
GRITREP: 0APT and the Victims Who Weren’t
Bottom Line Up Front (BLUF):
- GuidePoint’s Research and Intelligence Team (GRIT) assesses with high confidence that the victims claimed by “0APT” are a blend of wholly fabricated generic company names and recognizable organizations which threat actors have not breached. GRIT has observed no evidence that these victims were impacted by a threat actor associated with “0APT”, including through first-hand reporting.
- 0APT is likely operating in this deceptive manner in order to support extortion of uninformed victims, re-extortion of historical victims from other groups, defrauding of potential affiliates, or to garner interest in a nascent RaaS group. We cannot rule out the possibility that 0APT or associated actors may conduct real attacks in the future.
- 0APT emerged as a Data Leak Site in late January 2026 and quickly claimed over 200 victims in the course of a week. After security reporting emerged highlighting the number of victim organizations and implausible or fabricated organization names, the Data Leak Site went offline on February 8, before returning on February 9, with a much narrower slate of 15+ very large multinational organizations.
- Alleged victims of 0APT should consider activating their Incident Response Retainer or internal investigative procedures but are advised that in the absence of a ransom note, encrypted files, or any form of communication from the group, their post on 0APT is almost certainly entirely fabricated rather than representative of an undetected intrusion.
0APT emerged on our radar on January 28, immediately and continuously posting a staggering 200+ victims over the course of the following week. Typically, new groups with a high operational tempo out the gate signals a “Rebrand” or “Splinter” of another Established ransomware group, in which experienced operators simply continue their operations under a new name. So of course, we were interested in learning more.
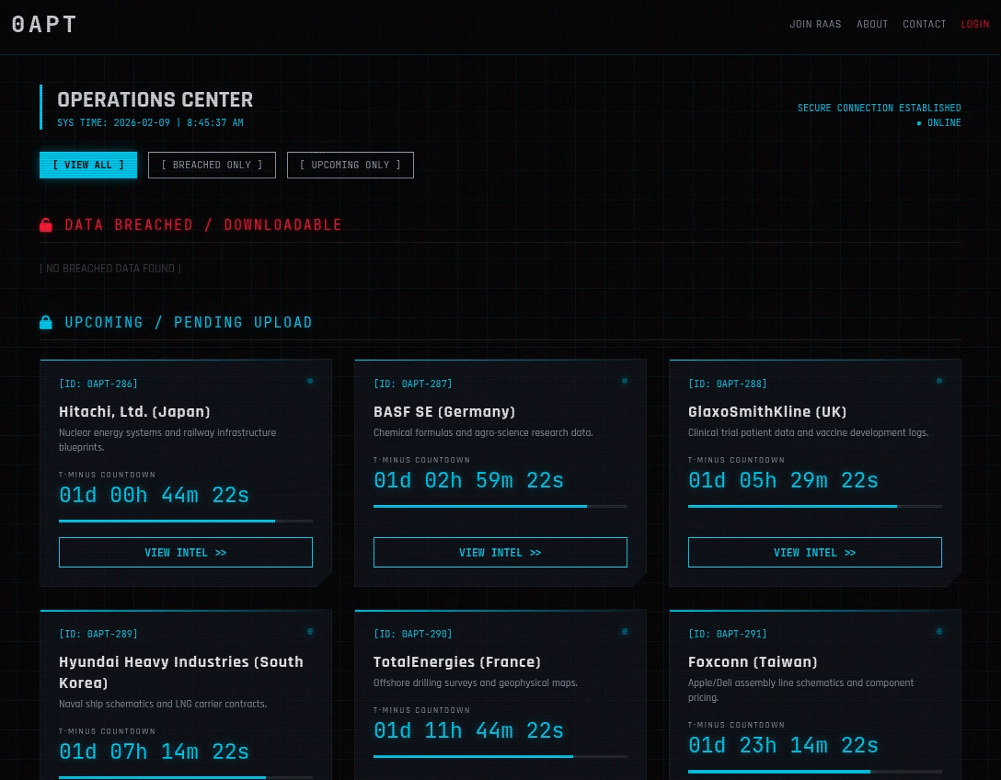
0APT’s “Data Leak Site” as of February 9, 2026
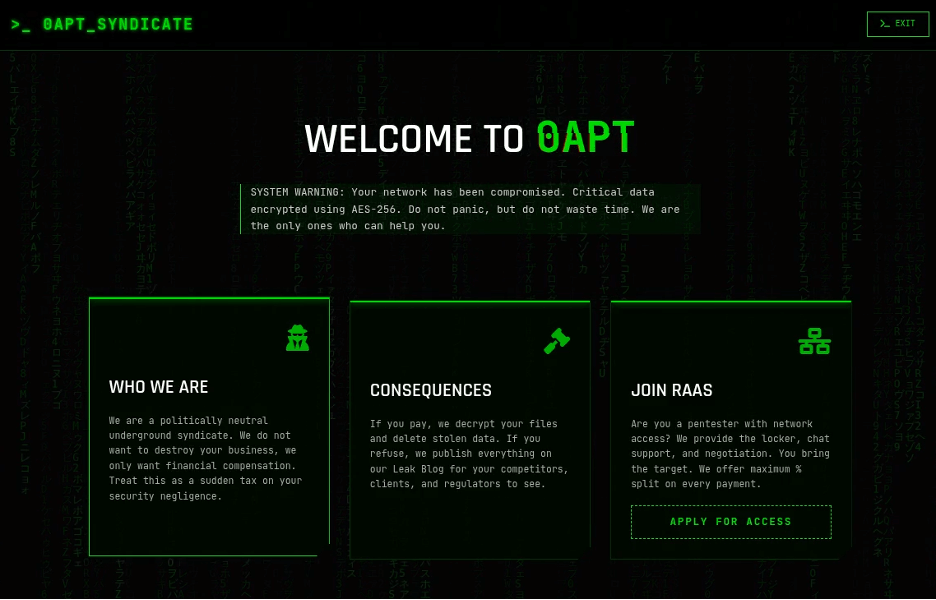
0APT’s “About” page referencing “0APT_SYNDICATE” as of February 9, 2026
