This number decreased by 60% to 23 in April, accounting for only 7% of observed victims.

Ransomware Victims by Country
The proportion of observed ransomware attacks attributed to US-based organizations remains steady at approximately 51%, consistent year over year and with March 2023.
Canada, Germany, and the United Kingdom continue to be the most impacted non-US countries, remaining relatively consistent at between 4.5% and 7% of observed attacks. However, we observed a lower diversity of impacted countries in April, down from 52 to 45, a 15% decrease.
We note that observed attacks against organizations in the Global South are often claimed by Emerging or Developing ransomware groups. Conversely, the most prolific Established ransomware groups focused disproportionately on the US, Western Europe, and Australia, which accounted for between 80% and 97% of victims posted by Play, Hunters International, and 8Base in April.


Industry Trends

Despite a slower month in terms of victim volume, the most impacted industry continues to be Manufacturing. Technology has reemerged as a frequently victimized industry, following a recent decrease in Q1.
We note the continued presence of Healthcare and Retail & Wholesale in the “top five” impacted industries, a relatively recent development that differs substantially from preceding years in which they were less frequently impacted.
Threat Actor Trends

Play has assumed the ”top spot” among ransomware groups, replacing LockBit. This displacement was not through increased operational tempo, but through the attrition of its peers, LockBit and Alphv. Play appears to post victims on a mostly weekly schedule of every 7-8 days, with ”batches” of posts on 4/4, 4/11, 4/19, and 4/26.
With 29 victims claimed in April, Hunters International demonstrated another aggressive month, second only to February 2024’s victim count of 30. Victims posted by Hunters have increased by 92% on average since February, potentially indicating an influx of affiliates.
8Base retained its place among the most prolific ransomware groups, as well as the most geographically dispersed victim base, including victims in Argentina, Indonesia, and South Korea. Like Play, 8Base also appears to claim victims on a mostly weekly schedule, posting almost exclusively on Mondays, as seen on 4/8, 4/15, 4/22, and 4/29.


Threat Actor Spotlight: RansomHub (Developing)
RansomHub is a Ransomware as a Service (RaaS) operation first observed in February 2024, which has quickly increased its operational tempo. The group employs double-extortion tactics, using a data leak site to post samples of exfiltrated data obtained before deploying an encryptor written in the Go programming language. We have observed threats by RansomHub to sell exfiltrated data on their branded data leak site (DLS) and instances where the group claims that data has been sold – a notable distinction from the more typical practice of posting such data openly. Possibilities for this distinct approach include the difficulty and cost of hosting stolen data, the group’s belief that data sales are more valuable than open posting, and the inherent pressure such activity places on the victimized organization to settle with the group.
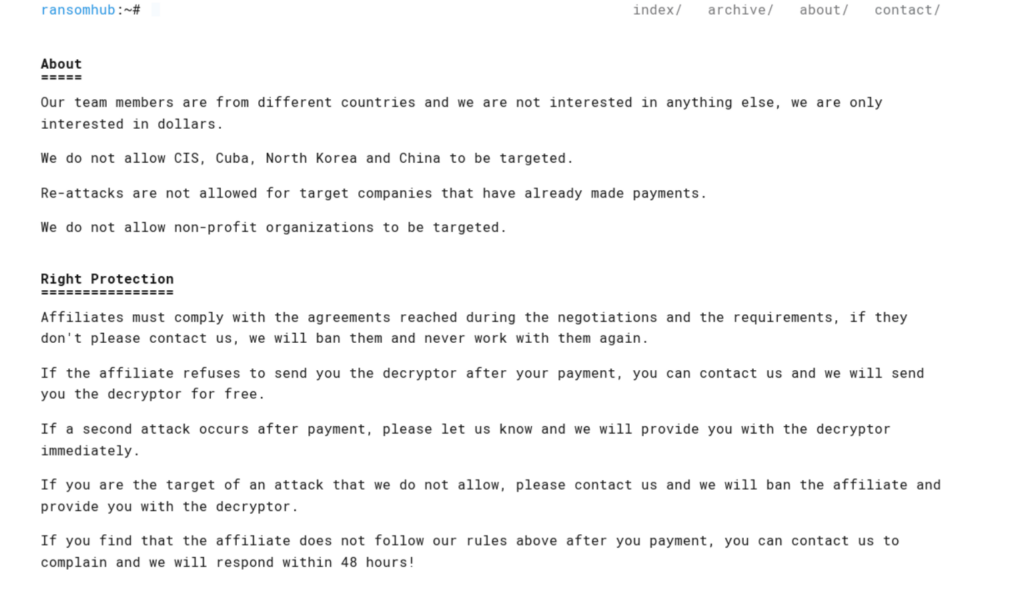
On its data leak site, the group expressly prohibits targeting organizations in the Commonwealth of Independent States, Cuba, North Korea, and China. It also prohibits targeting non-profit organizations or re-attacking victims who have previously paid. Interestingly, the group’s data leak site iterates that “affiliates must comply with the agreements reached during the negotiations and the requirements,” assuring victims that they may contact RansomHub’s administrators should an affiliate fail to do so.
