
GRIT Ransomware Report: July 2023
Additional contributors to this report: Jason Baker, Grayson North, Justin Timothy
July revealed several interesting changes in trends, with an observed increase in number of active threat groups, impacted industries, and impacted countries, despite a considerable decrease in activity attributed to seven of June’s top ten threat groups. While the effect of Clop’s (Established) June mass exploitation of the MOVEit Transfer Zero-day vulnerability continued to produce additional reported victims, the remaining threat actors still claimed victims from 30 Industries and 53 Countries. This represents the second most affected industries and the most affected countries of any month in 2023.
Note: MOVEit Transfer was vulnerable to an exploit that allowed Clop to conduct mass exploitation against publicly accessible instances across the web. Progress publicly disclosed the vulnerability and provided patches on May 31. For additional details about this vulnerability, see the Progress Community article: https://community.progress.com/s/article/MOVEit-Transfer-Critical-Vulnerability-31May2023
While data in this report shows Clop’s reported victims from July, it is important to clarify that these victims are most likely to be primarily impacted by the MOVEit exploitation which occurred in June.
July’s shifts are led by a downward trending Lockbit (Established), historically considered the “top of the food chain” in the Ransomware-as-a-Service ecosystem. Continuing four straight months of reduced victim postings, July resulted in LockBit’s lowest number of posted victims of any month this year. Despite this fall, Lockbit maintains the second-highest reported victim count for the second month in a row.
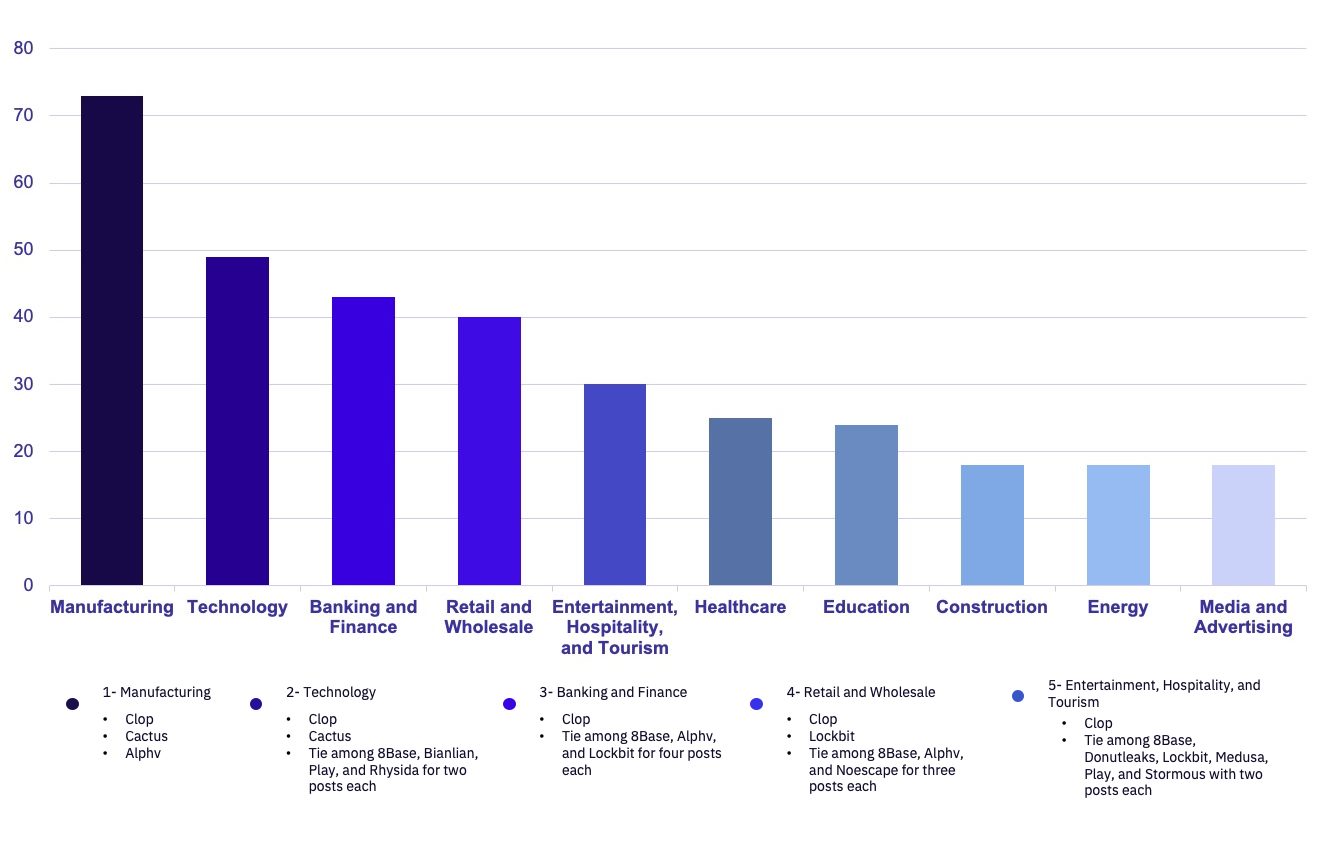
Clop’s activities heavily skewed this month’s impacted industries in favor of Technology, Banking and Finance, and Entertainment, Hospitality, and Tourism, all of which were more likely to use the MOVEit Managed File Transfer product. These industries represent the second, third, and fifth-most impacted industries when looked at holistically. However, when excluding Clop’s victims from our dataset, we observed these industries representing the fifth, seventh, and fourth positions overall. As usual, Manufacturing remains the most impacted industry by a wide margin.