0APT’s Data Leak Site (DLS) initially appeared as many such “normal” sites do. There is contact information, links to an affiliate program, and most importantly, victim tiles and details with countdowns until data is published, and presumably leaked data in the cases where victims have not paid. But this is where the similarities ended, and we observed the following oddities as we scrutinized further:
- The DLS initially featured several victim posts reflecting a status of “Payment Verified” or “Decryption Successful”. This is anomalous because one of the primary incentives for victims to pay a ransom is to prevent their publication or remove their names from a DLS. Keeping the victim name up, and even highlighting that they have paid, is more likely intended as a signal of group efficacy than representative of actual payment rates.
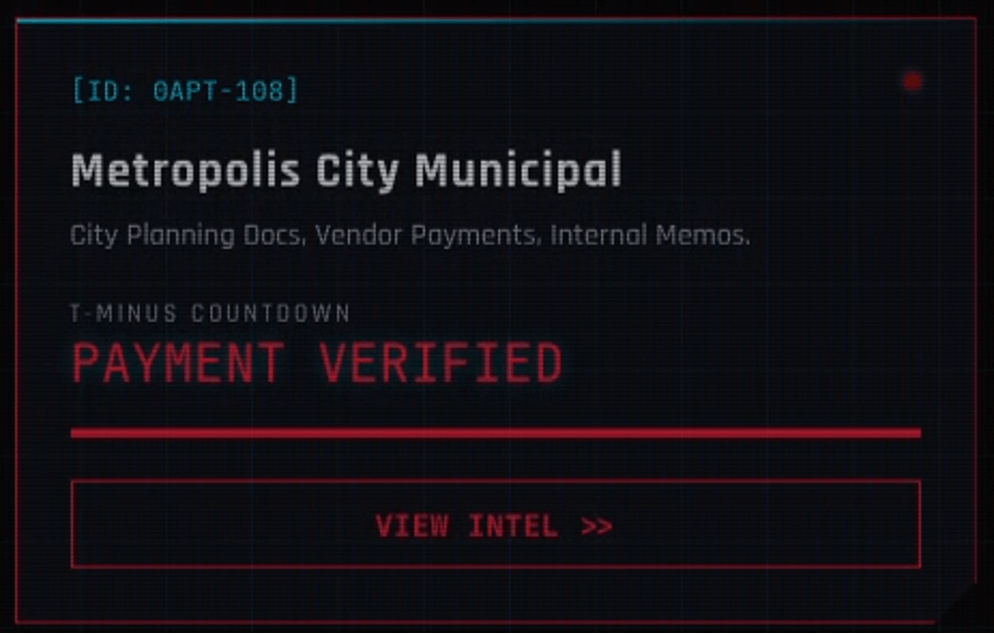
An earlier example of a “Victim” from 0APT’s page, reflecting “PAYMENT VERIFIED” status and a generic victim name
- While we did not download the posted victim data of any alleged victims for verification purposes out of respect for applicable laws, we noted that the evidence of “file trees” associated with multiple victims were extraordinarily large (>20GB) text documents where we would expect to see <10MB. Subsequent reporting from researchers in DataBreach highlighted the most likely explanation:
| The trick is simple, but it works. According to researchers who watched the traffic, the group’s servers are likely piping a stream of /dev/random (a standard computer tool for making random bits) straight into the user’s browser. This creates a solid illusion. To a network monitor, the jumble of data looks exactly like a massive, encrypted file. There are no “magic bytes,” the digital signatures at the start of a file that tell a computer it is looking at a ZIP or a PDF, to give the game away. Worse, the group masks the file size to look like hundreds of gigabytes. Because the Tor network is notoriously slow, an analyst can spend a week downloading what they think is a smoking gun, only to find they have spent days capturing a mountain of useless binary static. |
