Cybersecurity Awareness Month: The End of Phishing Attacks? How to Resist One of the Most Popular Cybersecurity Attacks
Author: Dan Cinnamon, Principal Solutions Architect, Okta
October is Cybersecurity Awareness Month. GuidePoint Security is proud to join the national effort, championed by the US National Cybersecurity Alliance (NCA) in collaboration with the Cybersecurity & Infrastructure Security Agency (CISA), to amplify essential cybersecurity practices under the 2025 themes: Stay Safe Online and Building a Cyber Strong America.
Synopsis:
Cybersecurity professionals dedicate their careers to defending against cyber attacks. They lock down their networks. They protect their devices. They have mature identity management practices. They employ multifactor authentication. They bolster all of this with robust educational programming for their user population. The list goes on. Despite all of these layers of security, phishing is still one of the most successful attack strategies employed by criminals today. Why is this? What can be done? The good news is that the identity industry has developed authentication technology that has been designed from the ground up to be highly resistant to phishing attacks. The bad news is that, as a cybersecurity professional, I rarely see this technology employed.
In this article, I will lay out a few popular phishing attack schemes, and how phishing resistant authenticators are designed to stop them. Finally, I’ll provide some tips and tricks for adoption within your organization.
The Warp
I’m a child of the 80’s/90’s, and like many of my peers – I loved playing Mario Brothers. The original. I played it for hours. I wanted to learn all of the secrets, find all of the hidden vines to climb to the heavens, and of course, brag to all of my friends about it at school. But one of my most fond memories was finding and exploiting the warp tubes. These secret rooms were the subject of many childhood legends. I remember the thrill I felt the first time I found the warp directly to world 8. Those were the days.
Why does this matter? Phishing attacks are a lot like these magical warp tubes. The most classic defense strategy in cybersecurity is to defend in layers. What if the attacker can warp past most, if not all of those layers? This is precisely what happens in a phishing attack. All of the password strength, all of the MFA, and all of the device policy is for naught if an attacker can manipulate this login process for their gain.
What’s worse is that phishing attacks target the most unreliable link in the chain… you and I. Yes, I said it. Even highly trained cybersecurity experts can fall prey to a phishing attack. Even if 999/1000 we don’t, all it takes is one time. Maybe we had a late night. Maybe we’re sick. Maybe we had an argument with a loved one. Life gets in the way, and we, as people, are not 100% alert, 100% of the time. In the past, many phishing attacks were pretty easy to spot, but there has always been a subset of attacks referred to as “spear phishing” attacks. This is where an attacker would target an individual, gather personal information about that person, and build an attack that looked incredibly convincing. It was actually a relatively expensive operation, and in the past was usually limited to highly valuable targets. Of course, now with AI, the cost of crafting these hyper-personalized attacks has dropped dramatically, so we can expect hyper-personalized phishing attacks to become the norm vs. the exception.
So what can we do about this? Read on!
The Methods
To set the stage for how phishing resistance works, I want to first lay out (at a high level) two of the most popular phishing attack strategies. It’s important to understand how these work to understand how to defend against them.
Typo Squatting Phishing Attacks
A typo squatting phishing attack mimics a real website but with intentional spelling errors or variations of legitimate addresses in order to trick users into visiting a fake site, often to steal personal information or install malware.
Breaking update: The VoidProxy phishing service is a real-world deep dive into this style of phishing attack.
This style of attack is the most popular one. Have you ever gotten a text message or email with a link to “fix something”? Looking closely at the link, you’ll notice something “off” about it. Maybe it’s netflix.jankydomain.xyz, or usps.postalservice.jankydomain.com (both completely made up examples, of course). It’s of course also possible to have the link “display” something valid, but the actual destination is fake – so the scam would be more difficult to notice until after it’s clicked.
So here’s a diagram that outlines how this attack works. One nefarious attribute of this attack is that it’s transparent to the user. Other than a malformed address in the address bar, the site they’re interacting with looks completely legitimate.
What happens next depends a little bit upon the security measures in place. If MFA is enabled, then the attacker can only impersonate the real person while the login session is active. If MFA is not active, then the attacker can simply login whenever they wish.
In both cases, a typical next step would be for the attacker to wield their power immediately to perform a password or MFA change – thus cementing their access for use in the future, or to further pass along or sell to other attackers.