While we first observed Cactus (Emerging) in our most recent quarterly report, July marks the first month where we have observed their posting of 18 victims, primarily in the Manufacturing and Technology sectors. Another newly monitored group, Knight (Emerging, Rebrand)–previously known as Cyclops–is now included in our dataset, with six posted victims spanning five industries, including Government and Healthcare.
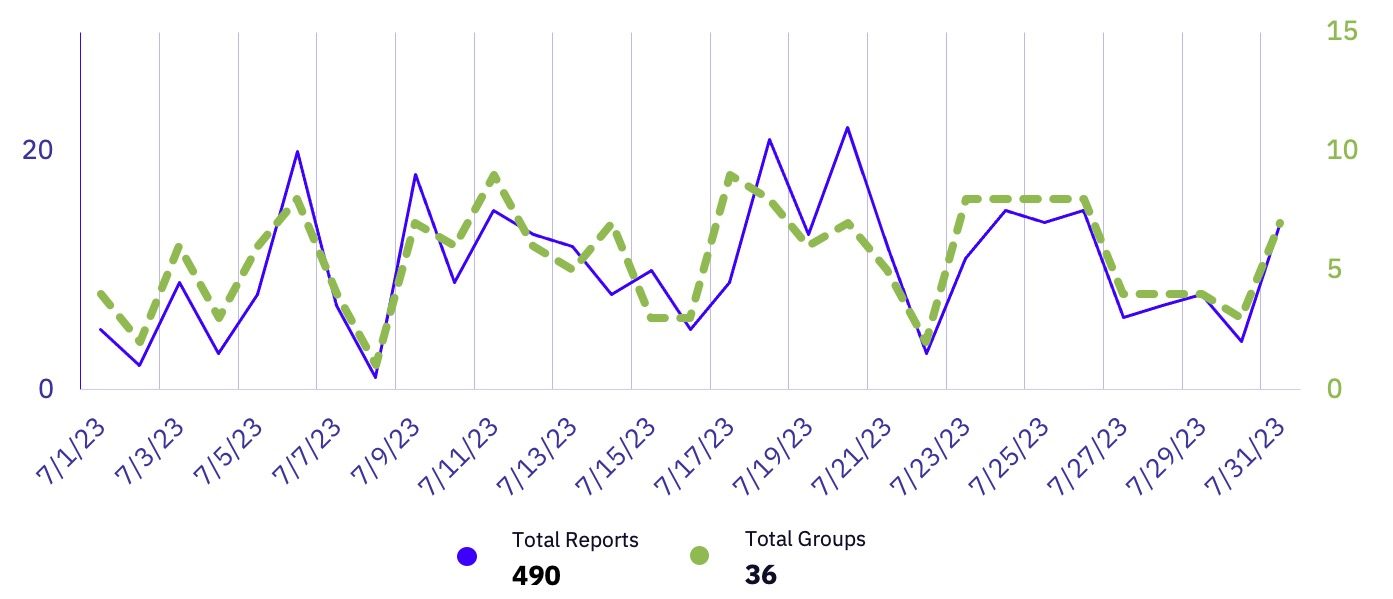
| Total Publicly Posted Ransomware Victims | 490 |
| Number of Active Ransomware Groups | 36 |
| Average Posting Rate (per day) | 15.8 |
Ransomware Trends
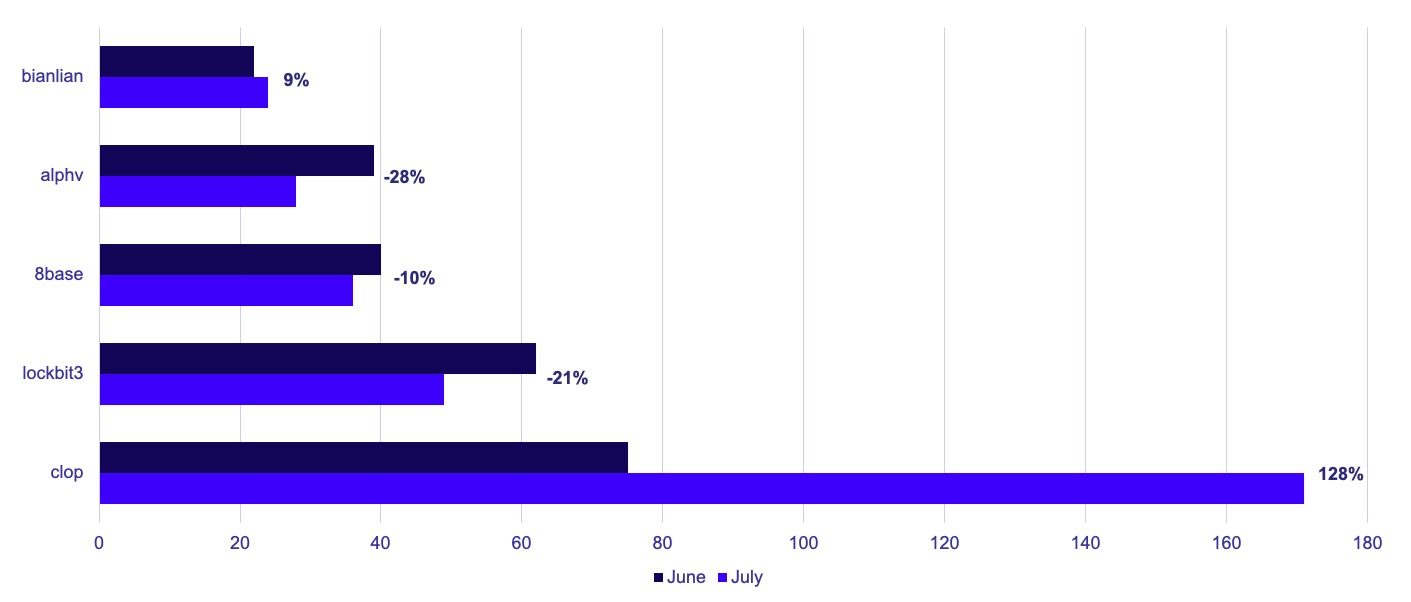
GRIT’s analysis revealed a notable 20% increase in the number of affected organizations from June to July.