- Multiple amateur threat researchers and “OSINT” accounts on social media have reached the conclusion that 0APT is a “fabrication”, citing unverifiable and potentially AI-generated victim names peppered with real businesses, and the absence of evidence of ongoing or historical operations. However, several such accounts which trend towards attention-grabbing or AI-generated content continue to amplify the group’s alleged victim posts, which have since been updated by the threat actor to a more “believable” number of real organizations.
- In at least two instances of which GRIT is aware, alleged victims that have been claimed by the group experienced no intrusion at all following in-depth analysis and review. No ransom notes have been discovered and no direct communications with the victim were observed. By all indications, the claims of a breach by 0APT in these instances is entirely fabricated. GRIT is aware of no instances in which a posted victim experienced a recent or concurrent intrusion that could be attributed to “0APT.”
Historical Context
So, why go through all the hassle? There are a few plausible explanations, each of which we have observed in the past by similar fabulist “threat actors”:
- Defraud potential affiliates or cybercriminals by collecting application fees for entry to the RaaS program. Although 0APTs page has subsequently updated to allow for free applications for affiliates, earlier versions charged a 1BTC “security bond” for entry into the program. We observed similar behavior designed to defraud cybercriminals by the fabulist group “Mogilevich” in early 2024, which the actor subsequently admitted was a fraud all along:
“You may be wondering why all this, and now I’m going to explain everything you need. In reality, we are not a ransomware-as-a-service, but professional fraudsters… None of the databases listed in our blog were as true as you might have discovered recently. We took advantage of big names to gain visibility as quickly as possible, but not to fame [SIC] and receive approval, but to build meticulously our new trafficking of victims to scam… We don’t think of ourselves as hackers but rather as criminal geniuses, if you can call us that.”
The actor claimed to have defrauded interested cybercriminals out of at least $85,000.