The most likely explanation for RansomHub’s rapid February to April increase in the number of victims claimed is their posturing and advertising to attract displaced affiliates from Alphv and LockBit, a trend among several groups that we discussed in our recent blog “T-O-X-I-N-B-I-O – Ransomware Recruitment Efforts Following Law Enforcement Disruption.” RansomHub has claimed to security researchers that “many” former Alphv affiliates have moved to the new group, a claim seemingly supported by the group’s subsequent increased rate of victims.
In GRIT’s Q1 ransomware report, we highlighted RansomHub and other groups’ seemingly attempting to capitalize on law enforcement disruption operations by posting recruitment advertisements, with several lesser-known RaaS groups presenting themselves as attractive landing spots for would-be-forgotten cybercriminals. Specifically, we observed ramped-up recruitment operations from Medusa and Cloak amidst the more aggressively affiliate-friendly terms marketed by RansomHub. RansomHub, posting on the illicit forum “RAMP” as early as February, offered affiliates a generous 90% commission on victim payments, including a stipulation that affiliates receive victim payments directly rather than requiring payments first be “processed” by an administrator; we see this stipulation as likely intended to ameliorate the concerns of wary affiliates freshly “exit scammed” by Alphv.
RansomHub has apparently succeeded in attracting at least one valuable affiliate from Alphv – the same affiliate that allegedly attacked Change Healthcare. The affiliate, who uses the name “notchy” on illicit forums, was allegedly robbed of their share of a $22 Million USD ransom, which Alphv’s administrators absconded with as part of their “exit scam.” With the affiliate’s stolen data in hand and absent a payday, “notchy” took their business to RansomHub, which posted an advertisement of their new possession on their data leak site in April. Change Healthcare’s listing on RansomHub’s data leak site has since been deleted, though it is unclear whether this is due to an additional ransom payment or the data’s purchase by a third party. In the mid-to-long term, if RansomHub has genuinely attracted multiple Alphv affiliates, we expect the group to continue or increase its operations, with additional posts of victims to follow. We assess that this will depend on the profitability and attractiveness of RansomHub to any former Alphv affiliates, and note that additional, more reluctant former Alphv affiliates may be attracted to the group should it prove to be a profitable landing pad.
Other Notable Ransomware Events
Low-Level Groups Exploiting Atlassian Confluence Vulns
In line with our prior assessments that threat actors will continue to exploit vulnerabilities impacting public-facing corporate infrastructure, recent open-source reporting has detailed the exploitation of Atlassian Confluence Data Center and Server to deploy Linux variants of the Cerber ransomware. Specifically, attackers have exploited CVE-2023-22518, a critical severity (CVSS: 9.1) Improper Authorization Vulnerability, which allows an unauthenticated attacker to reset Confluence and create an administrator account for persistent access. This CVE was first published in October 2023, with exploitation observed since early November to deploy Cerber ransomware. Additional reporting from at least late 2021 indicates this ransomware has also been used to target other Confluence vulnerabilities.
These observations highlight the importance of vulnerability management and mitigation efforts. Recent exploitation of these dated vulnerabilities–despite more than six months since Atlassian made patches available and advised that “customers must take immediate action to protect their instance”–has continued to provide threat actors with successful avenues for attack.
These reports demonstrate the continued exploitation of vulnerabilities by ransomware actors, particularly well-known vulnerabilities, where patches have been available for a significant amount of time. Based on the public availability of Proof-of-Concept (PoC) exploits and detailed technical information published after initial waves of exploitation, long-term exploitation may be considerably easier for less technically skilled threat actors, including ransomware actors.
HelloKitty rebranded as HelloGookie

In April, multiple open-source reports detailed the alleged rebranding of the HelloKitty ransomware group as HelloGookie, operating under the new name on a new data leak site. HelloGookie’s administrators have declared the rebranding openly, providing sensitive data previously obtained by HelloKitty in 2021 as evidence.
A user with the name “Gookee/kapuchin0” announced the rebranding; we note that a threat actor using these usernames, in addition to the username “Guki,” was the developer of HelloKitty, as revealed in 2022 leaked conversations between the Yanluowang ransomware operation and a user under the “Guki” moniker. Some reports have also indicated a close relationship between this user and the Yanluowang ransomware group.