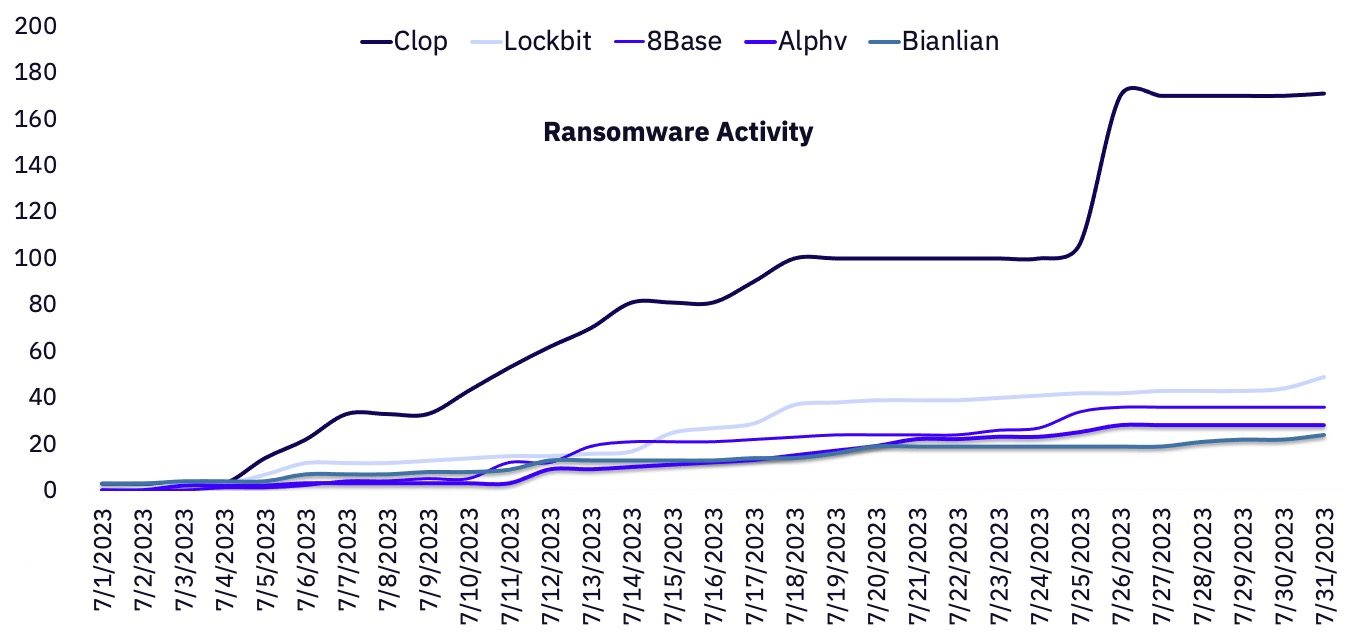
There was an increase of 80 victims compared to June. This includes 171 victims claimed by Clop (Established), marking a significant increase of 96 additional victims reported by Clop compared to June. If we exclude Clop’s engagement, the reported victim count for July actually shows a decline of 91 in comparison to June.
July’s most active day in terms of posted reports was the 26th, where a total of 79 reports were identified, spanning across 