
Identity & Access Management
(IAM) Services
Control User Access to Critical Information and Systems - Without Impeding Business Operations
IAM CHALLENGES
How Are You Using IAM to Enable Business Agility, While Improving Security?
The modern business landscape is a competitive one, however, scaling too quickly – especially in today’s world of hyperconnected devices, applications and points of access – leaves you with an ecosystem that is unnecessarily complicated and practically bursting at the seams. By properly mapping out and implementing an Identity & Access Management program, you can streamline user access, improve operational efficiencies and reduce your risk.
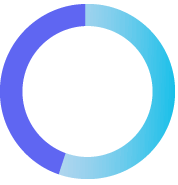
54%
of all attacks are initiated via compromised credentials
CISA Analysis: Fiscal Year 2022 Risk and Vulnerability Assessments

$4.62m
is the average cost of a breach due to stolen or compromised credentials
Ponemon Institute 2023 Cost of a Data Breach
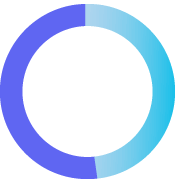
49%
of breaches involved the use of stolen credentials
Verizon 2023 Data Breach Investigations Report
Identity & Access Management Solutions
IAM Services That Help You Realize a Return on Investment
Our IAM practice helps organizations secure identities across on-prem, hybrid and cloud environments.
Whether it’s Identity Governance & Administration, Access Management, Privileged Access Management or Customer IAM, our team ensures that the right people have the right access to get their jobs done in a secure manner.
Our Identity & Access Management Commitment to You
We will help you raise the IAM bar by:
- Automating joiner, leaver and mover user lifecycle processes, ensuring efficient provisioning and de-provisioning and improving access certification for a better user experience.
- Seamlessly managing access to improve business users’ experience and reduce risk of unauthorized access through capabilities such as single sign-on, multi-factor authentication and federated single sign-on for robust authentication and authorization.
- Establishing a strategic risk management program built on a security framework to effectively manage and grow the program and ultimately allowing you to make faster, more risk-informed business decisions.
- Evaluating, deploying and managing your Privileged Access Management solution to govern the lifecycle of privileged users as well as implement best practices to reduce the associated risk.
- Guiding you through the CIAM implementation process, focusing on streamlining user registration, enhancing data security and compliance and gaining valuable customer insights.
IAM SERVICES
Enable Business Operations Through Access Governance & Process Automation
Explore our IAM services:
With our help, you can improve business agility by reducing operational costs through process automation and enhancing user experience and productivity through self-service—all while improving your security posture and mitigating risk.

Advisory
Services
Assess your IAM setup & improve your program via roadmap development, architecture reviews, health checks, & PAM, Zero Trust & Passwordless architecture workshops.

Implementation
Services
Automate & simplify your IAM program by ensuring continuous management & optimization of your IGA, PAM, Access Management & CIAM solutions.

Zero Trust
Workshops
We help facilitate your organization’s journey towards zero trust adoption through iterative, manageable steps.

Access Management
Identify & implement access management solutions that best align with your current & future needs.

Identity & Governance Administration (IGA)
Automate lifecycle processes to improve efficiency, user experience & security posture, while reducing risk & cost.

Privileged Access Management (PAM)
Define processes & implement the right PAM solution to manage the lifecycle of privileged accounts.

Customer Identity & Access Management (CIAM)
Focus on streamlining user registration, enhancing data security & compliance, & gaining valuable customer insights.
Identity as a Service
A robust solution for the complex challenges of identity management, focusing on optimizing resources, enhancing user experience, & ensuring security.
IDENTITY & ACCESS MANAGEMENT OUTCOMES
Improve Operational Efficiency While
Reducing Risk
Our IAM services help ensure your IT staff is armed with the necessary tools to manage and monitor user roles and activities and to consistently enforce your program-defined policies.
Improve Information Sharing
Share information & improve collaboration among applications, devices, & business units
Proactively Identify & Mitigate Risk
Flag policy violations & eliminate improper access privileges without searching through distributed systems
Develop Strong Security Policies & Practices
Meet privacy & protection regulations with high-quality security practices & policies that mitigate data breaches
Lower Service Costs
Eliminate outsourcing & the cost of managing obsolete, unreliable systems & avoid the pitfalls of regulatory violations
Why GuidePoint Security
Your Elite, Highly-trained Team
More than 50% of our workforce consists of tenured cybersecurity engineers, architects and consultants. We are also highly certified across industry standards as well as hundreds of cybersecurity solutions.
We understand that delivering successful IAM programs requires key personnel like business analysts, architects and developers, as well as functional expertise in key lifecycle and compliance-related processes. Our team of certified experts has assisted organizations across various industries with designing and implementing large-scale IAM projects.
Highly Trained, Highly Certified
Examples Include:




Okta Certifited






IGA









PAM
Your Trusted Advisor
Our team works side-by-side with you as your cybersecurity partner.
“GuidePoint Security is basically family. They’re always there when I need them. At the end of the day GuidePoint is always there to help and that’s how they add value.”
Mark Gilman
Security Manager