HelloKitty started operations in late 2020, claiming multiple high-profile victims, including game developer CD Projekt, Cisco, and a Brazilian energy company, CEMIG. The group gained attention for its ransomware operations, which included the deployment of Linux variants targeting VMware ESXi, distributed denial of service (DDoS) attacks, and mass exploitation of CVEs, including CVE-2019-7481, which impacted SonicWall SMA100 remote access appliances. We note that this apparent Rebrand differs from most ransomware Rebrands in that the former and contemporary group names are overtly linked and announced. Typically, Rebrands have been considered as a means to evade law enforcement scrutiny, with at least some effort made to obfuscate the continued operations of an existing ransomware group.
“Muliaka” ransomware attacking Russian businesses
Recent reporting from the Russia-based technology company FACCT indicates that a cybercrime group dubbed “Muliaka,” which translates to “Muddy Water,” has been conducting ransomware attacks against Russian entities since at least December 2023 (Note: We have no reason to link this translated name with the Iranian “MuddyWater” APT group). The report details a specific incident that occurred in January 2024, which resulted in the encryption of the Russian victim’s network. Investigators found few traces of the intrusion and were unable to identify the initial access vector, potentially indicating successful anti-forensic tactics generally indicative of sophisticated actors.
According to the report, Muliaka operators maintained access to the victim’s network for two weeks prior to deploying ransomware via the victim’s anti-virus solution. To achieve this, the attackers created an installation package within the anti-virus product, subsequently creating a task in the program to deploy the package. The Windows version of the Muliaka ransomware appears to be a modified version of the Conti ransomware encryptor, which was publicly leaked in 2020. Among the modifications observed were changes to the encryption algorithms and additional functionality to terminate system processes and services prior to encryption. We have not observed a data leak site nor Telegram channel associated with the group, which we would typically expect with a more mature ransomware group. We note that this could indicate a number of conclusions, including a nascent ransomware organization or a series of ad hoc operations not intended to continue for the long term.
We highlight this case as most contemporary RaaS groups operate under rules that prohibit the targeting of organizations headquartered in Russia and multiple former states of the former Soviet Union. These rules presumably exist to avoid attracting the attention of local security services. Increasing ransomware operations impacting Russian organizations would be expected to impact the risk calculus of Russia’s security service and willingness to overlook or condone global cybercriminal operations.
Sophos report on “Junk Gun” ransomware
In April, we released a blog titled “Awkward Adolescence: Increased Risks Among Immature Ransomware Operators,” which addressed a concerning uptick in ad hoc and opportunistic “low-tier” cybercriminals, often operating with a shifting or undefined “brand” and ransomware that was less easily attributed to a “mainstream” group or Ransomware-as-a-Service offering. Our report was followed by a distinct report from Sophos, “‘Junk gun’ ransomware: Peashooters can still pack a punch,” which highlighted “multiple examples of independently produced, inexpensive, and crudely-constructed ransomware, mostly sold as a one-time purchase rather than typical affiliate-based [RaaS] models.” We consider the two phenomena to be related and indicative of the reduced barriers to entry afforded by contemporary widespread cybercrime operations.
The Sophos report details the expression of interest by lower-tier threat actors in these products, as well as claims by users to have successfully used the lower-quality malware in real-world attacks against organizations, allowing for relatively unskilled actors to complete an intrusion and attack chain absent support of a core ransomware group or initial access broker. These attacks ostensibly breached lower-lying targets and would have attracted substantially smaller ransoms and, in at least some cases, almost certainly failed due to defensive measures or technical issues. However, the affordability of such tools coupled with the availability of publicly available leaked credentials–so-called “combo lists”– would almost certainly make this approach to ransomware more accessible, even at a low price point.
Phobos and our associated coverage of its use in our blog fits the bill in a similar way. Available at low cost even on low-tier forums and marketplaces, we have observed multiple incident response cases in which attackers using Phobos have attempted–and sometimes succeeded–in comparatively low-sophistication ransomware attacks against Small-to-Midsize Businesses (SMBs). These attack methods and associated tooling are less likely to succeed against larger, more well-defended businesses, but their use against smaller targets may still yield revenue or substantial profits if performed at scale.
Ultimately, this reporting and associated incidents serve as a reminder that smaller organizations also face threats from ransomware and other threat actors which prey upon them as central to a criminal business model. We also note the continued importance of patching and vulnerability remediation, as at least some portion of immature cybercrime operations appear to use historical vulnerabilities as a means of access, “picking up the scraps” of smaller organizations that have not applied patching even a year after the fact.
Final Thoughts
April 2024 may be remembered as the first month in which we clearly and unmistakably observed the emerging impacts of recent law enforcement operations on ransomware’s two largest players – Alphv and LockBit. The number of victims claimed by both groups over the past two years has drastically skewed cumulative ransomware data observable in the public domain, and their respective disappearance and diminishment would, in and of itself, be expected to lead to reduced victim observations in the short term.