8 distinct threat actor groups. Notably, the lion’s share of these reports (64) could be attributed to postings made by Clop.
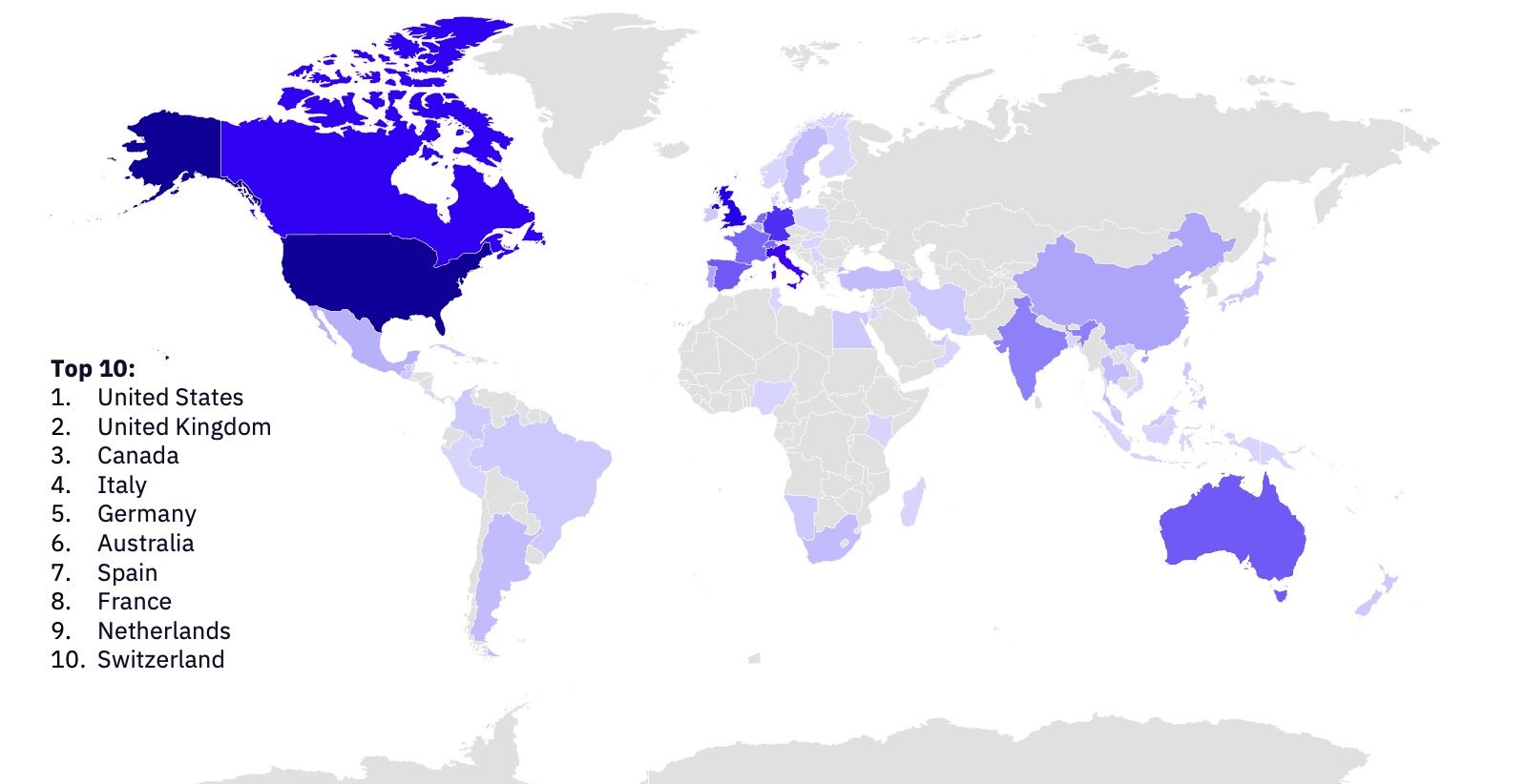
Ransomware Victims by Country
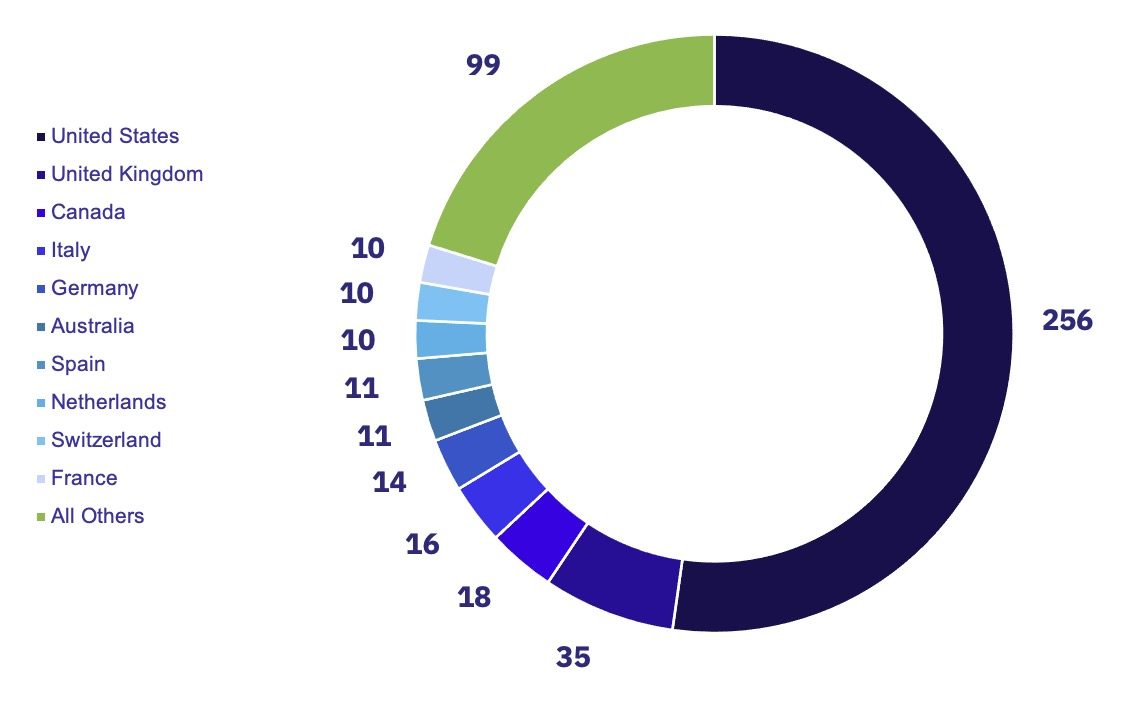
Like many previous months, ransomware attacks targeting the US once again vastly outnumbered attacks impacting other countries, with 256 attacks targeting US-based organizations. Attacks targeting organizations in the UK came in second with just 35.