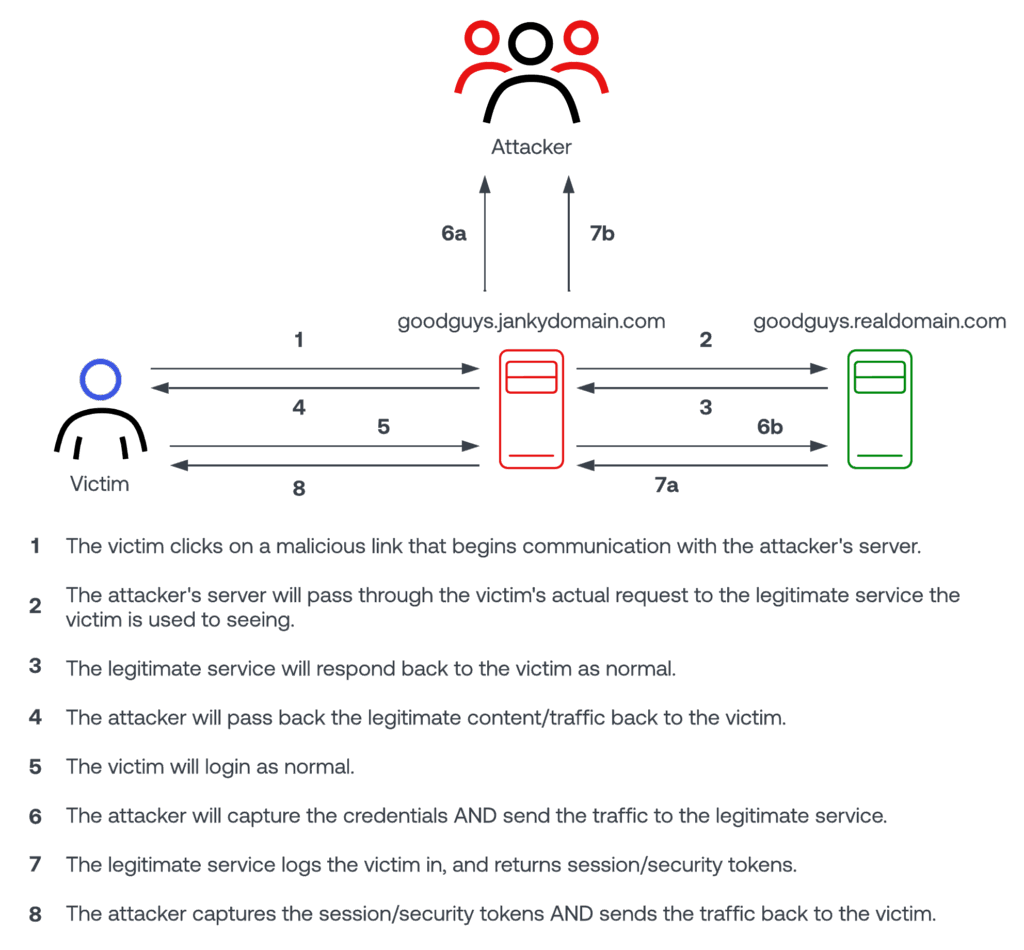
So the end result of this attack is that the attacker now has:
- The victim’s username and password
- The victim’s MFA one time code if applicable
- The victim’s logged in session ID/cookie
What happens next depends a little bit upon the security measures in place. If MFA is enabled, then the attacker can only impersonate the real person while the login session is active. If MFA is not active, then the attacker can simply login whenever they wish.
In both cases, a typical next step would be for the attacker to wield their power immediately to perform a password or MFA change – thus cementing their access for use in the future, or to further pass along or sell to other attackers.
MFA Fatigue Attacks
MFA fatigue attacks aim to bypass MFA by bombarding users with repeated authentication requests to overwhelm the user and make them approve an MFA request, even if they suspect it is fraudulent.
This style of attack requires the attacker to know the user’s primary credential (usually the password). At first glance this may seem like a high barrier, but with the prevalence of breached password databases and poor password hygiene for most people – obtaining a valid password for someone is not the challenge it once was. This attack also relies on “out of band” MFA, like a mobile app push-style MFA. This MFA strategy can be very convenient for end users, and is quite popular.