Theory differs from practice, however, and as we have covered in recent ransomware reports, we expect that the flexibility of the Ransomware-as-a-Service (RaaS) model will instead encourage former Alphv and LockBit affiliates to seek a new home and resume operations, albeit with a potential period of reduced operations as affiliates realign their operations. This may be reflected in increased victim volumes demonstrated by several “mid-tier” Developing and Established ransomware groups in recent months, including RansomHub, but we lack sufficient corroborative all-source reporting to assert such a development at this time.
While we continue to track the ransomware landscape to determine long-term changes, we anticipate formerly ”mid-tier” Developing and Established ransomware groups to become increasingly visible, either due to the attrition of more prolific competitors or due to shifting affiliate alignment. In the former case, we would expect to see lower total victim volume in the short and mid-term, whereas in the latter, we would expect to see increasing numbers of claimed victims by groups that have historically had a lower operations tempo relative to their peers.
As this report was finalized, Operation Cronos, a joint international Law Enforcement operation led by the UK National Crime Agency (NCA), appears to have revitalized their earlier February 2024 disruption operation – bringing formerly seized LockBit data leak sites back online with countdowns and posts seemingly promising additional information on LockBit to be released in the coming days. Whether this information will further degrade LockBit as an organization remains to be seen, though the continued attention of law enforcement is unlikely to make LockBit an attractive destination for new affiliates in the future.
The month of April serves as a reminder to the threat intelligence community that imposition of punitive costs and removal or reduction of incentives, such as through disruptive law enforcement operations, can and does impact the ransomware landscape as a whole. Impacts may not be as far-ranging or complete as we would like, or occur all at once, but it is hard to deny the effects we have seen thus far in 2024. We are also reminded of the ways in which cybercriminal enterprises change and adapt to outside threats – whether by restructuring, dissipating, rebranding, or other means, we cannot expect that even the outright downfall of the landscape’s two largest groups will lead to the end of ransomware as a threat.
Should ransomware operations dissipate, restructure, or otherwise attempt to continue in the short and long term, effective and collective intelligence will be as imperative as ever to maintain situational awareness and effective defense. To this end, we look forward to the continued efforts, research, and information sharing of our partners and the wider community.
The GRIT Ransomware Taxonomy
By subdividing ransomware groups, GRIT can obtain more detailed insights into how ransomware groups progress in their level of operational maturity and can classify and identify potential rebranding activity.
We distinguish ransomware groups by placing them into these six categories:
EMERGING
This category is reserved for new ransomware groups within their first three months of operations. These organizations may be short-lived, resulting in an Ephemeral group; may be determined to have Splintered or Rebranded from an Established group; or may move on to further develop their operations and TTPs over time.
EPHEMERAL
These groups are short-lived, with varied but low victim rates. Observed victims are usually posted in a single or short series of large postings rather than a continuous flow over time. Ephemeral groups, by definition, terminate operations, spin-off, or rebrand within three months of formation. These groups may or may not have dedicated infrastructure (i.e., data leak sites and chat support) as part of their operations.
DEVELOPING
These groups have conducted operations for three months or longer, resulting in a recurring flow of victims. Developing groups do not appear to be directly linked to other ransomware groups as a Splinter or Rebrand but may include some experienced ransomware operators. Developing groups generally improve their people, processes, or technology over time by recruiting additional members, refining TTPs, or improving the quality of their associated ransomware and encryption. These groups generally have dedicated infrastructure (i.e., data leak sites and chat support) as part of their operations.
SPLINTER
These groups consist of a plurality of members from previously Developing or Established groups and may have formed either by choice or due to exclusion. These groups may be identified by very similar or overlapping TTPs and tooling or through HUMINT gathered through interactions with personas on the deep and dark web. Splinter groups differ from Rebrands by the continued existence of the original organization as the Splinter group operates.
REBRAND
These groups consist in whole, or in part, of former Developing or Established groups. Rebrands often maintain the same people, processes, and technology as the original group. Rebrands are generally undertaken in order to minimize attention from law enforcement or intelligence officials or to avoid negative publicity.
ESTABLISHED
These groups have operated successfully for at least nine months and have well-defined and consistent tactics, techniques, and procedures. Established groups often possess functional business units that enable sustained ransomware operations, with specialists focused on areas such as personnel, encryption, negotiations, etc. These organizations successfully employ technology and redundant infrastructure to support their operations.
There are multiple routes a group can take through the various classifications, and no one route is standard. While one group may begin as “Ephemeral” and move their way through the ranks to “Full-time,” another group may enter as a “Rebrand” as part of a larger obfuscation strategy to avoid attention from law enforcement.