The top three groups affecting US-based organizations were Clop, Play, and Lockbit, all Established groups. Clop’s inclusion in the top 3 is unsurprising given their massive surge in activity related to the MOVEit vulnerabilities, but it is notable that they beat out the usual top contender, Lockbit.
Ransomware Victims by Industry
Among the most heavily attacked countries, ransomware groups impacted the following number of distinct industries:
United States: 29
United Kingdom: 17
Canada: 13
Italy: 10
Germany: 7
Among the most heavily attacked countries, the most impacted industries shifted dramatically as a result of Clop’s (Established) mass exploitation of the MOVEit vulnerabilities. The Entertainment, Hospitality, and Tourism; Banking and Finance; and Technology industry victim numbers all saw spikes due to their common use of MOVEit software.
Cumulative Victims by Threat Group
The top three most active groups overall were Clop, Lockbit, and 8base. While both Clop and Lockbit are Established groups according to the GRIT Ransomware Taxonomy, 8base is still classified as an Emerging group.
In July alone, GRIT observed 171 posts by Clop. While this is the most activity published by Clop, most of their posted victims in July appear to be the result of their mass exploitation of the MOVEit Managed File Transfer product, which occurred in June 2023.
Lockbit’s observed activity has been steadily decreasing by 15-40 posts per month since April. Representative of this trend, LockBit’s number of posted victims has again dropped from 62 in June to 49 in July.
Despite reportedly operating since early 2022, 8Base first came to our attention in Q2 of 2023, at which point they began rapidly posting victims. 8Base continues its outsized performance as a relatively new Emerging group, performing among the top three groups with 36 posted victims in July
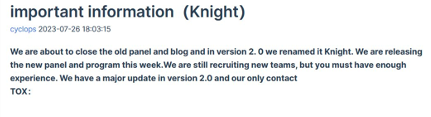
Threat Actor Spotlight: Knight, formerly known as Cyclops (Rebrand)

Cyclops ransomware, a Ransomware-as-a-Service (RaaS) group first observed in May 2023, announced their rebrand to “Knight” coinciding with “version 2.0” of their associated ransomware on 26 July. While rebrands are frequently undertaken in order to reduce law enforcement attention or negative publicity, Cyclops’ public rebranding as Knight appears to instead be an attempt to generate publicity.
Cyclops ransomware was historically known for its cross-platform compatibility, allowing it to impact Windows, macOS, and Linux operating systems. This rare level of flexibility, most often seen in more established groups, is a result of its use of the modern Go programming language for the Cyclops ransomware binary.
As a group, Cyclops has historically offered affiliates access to both their ransomware and a separate Go-based malware capable of stealing information from browsers, cryptocurrency wallets, VPNs, and other applications. Limited reporting previously identified Cyclops’ information-stealing malware as “Dot Net”, though we cannot verify this link or the use of the same malware post-rebrand.
Security researchers have noted similarities in Cyclops’ encryption logic and encoding techniques to those of Babuk and LockBit. Because both Babuk and LockBit have had their source code leaked in the past, we assess that cannibalization and repurposing of previously leaked source code could explain these similarities; we consider direct ties to either group, with Cyclops operating as a Splinter group, to be less likely.
Other Notable Ransomware Events
Everest (Established) Attempting to Purchase Access to Corporate Networks
In a post on their ransomware leak site on July 31st, the Established ransomware group Everest advertised an offer to pay insiders for access to corporate networks, likely to facilitate seemingly legitimate access in support of future ransomware operations against large businesses. This offer was set to expire on Aug 7th and included two email addresses and two Jabber accounts as contact information.
More Fallout from Clop’s (Established) MOVEit Zero-Day Exploitation
Publication of victim names and data have increased considerably following the announcement of mass exploitation of the MOVEit Transfer appliance, with Clop posting 171 victims in July. Clop has made considerable process changes to make their leaked data more accessible, including attempting to post some prominent victim data on a clear-web site, and switching to Torrent files for data leakage instead of Tor-hosted web servers.
New Ransomware Groups Tracked by GRIT in July 2023:
Cyclops/Knight (Emerging, Rebrand)
As mentioned in the Threat Actor Spotlight, Knight is an Emerging group to the ransomware scene, having posted their first victims in July, but their capabilities include executing ransomware across a diverse set of operating systems. Notably, they also utilize an info-stealer binary that collects files of interest based on extension and file name, compressing them into password-protected Zip files and staging for exfiltration.