Here is a quick diagram that outlines how this attack works:
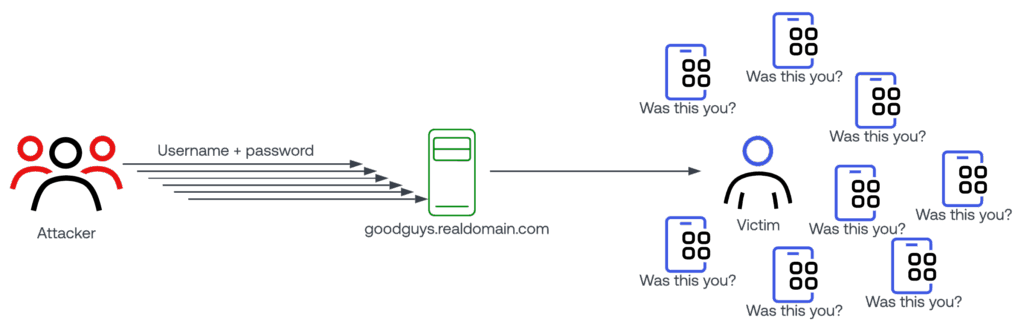
If this attack is successful, the attacker is now logged in as the end user. Like the other attack pattern, the first thing the attacker might try to do is perform an MFA reset, or some other activity to cement their access.
Mitigation Strategies
Both attacks can be mitigated to some degree without phishing resistant authenticators.
For typo squatting attacks, we often deploy end user training, as well as advanced network firewalls to help detect nefarious activity and stop them at the source.
For MFA fatigue attacks, MFA providers should be employing heuristic based or AI-based mechanisms to detect and filter nefarious MFA requests and provide mechanisms for end users to report suspicious activity.
The problem is that neither of these solutions prevent these attacks “by design”. They’re both somewhat reactive and prone to false positives (and negatives). An overzealous algorithm can easily prevent valid users from logging in properly, and overzealous network policies may prevent valid sites from working properly.
Don’t get me wrong – these layers of security are still absolutely necessary, and they are effective controls for many different types of vulnerabilities. I’m just saying that they aren’t a complete solution for phishing attacks.
Enter: The Phishing Resistant Authenticator
Ok, let’s get to the main entree. The meat and potatoes. Let’s talk about how a phishing resistant authenticator can be a powerful force in the defense against phishing attacks.
What I’m about to describe in this section was designed by the FIDO alliance. The FIDO alliance is a technology industry consortium that publishes standards and specifications for modern authentication protocols. The authentication specification I’m going to summarize is the FIDO2 specification, an open, phishing-resistant authentication standard. It uses public-key cryptography to replace passwords with strong, unique credentials called passkeys, which are bound to a specific online service, preventing cross-service tracking and ensuring that biometric data stays on the user’s device.
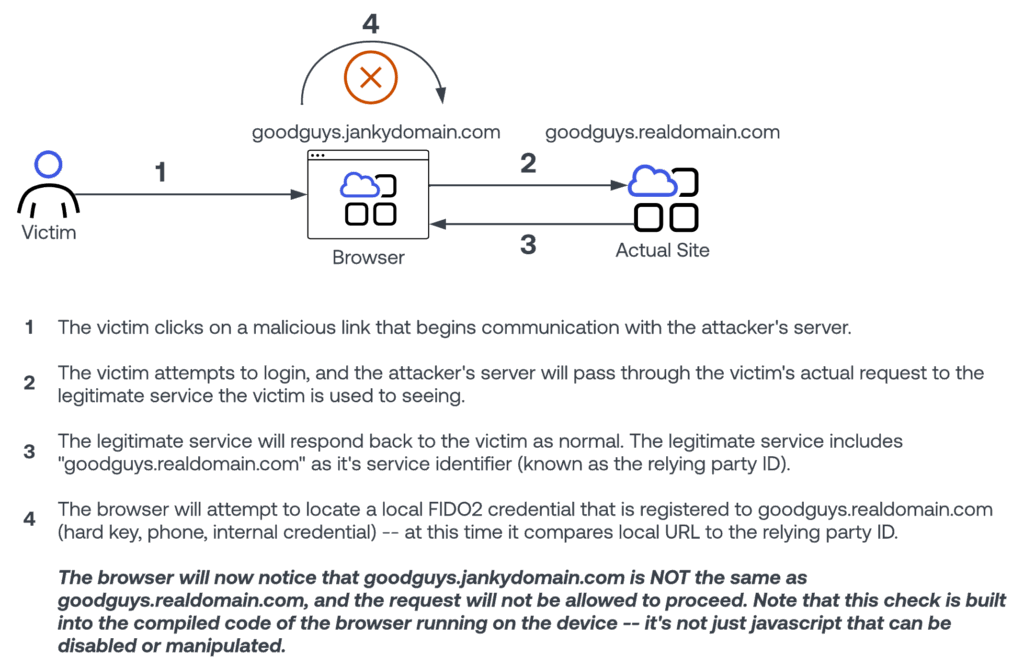
The above diagram illustrates a (very high level and simplified) phishing resistant authentication flow with FIDO2. There are two really important traits of this flow to highlight.