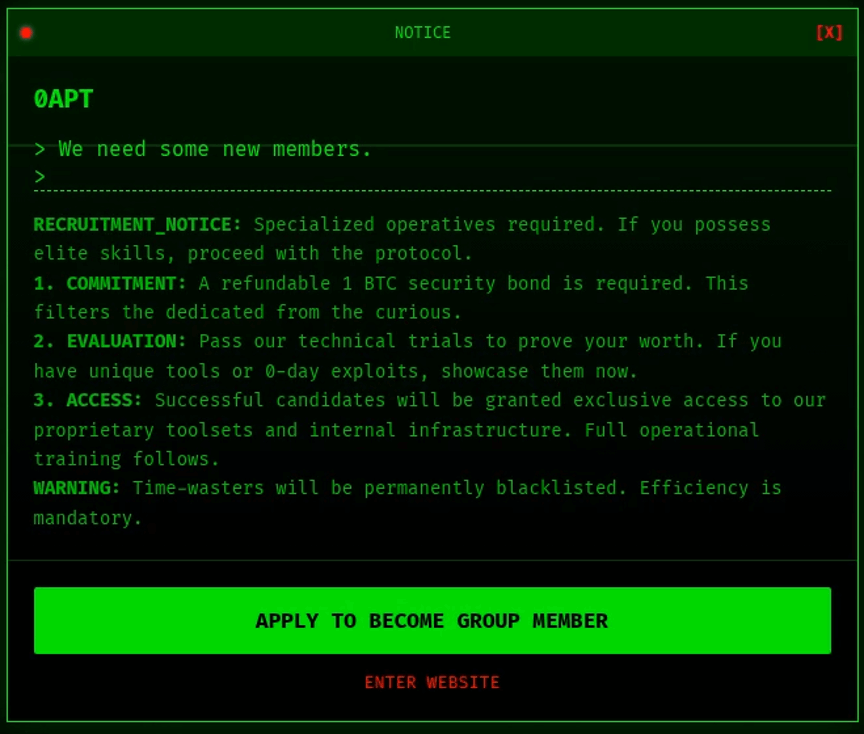
An earlier version of 0APT’s pop-up greeting advertising an affiliate program

A later version of 0APT’s pop-up greeting, reflecting free application
Extort alleged victims that are incapable of determining whether a breach had occurred or recycle historical breach data to “re-extort” victims. RansomedVC, a fabulist data extortion group, demonstrated similar behavior in 2023. In an excellent breakdown provided by security researcher Jon Dimaggio, scrutiny reveals that the threat actor behind the group, also known as RansomedSupport, “admits that some of their attacks are completely fabricated and that they even created fictitious data to deceive one of their victims in September 2023. In other situations, RansomedSupport bought stolen data, or stole it from other criminals.”
- Attract broad attention for later-stage operations or follow-on endeavors. We observed similar behavior from the fabulist group “FunkSec” in late 2024, which leveraged a rudimentary encryptor developed using AI/LLM tools to give credibility to a later data auction site (FunkBID) and forum site (FunkForum). None of these endeavors were assessed to have been particularly successful, having failed to attract a consistent or high volume of users. However, data sales and forum management were likely more aligned with the skills and capabilities of the underlying threat actor than full-blown ransomware operations.
Actions for Defenders
Although we assess that 0APTs operations to data have been fraudulent or fabulist in nature, we cannot rule out the possibility that the underlying threat actor could pose a risk to organizations in the future, whether through continued development or through partnerships with other threat actors. As such, GRIT recommends the following as actions and recommendations for Defenders:
- For organizations with internal Cyber Threat Intelligence capabilities, validation and corroboration of threat intelligence sources remains critical. Even after more than a week, some threat intelligence sources still proclaim 0APT as “an emerging sophisticated ransomware group,” potentially as the result of unchecked AI-generated content or poor internal quality control. All threat intelligence sourcing should be periodically validated by consumers for accuracy, timeliness, and actionability before being relied upon as a basis for internal decision-making.
- Compromised credentials remain the easiest, most prolific, and least alerting method of initial access for threat actors to gain access to a victim environment. Enforced phishing-resistant Multi-Factor Authentication (MFA), particularly in external-facing services such as VPNs, can significantly reduce the threat. Additionally, a litany of open-source and commercial tools are available to detect and respond to compromised credentials on the open internet and deep and dark web.
- In cases where less sophisticated actors gain access to target environments, their tactics, techniques, and procedures are typically rudimentary and rely on widely available tools rather than custom of novel malware and C2. Deployment of a reputable Endpoint Detection and Response (EDR) solution will aid in the rapid identification and containment of such behavior before adversaries have an opportunity to achieve their objectives, including ransomware deployment.
- If you suspect that an authorized party has gained access into your corporate network, we recommend activating your Incident Response retainer, or contacting the GuidePoint Digital Forensics and Incident response team for assistance.