Cactus (Emerging)
Cactus is an Emerging ransomware group that GRIT only recently observed as reporting victims through their Tor data leak site. Interestingly, Cactus utilizes a ransomware binary that is protected by an AES encryption key. The threat actors decrypt the binary at execution by providing the key as an argument, providing some defense evasion capability against antivirus software. Cactus threat actors rely heavily on PowerShell and have been observed using legitimate remote access tools to avoid detection.
Final Thoughts
While the total reported victim count is significantly higher than previous months, July saw a clear drop in total victims after excluding new reports from Clop’s (Established) MOVEit Transfer exploitation. The observation of 36 active groups in July, compared to only 28 in June, may indicate an effort by smaller groups to increase their presence. However, even with eight more groups showing activity in July, GRIT observed a decrease of 15 posts across ransomware groups’ sites, after excluding results from Clop.
Clop’s success in garnering media attention and impacting countless organizations through their mass exploitation of the MOVEit vulnerability may lead to similar large-scale mass exploitation campaigns by other threat actors relatively soon, especially ones impacting file storage services. As stated in our 2023 Q2 ransomware report, GRIT expects to see similar activity from other groups, provided they develop exploits of vulnerabilities impacting a large enough portion of organizations globally. Additionally, we anticipate ongoing sightings of new Clop victims for a little while longer as they continue to stage new data leaks and may be winding down negotiations with additional victims.
Finally, looking at the upcoming months and the remainder of Q3 2023, GRIT expects to see increased activity from smaller Emerging and Developing groups, with unique and ambitious attempts to find new vulnerabilities in organizations, such as Everest’s (Established) “opportunity” post seeking insider access to corporate networks. While these efforts may include novel methods, at least some of them are likely to prove successful, especially if threat groups effectively incentivize collaborators.
The GRIT Ransomware Taxonomy
By subdividing ransomware groups, GRIT can obtain more detailed insights into how ransomware groups progress in their level of operational maturity and can classify and identify potential rebranding activity.
We distinguish ransomware groups by placing them into these six categories:
EMERGING
This category is reserved for new ransomware groups within their first three months of operations. These organizations may be short-lived, resulting in an Ephemeral group; may be determined to have Splintered or Rebranded from an Established group; or may move on to further develop their operations and TTPs over time.
EPHEMERAL
These groups are short-lived, with varied but low victim rates. Observed victims are usually posted in a single or short series of large postings rather than a continuous flow over time. Ephemeral groups, by definition, terminate operations, spin-off, or rebrand within three months of formation. These groups may or may not have dedicated infrastructure (i.e., data leak sites and chat support) as part of their operations.
DEVELOPING
These groups have conducted operations for three months or longer, resulting in a recurring flow of victims. Developing groups do not appear to be directly linked to other ransomware groups as a Splinter or Rebrand but may include some experienced ransomware operators. Developing groups generally improve their people, processes, or technology over time by recruiting additional members, refining TTPs, or improving the quality of their associated ransomware and encryption. These groups generally have dedicated infrastructure (i.e., data leak sites and chat support) as part of their operations.
SPLINTER
These groups consist of a plurality of members from previously Developing or Established groups and may have formed either by choice or due to exclusion. These groups may be identified by very similar or overlapping TTPs and tooling or through HUMINT gathered through interactions with personas on the deep and dark web. Splinter groups differ from Rebrands by the continued existence of the original organization as the Splinter group operates.
REBRAND
These groups consist in whole, or in part, of former Developing or Established groups. Rebrands often maintain the same people, processes, and technology as the original group. Rebrands are generally undertaken in order to minimize attention from law enforcement or intelligence officials or to avoid negative publicity.
ESTABLISHED
These groups have operated successfully for at least nine months and have well-defined and consistent tactics, techniques, and procedures. Established groups often possess functional business units that enable sustained ransomware operations, with specialists focused on areas such as personnel, encryption, negotiations, etc. These organizations successfully employ technology and redundant infrastructure to support their operations.
There are multiple routes a group can take through the various classifications, and no one route is standard. While one group may begin as “Ephemeral” and move their way through the ranks to “Full-time,” another group may enter as a “Rebrand” as part of a larger obfuscation strategy to avoid attention from law enforcement.




