- Authentication Intent and Physical Presence
- Verifier Impersonation Resistance
Both of these concepts are covered in a lot more detail in the NIST 800-63b publication. https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-63b.pdf
Authentication Intent and Physical Presence
To put this very simply, this just means that an attempt to authenticate must be made by the physical credential holder, or at least in very close proximity to the credential holder.
Referring to my example above – let’s assume I’m an attacker halfway across the world, and I have your password. There’s very little stopping me from at least attempting to authenticate as you. I can flood your device with MFA push attempts. One mistaken acceptance of the push, and the attacker is in. As I said before, there are ways of making this more secure, with number verification strategies and identity provider algorithms to detect and prevent these attempts, but those are reactionary measures – not preventative measures.
With a FIDO2 authenticator, this attack vector is nearly eliminated. An attacker cannot even attempt to begin a FIDO2 authentication flow without the actual credential physically in hand.
With the addition of new passkey flows (passkeys are part of FIDO2), there are now bluetooth and QR code-based ways of presenting a FIDO2 authenticator in a wireless manner, so theoretically an attacker within a close proximity of a person could attempt this attack again. Even in such an instance, organizations can have policies to restrict which subset of FIDO2 authenticators are allowed to prevent even this (more unlikely) attack scenario.
Verifier Impersonation Resistance
Verifier impersonation resistance means that when a FIDO2 phishing resistant authenticator is enrolled for the very first time, it is hard-bound to an internet domain. For instance, if I enroll my FIDO2 authenticator against okta.com, it will only work with okta.com. This binding is supported by the browser. At both enrollment and authentication time, the browser is involved in the authentication process using a browser-provided API called “webauthn”. Often, “FIDO2” and “webauthn” are terms used interchangeably or together, but technically webauthn is a subset of the FIDO2 specification.
The main takeaway here is that, if I fall prey to a phishing attack, and I click on a link that takes me to okta.jankydomain.com, my FIDO2 compliant authenticator absolutely will not work. As an end user, I physically won’t be able to provide valid credentials for an attacker to steal. The browser will see the mis-matched site, and it will fail to find valid credentials for that site.
Multi-factor Authenticators
I’d like to close this section by highlighting an additional usability benefit to many FIDO2 phishing resistant authenticators – and that is the fact that many of them are multi-factor. Wait– what? What does that mean? Haven’t we been doing MFA for years now??
The NIST 800-63b publication I referred to earlier speaks to this in great detail, but I’d like to summarize with an example. Let’s say that my FIDO2 authenticator has a fingerprint reader. That physical device will have my fingerprint locally on it, and I must verify it in order to authenticate. When I do this – I, as an end user, present my FIDO2 credential once, and I present my biometrics once. In one action, I simultaneously performed MFA (something I have, and something I am). This is one of those cases where security can seriously make people’s lives better. Mic drop.
What’s Next?
I hope this article was helpful in de-mystifying phishing resistance! I’d like to leave you with a little bit more information to take as a next step in your journey towards a phishing resistant future. The first question you might have is – how do I get my hands on a FIDO2 authenticator? Let’s talk about that.
Device platform authenticators
The easiest place is to simply use the baked in FIDO2 authenticator in your existing device. As a standard all of the major OS and browser vendors already feature baked in support. In this case, the FIDO2 authenticator is your laptop/desktop/mobile device. The latest browser versions have switched to the “passkey” marketing term. If you use a passkey, you’re using FIDO2.
Roaming Authenticators
These are generally going to be in the form of a key that can be put on a keychain or lanyard. I’ll stay somewhat vendor agnostic here, but if you simply search for FIDO2 keys, you’ll find some well known brands that offer these keys.
Proprietary authenticators
While FIDO2 is the most prolific, there are solutions like Okta Fastpass, which are phishing-resistant authenticators. They take security one step further than FIDO2 in that it also can be used to assert device ownership and device security posture, among other things. So, while we fully support and embrace FIDO2 authenticators, there are scenarios where further security can be beneficial.
How Do I Start?
As you might expect, simply having phishing resistant technology available is only one piece of the puzzle. Acquiring and implementing this technology within an organization requires experience and a smart strategy to navigate the transition. If you want to learn more, visit us at okta.com. Ensuring your organization is prepared to defend against these attacks is where a trusted advisor like GuidePoint Security comes in. Read more about GuidePoint’s phishing services here.
